Global Site
Displaying present location in the site.
September 28th, 2021
Machine translation is used partially for this article. See the Japanese version for the original article.
Introduction
Using AWS Transit Gateway (hereinafter called “Transit Gateway”), we tried connecting to an HA cluster based on VIP control, which was built on Amazon Web Services (hereinafter called “AWS”).
Transit Gateway is a service that allows Amazon Virtual Private Cloud (hereinafter called “VPC”) and on-premises networks to connect to a single gateway.
VPN connection from your on-premises environment to VPC, VPC Peering connection, and more can be realized with a single gateway.
For using AWS DNS resources to connect to HA clusters on AWS from on-premises environments, refer to  this article.
this article.
Contents
1. What is Transit Gateway?
Transit Gateway is a service that allows VPCs and on-premises networks to connect to a single gateway, as mentioned above.
If you do not use a Transit Gateway, peering connections between multiple VPC environments, or VPN connections between on-premises and multiple VPC environments, require more complex configuration as the number of VPCs increases.
By using Transit Gateway, it is very simple to build the environment.
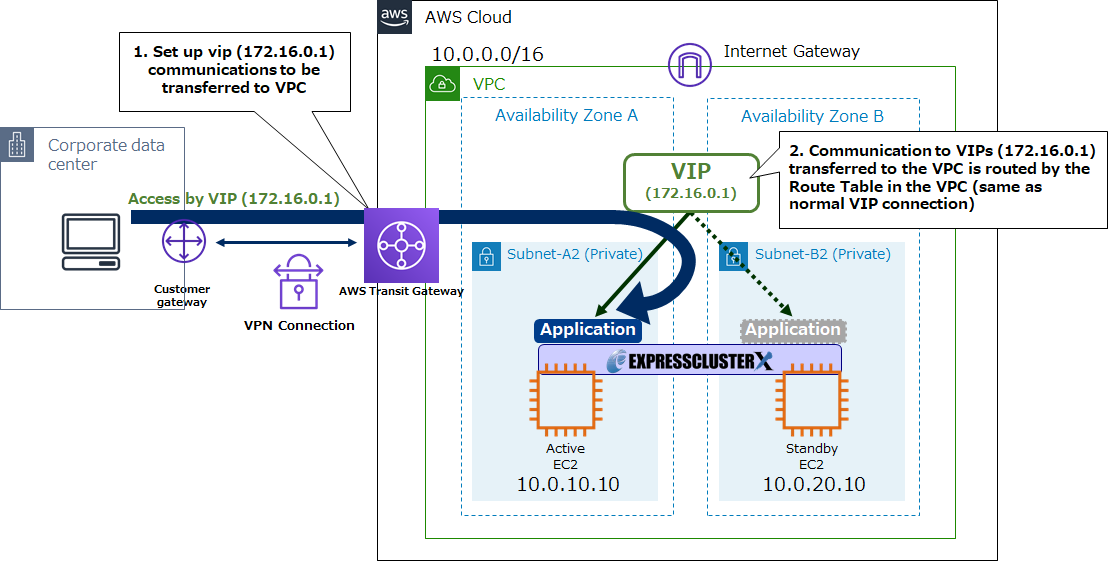
Transit Gateway routing settings combined with HA cluster based on VIP control enable connections to VIPs from outside the VPC, such as on-premises environments.
 AWS Transit Gateway
AWS Transit Gateway 2. HA Cluster Configuration Based on VIP Control
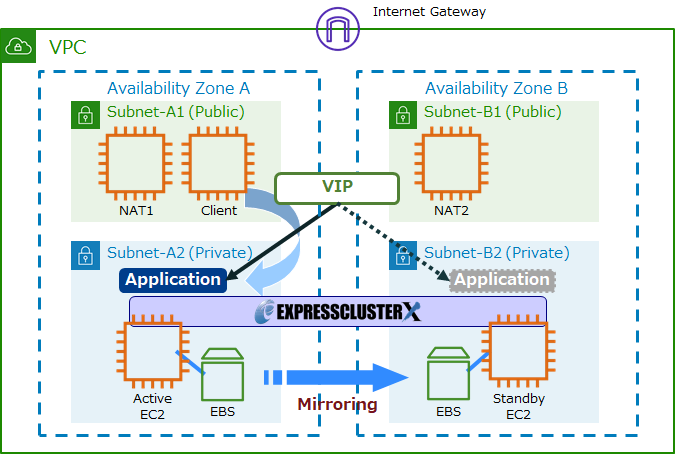
The following figure shows an HA cluster configuration using AWS Virtual IP resources.
AWS Virtual IP resource is a resource that enables the use of virtual IP addresses on AWS. It enables the reassignment of virtual IP addresses by changing the route table settings and assigning IP addresses to the OS.
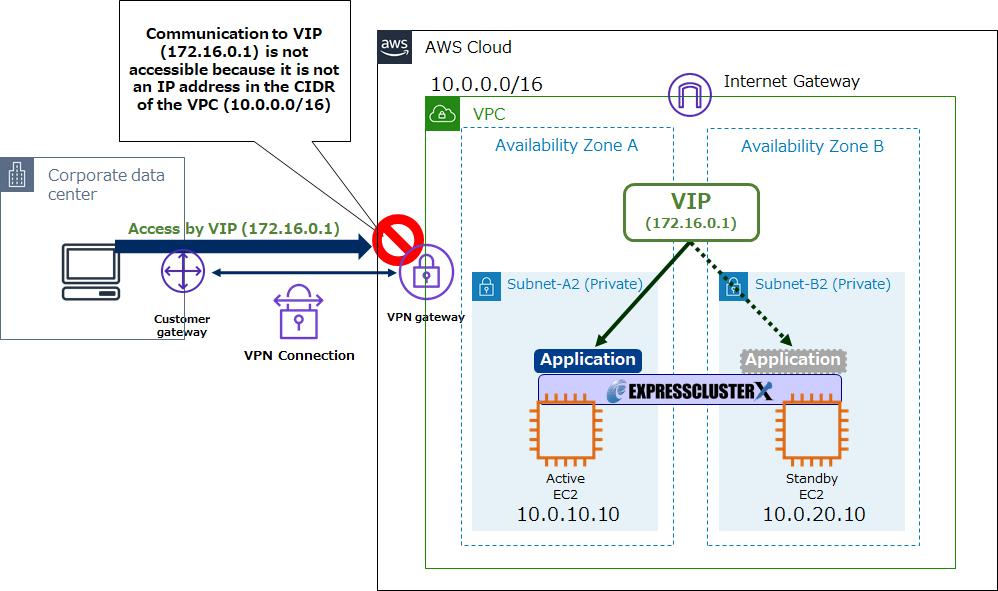
However, without Transit Gateway, there is a limitation that users can not connect to HA clusters in VPC environments from on-premises environments via VIPs.
By configuring a VPN connection using Transit Gateway and configuring communication to the VIP to VPC in transit gateway routing settings, it is possible to connect VIP from the on-premises environment to the HA cluster in the VPC environment.
3. HA Cluster Configuration
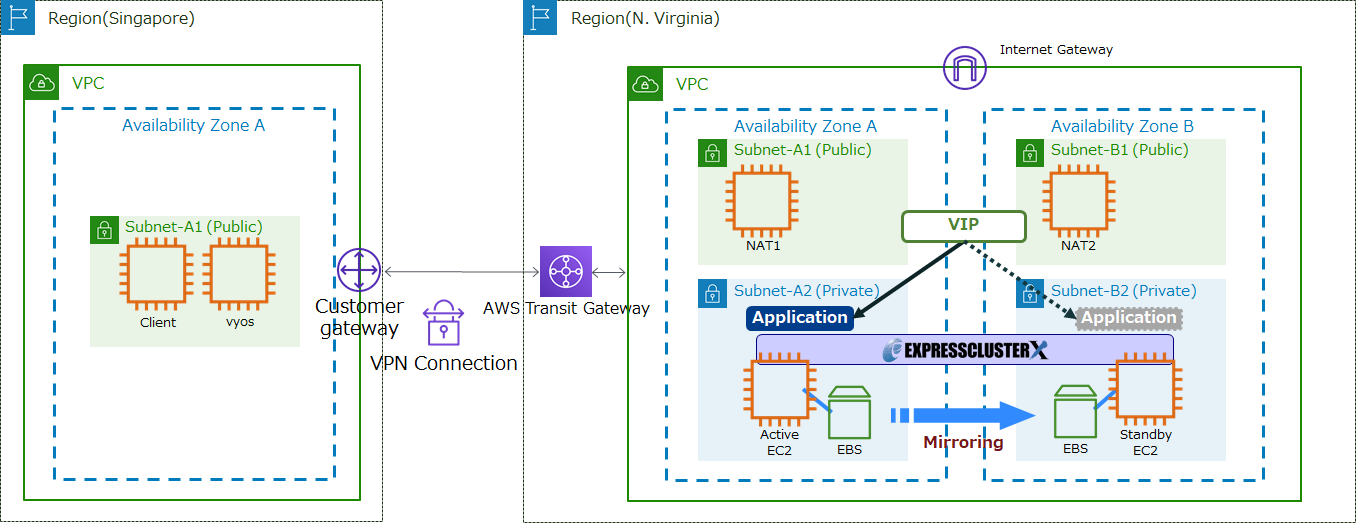
This time, we will build a "HA cluster based on VIP control" in the VPC environment in the N. Virginia region.
As a pseudo-environment for on-premises environments, we build client machines in the Singapore region and connect VPC in the Singapore and N. Virginia regions with a VPN.
* If you are actually connecting from an on-premises environment, please replace the following Singapore regions with on-premises environment.
The configuration is as follows.
4. HA Cluster Building Procedure
Build a "HA cluster based on VIP control".
4.1 Building HA Cluster Based on VIP Control
4.1.1 Preparation for HA Cluster Building
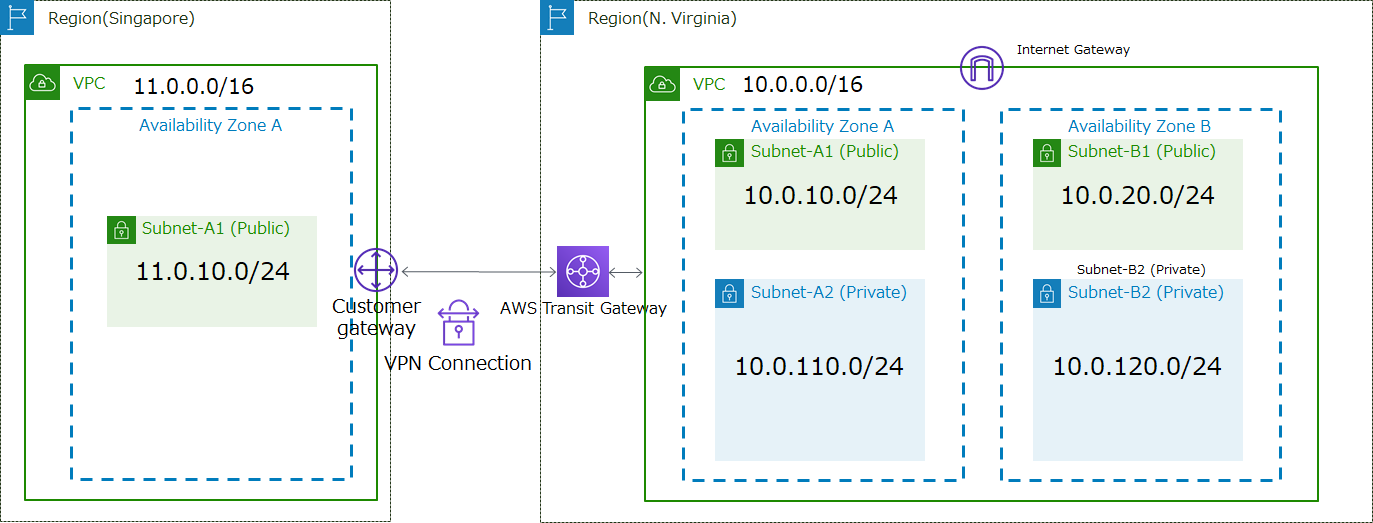
Create VPCs in advance. The configuration of the VPCs is as follows.
N. Virginia Region
- VPC (VPC ID : vpc-1234abcd)
- - CIDR:10.0.0.0/16
- - Subnets
- ■ Subnet-A1 (Subnet ID : sub-1111aaaa) : 10.0.10.0/24
- ■ Subnet-A2 (Subnet ID : sub-2222aaaa) : 10.0.110.0/24
- ■ Subnet-B1 (Subnet ID : sub-1111bbbb) : 10.0.20.0/24
- ■ Subnet-B2 (Subnet ID : sub-2222bbbb) : 10.0.120.0/24
- VPC (VPC ID : vpc-5678cdef)
- - CIDR:11.0.0.0/16
- - Subnets
- ■ Subnet-A1 (Subnet ID : sub-1111cdef) : 11.0.10.0/24
 Documentation - Setup Guides
Documentation - Setup Guides- Windows > Cloud > Amazon Web Services
- Linux > Cloud > Amazon Web Services
4.1.2 Building HA Cluster Based on VIP Control
Build a "HA cluster based on VIP control". EXPRESSCLUSTER consists of the following:
Register two resources in the failover group of EXPRESSCLUSTER, AWS Virtual IP Resource and Mirror Disk Resource.
For more information about how to build an HA cluster using AWS Virtual IP resources, refer to the Configuration Guide.
* No special cluster configuration is required to work with Transit Gateway.
- EXPRESSCLUSTER
- - Failover group
- ■ AWS Virtual IP resource
- > IP Address : 172.16.0.1
- > VPC ID : vpc-1234abcd
- ■ Mirror Disk resource (Windows)
- > Data Partition : M:\
- > Cluster Partition : R:\
- ■ Mirror Disk resource (Linux)
- > Data Partition : /dev/xvdb2
- > Cluster Partition : /dev/xvdb1
 Documentation - Setup Guides
Documentation - Setup Guides- Windows > Cloud > Amazon Web Services
- Linux > Cloud > Amazon Web Services
4.2 Creating Transit Gateway
Create a Transit Gateway and connect the N. Virginia and Singapore regions with a VPN. The flow of the settings is as follows.
- 1.Creating Transit Gateway
- 2.Creating Transit Gateway Attachment for VPN
Select a VPN for The Attachment Type and create a Transit Gateway Attachment to connect to the Singapore region via VPN. - 3.Setting vyos
Put the settings into vyos in the Singapore region and enable vpn connection. - 4.Creating Transit Gateway Attachment for VPC
Select VPC for Attachment Type and create a Transit Gateway Attachment to connect to the VPC in the N.Virginia region. - 5.Setting Transit Gateway Route Table
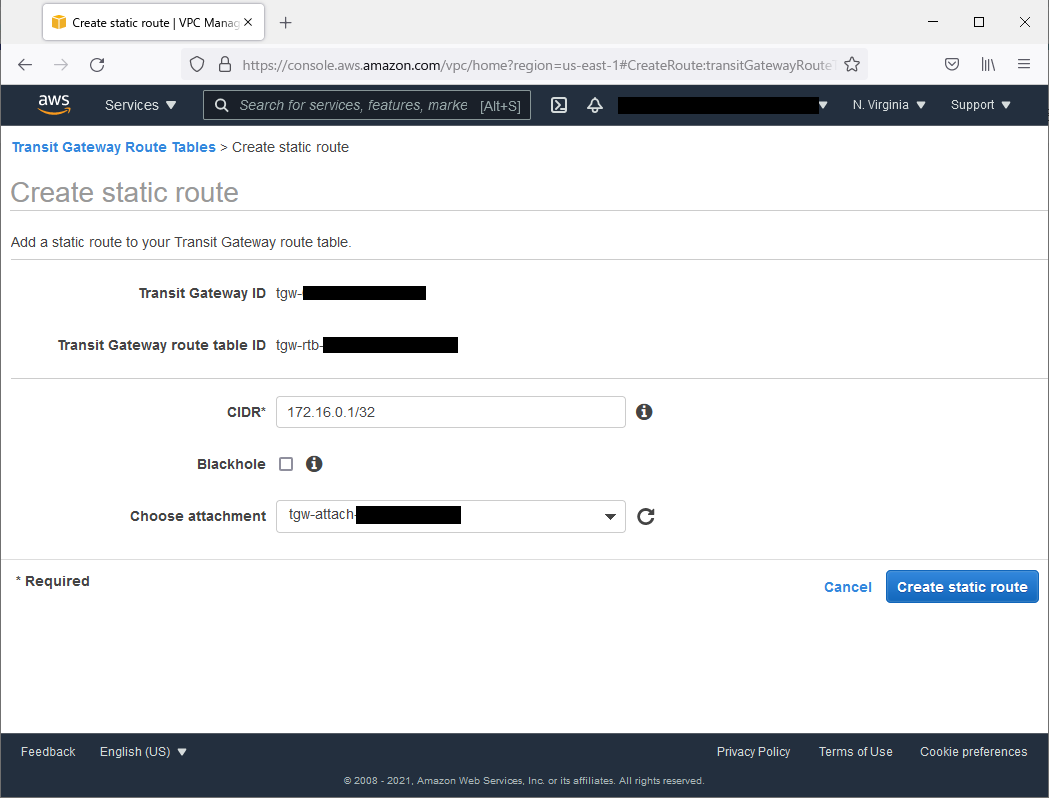
Add a VIP path to the Transit Gateway Route Table.
4.2.1 Creating Transit Gateway
Create a Transit Gateway.
This time, we're creating all of the settings by default.
The procedure for creating Transit Gateway was referred to the following site.
 Transit gateways
Transit gateways 4.2.2 Creating Transit Gateway Attachment for VPN
Select a VPN for the Attachment Type and create a Transit Gateway Attachment to connect to the Singapore region via VPN.
By creating a Transit Gateway Attachment, a VPN connection is created together.
The procedure for creating a Transit Gateway Attachment for VPN was referred to the following site.
 Transit gateway VPN attachments
Transit gateway VPN attachments 4.2.3 Setting vyos
Download the configuration information from the VPN connection created.
Enter the settings vyos in the Singapore region to enable the VPN connection.
In addition, add a configuration to vyos so that VIP (172.16.0.1) communication is routed to the Transit Gateway.
4.2.4 Creating Transit Gateway Attachment for VPC
Select VPC for Attachment Type and create a Transit Gateway Attachment to connect to the VPC in the N. Virginia region.
The procedure for creating a Transit Gateway Attachment for VPC was referred to the following site.
 Transit gateway attachments to a VPC
Transit gateway attachments to a VPC 4.2.5 Setting Transit Gateway Route Table
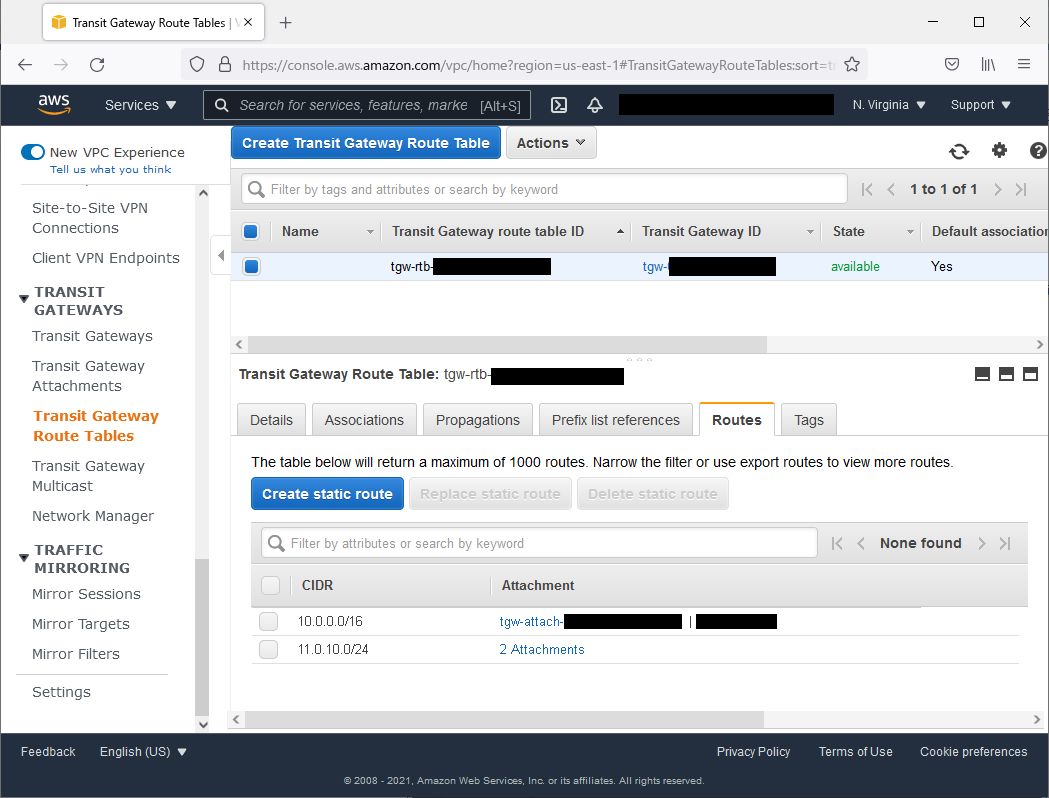
Add settings to the Transit Gateway Route Table.
Create settings so that VIP (172.16.0.1) communications are routed to the VPC (10.0.0.0/16) in the N. Virginia region.
5. Checking the Operation
Verify that the client machine can access the active EC2 instance using VIP (172.16.0.1).
- 1.Start failover groups on the active EC2 instance.
- 2.Verify that you can access the VIP (172.16.0.1) from a client machine in the Singapore region and connect to the active EC2 instance.
- 3.From Cluster WebUI, manually move the failover group from the active EC2 instance in the N.Virginia region to the standby EC2 instance.
- 4.Verify that you can access the VIP (172.16.0.1) from the client machine in the Singapore region and connect to the standby EC2 instance.
Conclusion
This time, we tried connecting to an HA cluster based on VIP control built on AWS using Transit Gateway.
We think that it is a very easy-to-use configuration because the HA cluster configuration can be connected from the on-premises environment as before.
The existing HA cluster based on VIP control can also be applied without changing the HA cluster settings, so please try it.
If you consider introducing the configuration described in this article, you can perform a validation with the  trial module of EXPRESSCLUSTER. Please do not hesitate to contact us if you have any questions.
trial module of EXPRESSCLUSTER. Please do not hesitate to contact us if you have any questions.

 Lerger view
Lerger view