Global Site
Displaying present location in the site.
NEC I:Delight — Personalized Adventures Unified by Trust
Among the many impacts of the COVID-19 pandemic has been the acceleration of existing trends towards the digitalization of society. These trends have triggered a change in lifestyles, work styles, and business styles, precipitating a shift towards a broader and more widely used range of online services, while hastening the integration of real and digital worlds. New ways of managing identities while coping with the risk of personal information leaks, fraudulent use, and privacy invasion are needed. NEC has developed a concept called NEC I:Delight, which is designed to address the issues described above. This paper introduces this high-value concept and illustrates the new view of the world it represents and the NEC Digital ID solution we are developing to achieve that world.
1. Introduction — The Changing Social and Economic Environment
The digitalization of society has changed the way people live, work, and do business. For example, new technology that connects touchpoints―which until recently have always been offline―via networks is triggering the creation of a burgeoning array of new services that integrate the real and digital worlds.
These trends have been massively accelerated by the COVID-19 pandemic which has forced people and businesses to dramatically alter the way they live, work, and do business, boosting existing online services and creating new ones. With social distancing and stay-at-home orders dominating the battle against COVID-19, new services that promote themselves with such buzzwords as “remote” or “no-contact” have popped up one after the other even in fields in which physical, in-person operations have been the norm. New online services are also being offered in various areas such as healthcare, education, labor, entertainment, and payment.
In societies where online services have progressed to this stage, service providers must be able to perform reliable online user identification and authorization based on the information provided by the users, as well as other permission and confirmation procedures upon use of the service. Three key themes have been identified that must be effectively managed in order to create a useful, high-functioning solution.
- Stricter management of personal information based on consent
- Compatibility between convenience and reliability
- Enhanced measures against risks of personal information leaks and unauthorized use
2. The World of NEC I: Delight
NEC I:Delight is an overarching concept aimed at solving the various issues that one can expect to occur in a society permeated by digitalization and where the “new normal” has literally become normal (Fig. 1).

NEC I:Delight is a concept that uses biometric authentication such as face or iris recognition as a universal ID, making it possible to offer users a consistent experience by connecting multiple touchpoints and services.
Seamless connection of services in various scenarios such as traveling, shopping, and commuting makes it possible to offer a safe, secure, and pleasant experience.
Personal information is essential for the services applicable to NEC I:Delight. When users consent to provide service providers with their personal information, they will be able to enjoy a unique experience carefully tailored to suit their tastes and preferences.
Rigorous security measures are applied in the management and use of the user’s personal data with appropriate rules to ensure safety and reliability.
3. NEC Digital ID Solution Achieves the World of NEC I:Delight
NEC Digital ID solution comprises a suite of technologies that support the concept of NEC I:Delight (Fig. 2).
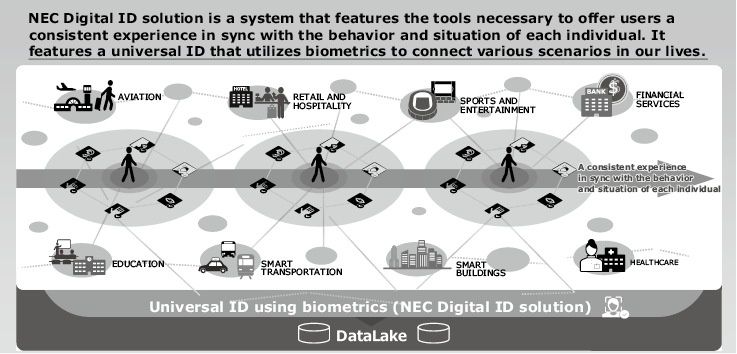
NEC Digital ID solution links biometric IDs and leverages personal data to connect various services that correspond to user needs and aspirations, making it possible to provide users with a seamless experience as they transit from one service to the next. NEC stands firmly by the fundamental belief that the individual retains sovereign power over their personal ID and data, and therefore requires their full consent in order to share and utilize their data.
NEC Digital ID solution offers value to both users and service providers.
- Improves user convenience by making multiple services accessible via biometric authentication.
- Increases efficiency and reduces labor requirements for customer service tasks using biometric authentication.
- Reduces the risk of leaks by securely managing personal information.
- Reduces the risk of identity theft and unauthorized use by using high-precision biometrics.
- Improves hygiene and reduces risk of infectious disease by providing touchless services.
- Uses personal data to improve the value of a service so that it more precisely meets the needs of users.
3.1 IoT Hospitality Cloud Service trial
In January 2019, we launched a trial in Nanki-Shirahama, Wakayama to show how our integrated digital solutions can enhance the tourist experience. On arrival at the local airport, visitors can register their facial information and subsequently enjoy various services–at hotels, commercial facilities, and sightseeing facilities―all without holding anything in their hands or using cash (Fig. 3).
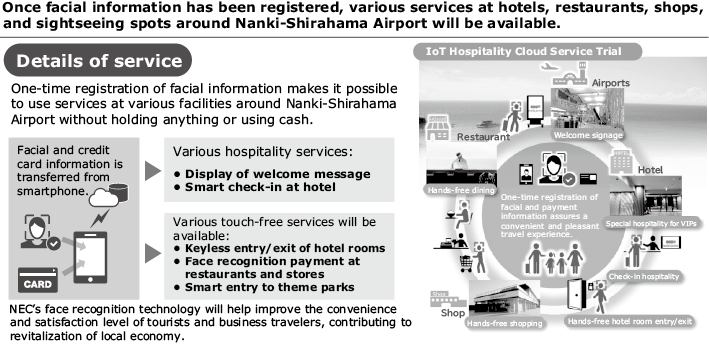
We are planning to continue this trial while increasing the number of the touchpoints and expanding the range of available services.
3.2 Trial at the NEC Super Tower — Digital workplace in the age of the “new normal”
Digitalization and COVID-19 have had a huge impact on the way many people work. This trial was initiated in July 2020 to test the efficacy of new digital offices at the NEC Super Tower in Minato-ku, Tokyo (Fig. 4).

With a view to improving the safety, productivity, and creativity of employees, we are testing out new work styles that combine telework with working from a traditional office. For example, we replaced employee ID cards with face recognition authentication, eliminating the need to carry an employee ID card to enter and exit work areas, use lockers, multifunction printers and vending machines, and have lunch at the cafeteria. In other words, instead of having to produce an ID card in various workplace scenarios, employees can access equipment or employee-only spaces in a convenient, touchless way, making office work safer and more efficient. Our challenge is to create new work styles that are at once comfortable and efficient, facilitating smooth communication between employees and between employee and customer.
4. The Cutting Edge Technologies behind NEC Digital ID Solutions
Central to the achievement of the world of NEC I:Delight, NEC Digital ID solution is built on two key functions―ID federation and data utilization. In the following section, we summarize the new technologies that make these functions possible.
The role of ID federation is to standardize service user authentication and authorization in multiple services. One of the values we hope to achieve with NEC Digital ID solution is walk-through authentication. Biometrics is the ideal tool to achieve this. To ensure that the walk-through authentication process is safe and pleasant, the biometrics must provide extremely high authentication precision.
No matter how accurate the authentication process is, the possibility of identity theft remains a risk. If pre-registered authentication data is stolen or tampered with, impersonation could occur. Hence, the protection of authentication data is as important as the precision of authentication.
Even if authentication information is secure, the authentication system could still be taken over by an attacker. If a malicious program is executed, this will interfere with authentication. Security of authentication terminals is equally important as authentication terminals in high-traffic locations such as airports and storefronts are likely to become targets for attack.
Data utilization complements ID verification by feeding personal information back to users as a new value. However, it is critical that the data be handled in such a way so as not to infringe the user’s privacy. To prevent this, it is important to obtain the free consent of the user after explaining to them why we need to use their data, how we will use it, and how we will protect it. Moreover, even if the user has given consent for their data to be used by the service, invasion of privacy can still occur if that data is stolen or tampered with. Thus, the protection of personal data is extremely important.
To sum up, to achieve ID federation and data utilization, the following four points are important.
- (1)Precision of authentication
- (2)Protection of authentication information and personal data
- (3)Security of authentication terminals
- (4)Safe handling of personal data in accordance with the user’s wishes
Among these, (4) should be dealt with in the design of the service itself. The others can be dealt with using common technologies not dependent on a specific service. These common technologies include the following.
Face and iris recognition: Contributes to the improvement of authentication accuracy. For ten straight years, NEC’s face recognition has held the number one spot in the benchmark tests conducted by the United States National Institute of Standards and Technology (NIST)1). To improve the authentication precision of this system, we combined it with our iris recognition system. Together, iris and face recognition offer an unprecedented level of authentication accuracy, helping to reduce the rate of mis-authentication to less than one ten-billionth. This high accuracy makes it possible to adapt NEC’s system to walk-through authentication in globally deployed services all over the world.
IoT terminal tampering detection: Contributes to the security of authorization terminal. If the authentication terminal is taken over, this technology makes it possible to detect and confirm the takeover by verifying the terminal from outside. This is effective even if the attacker attempts to disguise their attack by making it appear as if the terminal’s operating status is normal. This protects the server from attack via the hijacked terminal.
Secure terminal authentication: Contributes to the protection of authentication data. Smartphones and storefront authentication terminals may store the biometric data of the people who use their service. Unfortunately, these devices can be lost or stolen, increasing the risk of biometric information being stolen and the terminal being taken over. The secure terminal authentication technology prevents theft of data and makes it possible to perform biometric authentication on those devices safely.
Cancelable biometric authentication: Contributes to the protection of biometric data. If facial data is stolen, it used to be said it is impossible to reset the stolen data therefore the user cannot register their face again as a face recognition data. However, by storing the facial data with this cancelable biometric authentication system, the stolen data can be invalidated and the user can re-register their face. Moreover, once the re-registration is done, the stolen ID data can no longer be used.
Secure computation: Contributes to the protection of authentication data and personal data. This technology makes it possible to obtain computation results of the original data only, while preventing that data from leaking by using cryptographic techniques. Since there is no need to recover the data, data leakage can be comprehensively prevented.
Blockchain and secure multi-cloud storage: Contributes to the protection of personal data. The secure multi-cloud storage2) uses cryptographic techniques to make it difficult to leak data. When combined with blockchain, data tampering can also be prevented at the same time.
5. Conclusion
While we already possess the world’s leading biometric identification, we have no intention of resting on our laurels. We will continue to improve the accuracy and speed of ID federation using biometrics. At the same time, by promoting secure data utilization based on more secure management of personal data, we will continue to expand the range of applications for NEC Digital ID solution and maintain our commitment to the achievement of services that meet the needs of new lifestyles, new work styles, and new business styles.
Reference
Authors’ Profiles
Senior Expert
Digital Integration Division
Professional
Security Research Laboratories
Principal Researcher
Security Research Laboratories
 Ghassan KARAME, Wenting LI: Fortress: Secure De-duplicated Multi-Cloud Storage, NEC Technical Journal, Vol.10 No. 3, pp.114-117, July 2016
Ghassan KARAME, Wenting LI: Fortress: Secure De-duplicated Multi-Cloud Storage, NEC Technical Journal, Vol.10 No. 3, pp.114-117, July 2016
