Global Site
Breadcrumb navigation
Security
ICT PlatformsJune 30, 2022

Creating a Social System in Which People Can Live in Peace
Becoming a "provider of platforms that enable every system to be safely protected and continue to run normally." That is the very research vision put forth by NEC's security area. In the current era, social systems have become inseparable from ICT. NEC's various technologies are being broadly utilized in social infrastructure areas which support people's daily lives. We are advancing research and development on a daily basis with the goal of thoroughly managing cyber attacks, data leaks, and other risks to ensure the reliability of social infrastructure.
NEC's strengths include know-how accumulated through many years of involvement in social infrastructure and specialized knowledge in each area. The ability to create practical security systems that can be utilized in the field can perhaps be described as a unique characteristic of NEC. In addition, the company has had many research papers accepted by international conferences as it continues to send advanced technologies out into the world.
Utilizing Digital Twins and World-leading Encryption Technologies
NEC's research in the security area is currently pursuing the three themes of "system security," "data security," and "AI security." In system security, our goal is to build and operate secure systems utilizing digital twins. In data security, we are researching technologies that can utilize data that stays encrypted end to end while in AI security, we are advancing technology research to prevent attacks against AI.
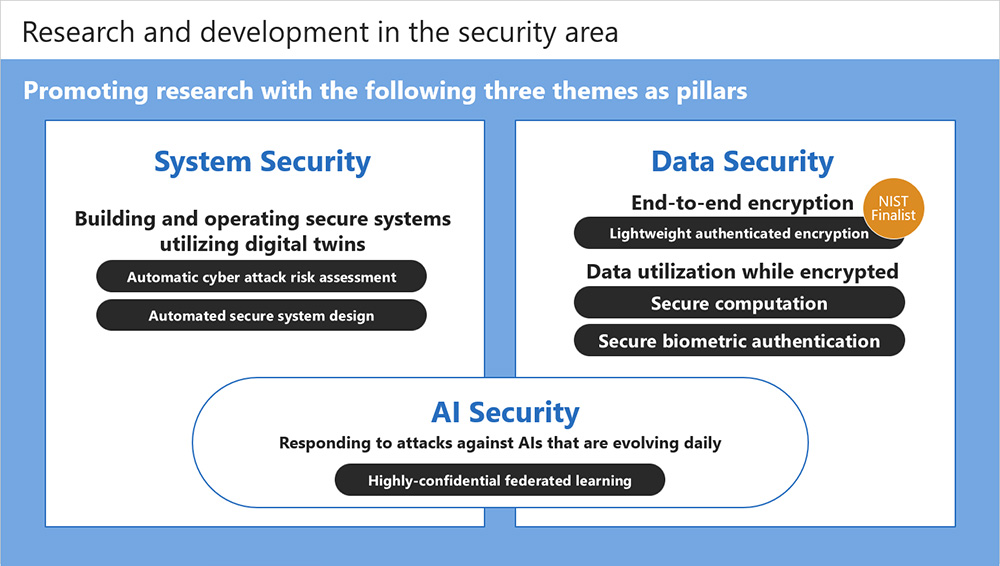
Primary research technologies
Technology for automatic cyber attack risk assessment
This technology builds a digital twin with respect to a system configuration to visualize vulnerabilities that can easily be abused and potential attack routes through simulation. We are digitizing the security assessment knowledge that NEC possesses as a database for simulation.
Person Re-identification Technology That Matches People Even If They Are Facing Away or Their Bodies Are Occluded

Automated secure system design technology
This technology automatically designs security-conscious systems and networks based on customer requirements. Converting the secure system design knowledge possessed by NEC into a database enables design without any dependence on individuals or examination omissions.
Lightweight authenticated encryption
This encryption technology can be utilized even in IoT sensors and other devices with limited CPU and memory resources. As a result, this guarantees end-to-end anonymity across the entire system. At NEC, we have developed encryption technologies which theoretically cannot be made any more lightweight. As of May 2022, this technology remains as a finalist in the NIST* international standardization competition.
*NIST: National Institute of Standards and Technology
World's Leading Symmetric-Key Cryptography Research:Kazuhiko Minematsu

Secure computation (Multi-party computation)
This technology secretly shares data among multiple servers to enable data analysis in a concealed state. NEC is leading the world in researching this technology and received the Best Paper award at ACM Computer and Communications Security 2016, a top international conference.
Secure computation technology for analyzing data with the information concealed

Secure biometric authentication (homomorphic encryption)
This technology recognizes biological features used in face recognition in an encrypted state to reduce the risk of leaking such personal information. In addition to the secret sharing method mentioned above, it also realizes a method using homomorphic encryption which does not require multiple servers.
Highly-confidential federated learning
This technology is compatible with both high security and analysis accuracy in federated learning which utilizes data between multiple organizations. By applying secure computation and attack simulation, it realizes attack-resistant learning with little accuracy degradation to eliminate the risk that the original data will be inferred from the AI model that is the learning result.