Global Site
Displaying present location in the site.
March 24th, 2022
Machine translation is used partially for this article. See the Japanese version for the original article.
Introduction
We tried to build an HA cluster across different regions using Amazon VPC peering (hereinafter called "VPC peering") on Amazon Web Services (hereinafter called “AWS”). VPC peering is a networking connection that allows private traffic to be routed between two VPCs.
VPC peering supports inter-region VPC peering, which enables private connections not only between VPCs in the same region but also them in different regions.
This time, we build an HA cluster that across N.Virginia and Singapore regions using inter-region VPC peering.
Contents
1. What is Amazon VPC peering?
VPC peering is a feature that enables private communication between two different VPCs.
In the past, when building a DR cluster on AWS, it was necessary to establish a VPN connection on the user side, such as setting up a software router individually. By using VPC peering connections, it is possible to connect easily VPCs privately as a function provided by AWS.
 Connect VPCs with VPC peering
Connect VPCs with VPC peering 2. HA Cluster Configureation
This time, we will build an "HA cluster based on DNS name control".
The configuration is as follows.
An "HA cluster based on DNS name control" uses AWS DNS resource. For more information about AWS DNS resources, please refer to  here.
here.
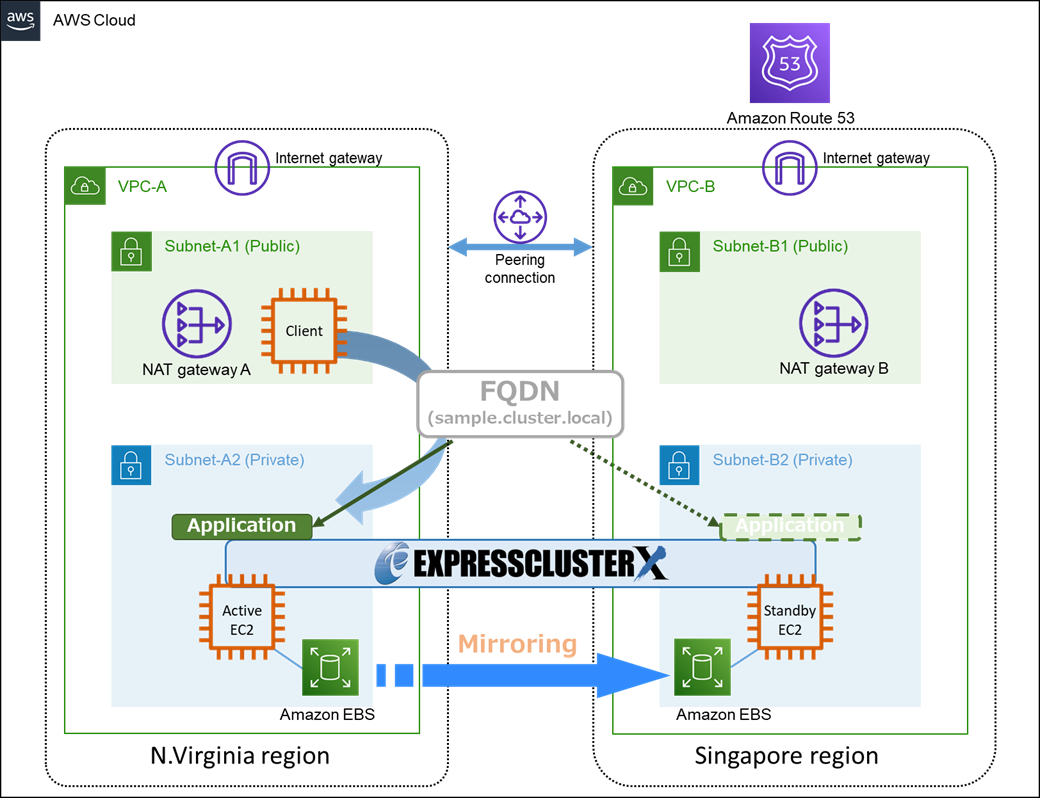
3. HA Cluster Building Procedure
3.1 Preparation for HA Cluster Construction
3.1.1 VPC Settings
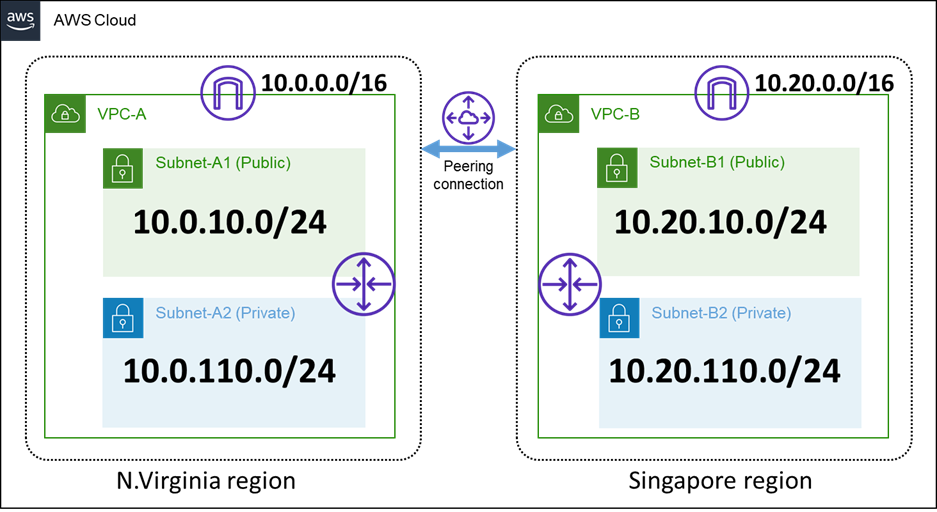
Create a VPC in advance. The configuration of VPC for each region is as follows:
- * For routes to VPC peering connections, add them after you create a VPC peering connection in 3.1.2 VPC Peering Connection Setting.
- VPC(VPC ID:vpc-1234abcd)
-CIDR:10.0.0.0/16
-Subnets
■Subnet-A1 (Subnet ID : sub-1111aaaa) : 10.0.10.0/24
■Subnet-A2 (Subnet ID : sub-2222aaaa) : 10.0.110.0/24
-RouteTables
■Main (Route table ID : rtb-00000001)
>10.0.0.0/16 → local
>0.0.0.0/0 → igw-1234abcd (Internet Gateway)
>10.20.0.0/16 → pcx-1234abcd (VPC Peering) *Set after creating VPC peering connection
■Route-A (Route table ID : rtb-0000000a)
>10.0.0.0/16 → local
>0.0.0.0/0 → eni-1234abcd (NAT Gateway ID for NAT Gateway A)
>10.20.0.0/16 → pcx-1234abcd (VPC Peering) *Set after creating a VPC peering connection
- VPC(VPC ID:vpc-5678efgh)
-CIDR:10.20.0.0/16
-Subnets
■Subnet-B1 (Subnet ID : sub-1111bbbb) : 10.20.10.0/24
■Subnet-B2 (Subnet ID : sub-2222bbbb) : 10.20.110.0/24
-RouteTables
■Main (Route table ID : rtb-00000002)
>10.20.0.0/16 → local
>0.0.0.0/0 → igw-5678efgh (Internet Gateway)
>10.0.0.0/16 → pcx-1234abcd (VPC Peering) *Set after creating VPC peering connection
■Route-B (Route table ID : rtb-0000000b)
>10.20.0.0/16 → local
>0.0.0.0/0 → eni-5678efgh (NAT Gateway ID for NAT Gateway B)
>10.0.0.0/16 → pcx-1234abcd (VPC Peering) *Set after creating a VPC peering connection
Also, set up security groups. The details of the security groups used in each region are as follows:
N. Virginia Region- Security Group
-Security Groups
■default-A (Security group ID: sg-00000001)
>Inbound rules:
・Type: All traffic
・Protocol: All
・Port range: All
・Source: sg-00000001
■SG-VPCPeering-A (Security group ID: sg-0000000a)
>Inbound rules:
・Type: All traffic
・Protocol: All
・Port range: All
・Source: 10.20.0.0/16 ← CIDR at vpc-5678efgh
- Security Group
-Security Groups
■default-B (Security group ID: sg-00000002)
>Inbound rules:
・Type: All traffic
・Protocol: All
・Port range: All
・ Destination: sg-00000002
■SG-VPCPeering-b (Security group ID: sg-0000000b)
>Inbound rules:
・Type: All traffic
・Protocol: All
・Port range: All
・Source: 10.0.0.0/16 ← CIDR at vpc-1234abcd
 Documentation – Setup Guides
Documentation – Setup Guides- Windows > Cloud > Amazon Web Services > EXPRESSCLUSTER X 4.3 for Windows HA Cluster Configuration Guide for Amazon Web Services
3.1.2 VPC Peering Connection Settings
Create a VPC peering connection to connect the VPC in the N.Virginia region and the VPC in the Singapore region. After you create a VPC peering connection, configure a route table.
- VPC (requester): vpc-1234abcd ← VPC ID in N.Virginia region
- VPC (accepter): vpc-5678efgh ← VPC ID in Singapore region
3.1.3 DNS Settings
Configure Amazon Route 53 to build an HA cluster based on DNS name control.
- Domain Name: local
- Hoted Zone ID: 123456789abcde
- Type: Private Hosted Zone for Amazon VPC
- Associated VPCs: vpc-1234abcd、vpc-5678-efgh
3.1.4 IAM Settings
Configure IAM as the permission setting for running AWS DNS resources.
Allow the following actions in the IAM role policy in order to retrieve and update information about the resource record set settings for Amazon Route 53:
"route53:ListResourceRecordSets"
3.1.5 Creating EC2 Instances
Create EC2 instances (active and standby) that will constitute the HA cluster in each region.
Set up security groups to allow connections from different regions.
- Active EC2
- -Security Group: default-A、SG-VPCPeering-A
- Standby EC2
- -Security Group: default-B、SG-VPCPeering-B
3.2 Creating HA Cluster Based on DNS Name Control
Create an "HA cluster based on DNS Name control". Configuration of EXPRESSCLUSTER is below. In the failover group of EXPRESSCLUSTER, we will register three resources: "AWS DNS resource", "Mirror Disk resource", and "CIFS resource".
First, register AWS DNS resources and mirror disk resources.
For more information about procedure to build an HA cluster based on AWS DNS resources, see the Configuration Guide for AWS.
- EXPRESSCLUSTER
- -Failover Group (failover)
- ■ AWS DNS Resource
・ Hosted Zone ID: 123456789abcde ← Hosted Zone ID set in "3.1.3 DNS Settings"
・ Resource Record Set Name: sample.cluster.local. - ■ Mirror disk Resource
・ Data partition Drive Letter: M:
・ Cluster partition Drive Letter: R:
-
- ■CIFS Resource
- ・Share Name: cifs_sharing_name
・Folder: M:\cifs_folder
-
 Documentation – Setup Guides
Documentation – Setup Guides- Windows > Cloud > Amazon Web Services > EXPRESSCLUSTER X 4.3 for Windows HA Cluster Configuration Guide for Amazon Web Services
> Chapter 7 Constructing an HA cluster based on DNS Name control
4. Checking the Operation
Confirm that CIFS resources are sharing files between different regions.
- 1. Create a test.txt under “M:\cifs_folder” on the active EC2 instance in N.Virginia region.
- 2. Access “\\sample.cluster.local\cifs_sharing_name” from the client EC2 instance and enter the ID and Password of the active EC2 instance to pass the authentication.
- Confirm that test.txt is displayed and you can open it with an editor.
- 3. Move manually the failover group from the active EC2 instance in the N.Virginia region to the standby EC2 instance in the Singapore region on the Cluster WebUI.
- 4. Open “\\sample.cluster.local\cifs_sharing_name” from the client EC2 instance and enter the ID and Password of the standby EC2 instance to pass authentication. Confirm that the test.txt file appears as it did before the manual failover and that you can open it with an editor.
We have confirmed that HA clusters can be built in environments that cross different regions.
Conclusion
This time, We tried to build an HA cluster across different regions using VPC peering connections.
The VPC peering connection is a bit complicated in terms of setting up the route table and security groups, but we think it is an attractive feature provided by AWS that allows you to easily achieve a private connection.
If you consider introducing the configuration described in this article, you can perform a validation with the  trial module of EXPRESSCLUSTER. Please do not hesitate to contact us if you have any questions.
trial module of EXPRESSCLUSTER. Please do not hesitate to contact us if you have any questions.
