Global Site
Displaying present location in the site.
No. 2 (January 2018) Special Issue on Cybersecurity
Vol. 12 No. 2 (January 2018)
NEC has dealt with critical security issues on many occasions in the early stages and built advanced systems such as cyberattack defense mechanisms and information leakage prevention platforms. Before offering these systems to our customers, we have always first verified their effectiveness by implementing them ourselves. In recent years, we have been focusing on the enhancement of information, technology and human resources in order to strengthen our cybersecurity capabilities.
In this special issue, we will introduce our efforts to ensure cybersecurity and the solutions we have to offer to our customers, as well the cutting-edge technologies.
Special Issue on Cybersecurity
Remarks for Special Issue on Cybersecurity
SAKAI Kazuhiro
Executive Vice President, CIO and CISO
Developing Fundamental Solutions to Combat the Rise in Cybercrime: What role can a third-party all-Japan industry-academia-government organization play in containing the threat posed by cybercrime?
Akira Saka
Executive Director, Japan Cybercrime Control Center (JC3)

Random, elusive, and ever more widespread, cybercrime today has become a menace to ordinary citizens, governments, and businesses alike. Already hackers have stolen private financial and medical data from credit bureaus and health insurance companies, exposing millions of people to fraud, identity theft and worse. From targeted attacks to ransomware, cybercrime is everywhere and no one is safe. Growing concern about the danger these threats pose to society has led to increasing cooperation worldwide between industry academia and government to develop anti-cybercrime solutions at the most fundamental level. Established in November 2014 with the participation of private companies, universities, and the National Police Agency (NPA), the Japan Cybercrime Control Center (JC3) has already succeeded in exposing the activities of many criminal groups. We asked Mr. Akira Saka, the JC3’s executive director, about trends in cybercrime and how the organization is preparing to cope with them.
Trends in Cybersecurity and NEC’s Commitment to Developing Solutions
SUZUKI Mikio
Senior Expert, Business Creation Division
YAMAI Tadanori
Manager, Cyber Security Strategy Division
SUZUKI Tetsuya
Assistant Manager, Cyber Security Strategy Division
MIYAUCHI Kouji
Executive Chief Engineer, Security Research Laboratories
Over the past few years, cyberattacks and cybercrime have become increasingly destructive and are now regarded as a significant social issue. Under these circumstances, the Japanese government has hammered out a number of policies aimed at boosting cybersecurity both in the public and private spheres. At NEC, we take the threat of cyberattacks very seriously and have developed a variety of technologies such as a cyberattack protection system and information leakage measurement platform to protect our own security. Most recently, we have begun to apply AI technology to detect and counter threats and are working diligently to acquire security intelligence. Drawing on the technologies we have developed and the information we have collected, as well as sophisticated security human resources, NEC is now able to offer a wide spectrum of security solutions. In this paper, we will take a closer look at trends in cybersecurity and explain in some detail the efforts NEC is undertaking in this area.
Social trends & NEC’s approach
An Analysis of the Actual Status of Recent Cyberattacks on Critical Infrastructures
NOGUCHI Mutsuo, UEDA Hirofumi
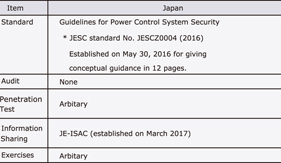
An increase in cyberattacks on critical infrastructures, especially on electric power systems, has been reported recently. It was previously thought that the risk of cyberattacks on critical infrastructures was low because of the need for specialist knowledge on the control system configuration and administrative operations as well as on the absence of suitable Internet connections. However, now that cyberattacks on critical infrastructures are exerting a significant impact on society, it has become necessary to reconfirm the risks by analysing the techniques used in such attacks. This paper references some cases of cyberattacks on electric power systems and discusses the issue of system administrations avoiding protective measures and thereby permitting attacks.
Latest Cyberattack Trends 2017 - Model Applying NEC Cyber Threat Intelligence -
ISODA Koji, KAKUMARU Takahiro
Traditional security measures have experienced difficulty in protecting against recent cyberattacks. This is because the attacks no longer consist of malware alone but have now acquired the capability of avoiding detection by the sophisticated use of management tools in their targeting systems. In order to deal with attack techniques that are continuing to advance, the use of Cyber Threat Intelligence (CTI) such as via cyberattack technique analysis, is currently attracting attention. This paper describes the cyberattack techniques recently discovered by using CTI.
The Measures Applied Internally by the NEC Group to Forestall and Prevent Cybersecurity Incidents
YOSHIDA Atsumasa
The NEC Group currently deploys proactive cybersecurity measures both inside and outside Japan in order to protect companies from the cyberattacks that are becoming increasingly sophisticated and advanced. Our security resources have been developed based on expertise accumulated over more than two decades, as well as on information sharing with external organizations including expert international security agencies and police forces. The group is also promoting the practical implementation of a system for localizing cyberattack damage by applying AI (Artificial Intelligence) and SDN (Software Defined Networking) technologies. This paper introduces the cybersecurity measures enhanced globally across the NEC Group, together with details of the existing information security infrastructure that the group is applying to protect customer information and other confidential data.
Cybersecurity solutions
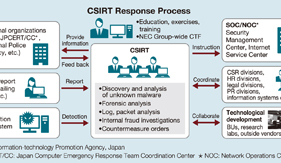
Security Operations Center (SOC) and Security Monitoring Services to Fight Complexity and Spread of Cyber Threats
ARIMATSU Tatsuhiko, YANO Yukiko, TAKAHASHI Yutaka
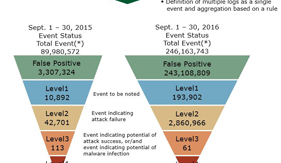
In answer to the spread and sophistication of cyberattacks, newly developed countermeasure products are achieving positive results and a certain level of success. However, many of them rely on the judgment abilities of the operators and due to the difficulties of their operations the current situation does not succeed in reducing damage satisfactorily. The security operations center (SOC) described below provides services with which professionals perform the required operations by substituting end users and is one that is currently attracting special attention in the field of cybersecurity. This paper describes the core issues that are currently being experienced and the innovative approach related to the SOCs and security monitoring services. It also gives a perspective on the desirable shape for the SOCs of the future.
Incident Response Solution to Minimize Attack Damage
OGUCHI Kyohei, YAMAZAKI Teru, YAMANE Masato
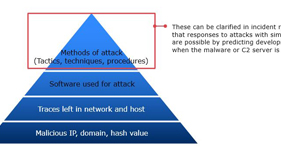
It is said that it is impossible to avoid security incidents no matter how many cyberattack countermeasures are taken. However, the possibility of mitigating the damage caused by cyberattacks depends greatly on the quality of the response taken initially, from immediately after the detection of an incident to a temporary calming down of the situation. This paper discusses the optimum form of the incident response to be taken, based on actual events. A first response support service provided by NEC is also introduced.
Enhancement of Incident Handling Capabilities by Cyber Exercise
YANO Yukiko, ITO Atsushi,
FUNAKOSHI Takeo, SATO Kazuyo

Under the intensification of threats of cyberattacks the refinement of human resources capable of handling them has become a pressing issue. NEC has been studying the skills expected from such human resources and the method of handling an actual cyberattack and thereby developing an effective training program. This paper introduces the concept of NEC in developing the practical cybersecurity exercises that are currently providing training courses, together with some actual cases.
Integrated Security Management/Response Solution – “NEC Cyber Security Platform”
ONODERA Hisato, YOSHIMOTO Masamichi, YAMAMOTO Kazuya
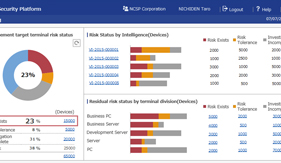
Damage caused by cyberattacks targeting the information systems of enterprises and public institutions have recently become a significant social issue. In order to counter the increase in the number of attacks, Defense in depth combining several countermeasures are now required. Defense in depth is composed of proactive measures as well as of threat detection and post-incident measures. The proactive measures include vulnerability management procedures consisting of steps that include; the assessment of equipment configuration information, assessment of vulnerability information, investigations/risk analyses of vulnerabilities and the enforcement of countermeasures. This paper discusses issues posed by these steps and also introduces a solution applied by NEC called “NEC Cyber Security Platform.”
Cloud-based File Encryption Service – ActSecure Cloud Secure File Service –
KAGEYAMA Tetsuya, SUZUKI Akio
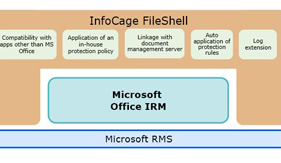
This paper introduces the Cloud Secure File Service. This is a SaaS service that encrypts the electronic files of an enterprise as a countermeasure against information leakages. The service is based on the InfoCage FileShell of file encryption software. It provides a management server function in the cloud environment and offers file encryption based on the DRM technology in collaboration with the Azure Information Protection service of Microsoft and the clients installed by the enterprise user. While previous systems specifically had freedom of customization but had to use labor in designing policy and building and operating a management server, this service is designed as enterprise user friendly by the strategy of offering the in-house operations knowhow of NEC and by providing a pre-built cloud environment.
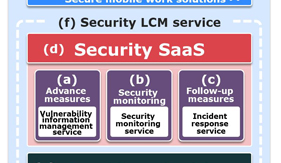
Security LCM Services
YAMAKI Tsuyoshi, SHIBATA Akira,
OHKOSHI Yoshihiko, KODAMA Jun
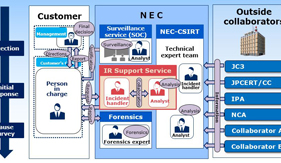
Under the threat of cyberattacks that are transforming themselves on a daily basis, many enterprises are now becoming incapable of dealing with the prevailing conditions. This is because they are required to adopt appropriate routine operations for preventing cyberattacks at the same time as preparing responses to possible security incidents by introducing security systems. To respond to such needs, NEC has started “Security LCM Services” that provide reliable services from consulting to construction and operation, while targeting the continuous improvement of customer cybersecurity measures. This paper introduces the LCM Services Security features and discusses the effects of their introduction.
Secure Mobile Work Solutions That Exploit EMM
OIKAWA Tsuyoshi, YOSHIDA Kazumi
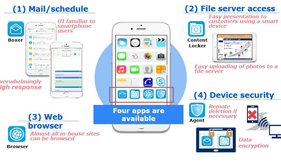
To promote the Work Style Reform proposed by Japan’s Abe administration, an ICT environment must be created that will allow people to work flexibly using various devices no matter where or when. However, it is expected that such a work style will increase the risk of cyberattacks, which makes sophisticated cyber-security critical to this endeavor. In this paper, we will discuss enterprise mobility management (EMM) solutions that ensure safe, reliable mobile work using smart devices. To illustrate how such a solution would work, we will review our own in-house case study, in which EMM was introduced at NEC.
Cybersecurity Consulting Services in the World of IoT
YOSHIFU Kenji, ITOH Mari, YAMADA Tomohide
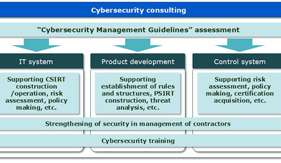
As IoT penetrates the fabric of our reality, transforming the way we live by dramatically increasing the efficiency of industry, improving the responsiveness of business, and enhancing the convenience of daily life, the threat posed by cyberattacks is becoming equally pervasive, posing huge risks to business and making it absolutely indispensable that management redouble its efforts to counter these attacks wherever they may strike, including their supply chains. In this paper, we take a look at the consulting services offered by NEC to help our customers implement appropriate security measures (in IT systems, product development, control systems, etc.) in management and manufacturing after making an assessment based on “Cybersecurity Management Guidelines” formulated by the Ministry of Economy, Trade and Industry (METI).
Applications of AI technology to cybersecurity
Countermeasures against Unknown Cyberattacks Using AI
NISHINO Shinichiro, KIDA Koji, KIZU Yoshiya,
YAGI Takashi, SAKAE Yoshiaki
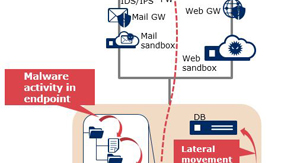
The spread and sophistication of cyberattacks have led to new issues when using existing security measures such as difficulty of detection. Even when detection is successful, advanced skills and a huge amount of manpower are required to analyze the results. NEC has dealt with these issues by developing a service designed to counter the unknown cyberattacks that used to be impossible to detect by applying AI technology. This service implements “detection” of unknown attacks over the entire attack process (from malware intrusion and the spread of infection inside a system to achievement of an attacker’s aim such as theft of data). After an attack “analysis” is also undertaken, thereby identifying the cause and extent of damage with a high degree of certainty. This paper introduces the current status and issues of cybersecurity, the base AI technology of the service, and its main functions and features, together with the results of the verification of how and how much the service solves the issues.
The Potential of AI to Propose Security Countermeasures
HOSOMI Itaru

As technology evolves, enhancing our lives in a myriad of ways, so too does its dark side. Today, cyberattacks are becoming ever more sophisticated and organized, and while the knowledge and experience of human analysts remains critical in preventing these attacks and developing effective, concrete counter-measures, cyberattack detection technology based on machine-learning AI is becoming increasingly effective. Recently, a number of startups in North America have developed machine-learning AI — such as those based on deep learning. In this paper, we will discuss the potential of logical inference AI as a tool for coping with the kind of complex, unformatted attacks that are expected to become prevalent in the future.
Detection, Auto Analysis of Cyber Threats Using Open Source Intelligence
KAWAKITA Masaru, SHIMA Shigeyoshi
Threat information such as cyberattack techniques and responsibility claims is distributed via social media and the deep web. However, the explosion of information and an insufficiency of security analysts make it difficult to detect such information at an early stage. This causes the problem of delayed preparation against attack damage. This paper introduces an automated proactive attack prevention technology that employs a technical analysis technique used in financial engineering to identify signs that a threat trend is reaching a peak. At the same time deep learning is employed to analyse the overall evidence of a cyberattack.
Cyber-Physical Integrated Analysis Technology for Criminal Investigation Support
TANI Masahiro

Cyberspace is the new frontier and like any frontier it is plagued by lawlessness. Criminals of all types from teenage pranksters to organized crime and even terrorists roam the virtual spaces of the online world wreaking havoc on individuals, businesses and governments alike. The problem is one that cannot be ignored and requires immediate attention from law enforcement entities around the world. What makes cybercrime especially intractable is that it can be extraordinarily difficult to identify the individuals and groups perpetrating these crimes — particularly since they can be located anywhere in the world and may be launching attacks using servers that are located in yet another jurisdiction. Developing simple countermeasures is no easy task, taking proactive measures is even more difficult. In this paper, we take a look at one of NEC’s current projects aimed at dealing with this problem, which involves building a system that can perform integrated analysis by extracting information useful for criminal investigations from the massive amount of data in cyberspace and applying biometrics including face recognition and object recognition technologies, as well as various analysis technologies.
In-house efforts provide safety and security for customers
Efforts to Provide Safe, Secure Products and Services for Customers – Secure Developments/Operations –
ISHIHARA Junji, NAKAMURA Masahide, IMOSE Atsuko,
OOSAWA Kumiko, HAYASHI Hidefusa
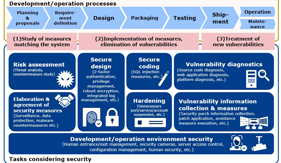
Both society and the commercial environment are shifting significantly toward the digital world. All of the devices connected to the Internet now have the potential of becoming the targets of cyberattacks. In such a setting, the NEC Group is making every effort toward securing developments/operations based on the concept of “security by design” that aims at the provision of safe, secure products and services in support of customer businesses. The quality of security is safeguarded by means of risk assessments that match the characteristics of each customer system and of efficient vulnerability responses, applied via precisely tailored management systems. This paper introduces the specific effects of secure development/operation and of future perspectives.
Talent Management: Managing Cybersecurity Human Resources
MINEGISHI Makoto

For several years now, NEC has been actively working to augment cybersecurity human resources. These efforts include promoting the expansion/deployment of training programs, improving the NEC Certified Professional (NCP) system, and encouraging the acquisition of certifications such as Certified Information Systems Security Professional (CISSP) and Registered Information Security Specialist (RISS). In this paper, we will review these policies and discuss our “talent management” program, that is, how we manage our cybersecurity human resources at the NEC Group including management of career paths and human resource exchanges.


 PDF
PDF