Global Site
Displaying present location in the site.
Biometric Authentication Leading the Way to the Future
Advanced Technologies and Methodologies Supporting DX OfferingsBiometric authentication is used every day by people around the world. By linking biometric authentication to all types of digital services in the future, we might be able to provide optimized services for individuals. The role of non-contact biometrics is becoming increasingly important as society shifts to one of non-contact interaction because of the novel coronavirus infection (COVID-19). In the benchmark tests conducted by the National Institute of Standards and Technology (NIST) held in 2021, NEC’s biometric technology ranked first in the world in two categories: non-contact face recognition and iris recognition. This article introduces the features of NEC’s technology for both face recognition and iris recognition that support our DX offerings, multimodal authentication that combines both of NEC’s winning technologies, and possible applications using the core technologies of face recognition.
1. Introduction
Biometric authentication is routinely used by people worldwide. Unlocking smartphones is one of the most familiar examples of using biometrics, but biometric authentication is also used in many other situations such as when people enter or leave offices and condominiums, open bank accounts, or make payments. In the future, through biometrics playing a central role in linking digital services, the provision of optimized services tailored to individuals is expected. To make such a world a reality, it is essential that the use of biometric authentication is safe and secure.
Recently, as we shift to a society of non-contact interaction and no face-to-face contact in the novel coronavirus infection (COVID-19) pandemic, the role of non-contact biometrics is becoming increasingly important. Under these circumstances, NEC’s biometric technologies ranked first in the world in the benchmark tests conducted by the National Institute of Standards and Technology (NIST) in 2021 in two categories: face recognition and iris recognition1)2).
In this article, NEC's technological features of face recognition and iris recognition are described in Sections 2 and 3, respectively. Section 4 introduces multimodal authentication that combines these two biometric technologies to provide high authentication accuracy. In addition, Section 5 describes applications that will closely support individuals from the viewpoint of healthcare by using the core technologies of face recognition.
2. Face Recognition
As previously mentioned, the use of face recognition has been rapidly expanding in recent years. This is largely because of the high level of usability of face recognition, such as the ability to perform non-contact authentication. From the technological perspective, however, usability and accuracy are generally contradictory in many cases, and ensuring the authentication accuracy without compromising usability is a major feature of face recognition technology. Also, as usage expands, not only accuracy but also technology which ensures that the use of face recognition is safe and secure are becoming important as is taking precautions to prevent spoofing using other people’s photographs or ID. Face recognition uses data (called face feature vectors) to authenticate individuals. Any data leaks, however, would have a significantly negative impact on the privacy of users. Therefore, the development of privacy protection technology is also important to address such situations.
Section 2.1 introduces the features of NEC’s face recognition in terms of authentication accuracy, Section 2.2 introduces NEC’S anti-spoofing technology, and Section 2.3 introduces NEC’s technology for privacy protection.
2.1 Special features of NEC’s face recognition
In recent years, the accuracy of face recognition has dramatically improved because of the progress made in deep learning. This improvement in accuracy has supported the expanded use of face recognition as mentioned earlier, but super high accuracy is required in some fields, and greater improvement of the accuracy of face recognition is still important.
Under these circumstances, NEC’s face recognition has been ranked as best in the world for accuracy in benchmark tests conducted by NIST. In particular, our strengths are in large-scale authentication with many galleries and in large age-gap authentication with a maximum age gap between images of 10 years.
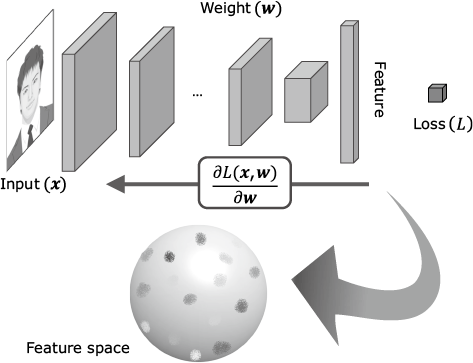
This section describes NEC’s high-accuracy face recognition technology. The process of face matching, which is the core of face recognition, is shown in Fig. 1. Face matching extracts facial features and converts them into vectors expressed in a string of numerical values best suited to identifying individuals. The accuracy of face recognition varies greatly depending on how best to calculate these facial feature vectors. NEC’s face recognition uses a proprietary method that maximizes the differences between exact matches and similar matches in calculating these facial feature vectors, and from a technical perspective this is a feature that enables us to achieve such high accuracy.
2.2 Anti-spoofing face recognition
Spoofing is the act of impersonating other people by using the photographs or other ID belonging to other people. Three main types of spoofing include the use of photographs and displays as shown in Photo 1 and 3D masks used as disguises. A technology must be developed to detect all three types of spoofing.

NEC is developing a technology to detect all three types of spoofing with high accuracy. The accuracy standards for the detection of presentation attacks (spoofing) are stipulated by the ISO standard ISO/IEC 30107-3. NEC’s spoofing detection was the first released by a Japanese company to be found in compliance with this ISO standard in tests conducted by an international quality assurance organization that is an independent third party3).
2.3 Privacy protection
The facial feature vectors used in face recognition are numeric strings in which the characteristics of the face are compressed. Recovering the original facial image from these feature vectors is almost impossible but not completely impossible if the algorithm used for face recognition is also obtained at the same time. It is necessary to prevent facial feature vectors from being used for purposes other than authentication, such as spoofing.
NEC is developing cancelable biometric authentication and encrypted face information as technologies to prevent such unauthorized usage. Cancelable biometric authentication is a technology that can be used to convert biometric feature vectors into something that is irreversible using keys that are registered in the system and used for face recognition. Because the feature vectors are irreversibly transformed, the original biometric feature vectors are not known. Even if the data is leaked, the data is invalidated by re-converting it with a new key. The latter is a technology that strongly protects the feature vectors by computing the authentication results while the feature vectors are encrypted.
3. Iris Recognition
The iris refers to a doughnut-shaped area surrounding the pupil located at the center of the eye. The iris is suitable for biometric identification because a person’s iris pattern is unique and generally remains unchanged throughout a person’s life, and because it is protected by the cornea, it is less susceptible to damage compared to other parts of the body. Section 3 introduces the technology used in iris matching, which is the basis of iris recognition. We will then introduce a walkthrough-type identification that uses NEC’s iris recognition technology to capture high-resolution iris images from a walking person and to instantaneously verify his/her identity.
3.1 Iris matching
In iris matching, a fine pattern in an iris area is used to compare two iris images, a registered image and a matching image, to verify the identity of a person. NEC’s iris-matching makes full use of AI-based authentication technology — one of NEC’s strengths — and is characterized by an extremely high authentication accuracy for images that have deteriorated quality because of various disturbances, which can often occur in practical situations. NEC’s iris recognition technology ranks first in the world in the benchmark test (IREX 10) conducted by NIST for iris recognition.
3.2 Walkthrough-type iris recognition
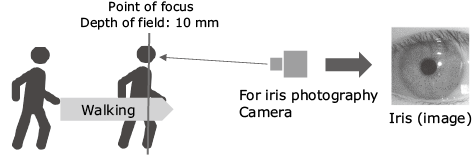
Because iris recognition uses a fine pattern in an iris with a diameter of approximately 12 mm as a feature, iris images are captured at a resolution (10 to 15.7 pixels/mm) that is approximately 25 times higher than that of face recognition. NEC is considering a walkthrough-type recognition approach to making iris recognition more convenient. To realize iris recognition as a walkthrough-type system, an advanced iris sensing method is required, because the camera, whose focal point is set slightly away from the camera itself, needs to capture irises of a person as a high-quality image without blurring at the moment when he/she passes through this focal point, as shown in Fig. 2.
The processing flow of iris sensing is shown in Fig. 3. We have developed image quality assessing technology to select images of suitable quality for authentication from a group of images around the eye area. These images are captured continuously when a walking subject passes near the focal point. We have also developed high-speed, high-precision eye position detection technology and iris detection that robustly detects iris areas against light reflections and other disturbances. These technologies are integrated into NEC’s iris sensing method.

This walkthrough-type iris recognition system that uses the iris sensing can capture the iris of a person who is walking at a speed of 1 m/sec and can instantaneously verify the person’s identity.
NEC’s walkthrough-type iris recognition system can use people’s irises to identify them while they are walking as shown in Photo 2. This system allows identification without stopping people. Because this system can realize high accuracy biometric authentication with a high throughput of approximately 20 people per minute without imposing a burden on anyone, NEC’s system can be applied to access control of important facilities that require control of many people entering and leaving the facilities within a short period of time.

4. Multimodal Authentication
This section introduces a multimodal biometric authentication terminal that incorporates face recognition and iris recognition.
NEC’s multimodal biometric authentication terminals enable authentication that achieves a false acceptance rate (FAR) of less than one in ten billion by integrating face recognition technology — which is being rapidly introduced in a variety of applications because it is highly convenient to use — and iris recognition technology that enables advanced biometric authentication. In addition, high speed authentication can be performed with stability and high accuracy in large-scale systems that must respond to a diversity of physical characteristics and in usage environments that require strict identity verification.
This multimodal authentication terminal automatically adjusts the angle of the built-in camera in accordance with the height of the user. It then detects the face and iris by determining the position of the face and eyes, and at the same time, verifies the identity based on the matching scores of similarity. To capture a high-resolution image of the iris with high quality, which has previously been difficult to do compared to face information, the position of the iris is quickly and accurately identified from face information, and the focus and lighting are automatically adjusted in an instant. This enables high speed biometric authentication in approximately two seconds without imposing a burden on anyone even if individual heights are different.
These multimodal authentication terminals are expected to be widely used in a variety of applications, including use in large-scale systems in countries and regions around the world, access control for offices that require high security, food processing factories that require hygienic clothing and masks, clean rooms in factories, medical facilities, as well as quick identification of customers at ATMs and prompt payment at stores (Photo 3).

5. Healthcare Applications of Face Recognition
Some signs related to mental and physical health as well as emotions might appear on people’s faces. By applying face recognition technology, we can detect gaze, iris, pupils and so on. If we can capture faces with even greater accuracy, we will then be able to obtain a variety of information such as changes in facial color or movement, blinking, pupil size, iris movement, and facial expressions. If physiological information or behavioral characteristics can be known based on this information, it could provide an opportunity to identify mental and physical health conditions (Fig. 4).
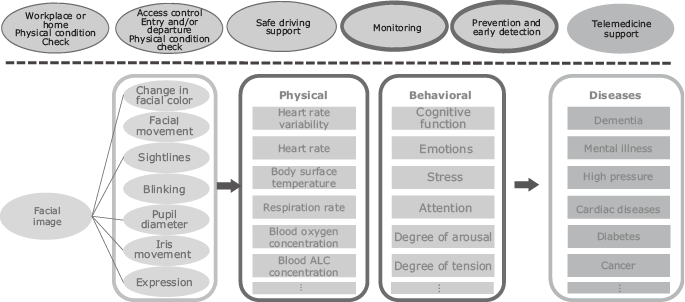
Such healthcare applications based on NEC’s face recognition technology have the potential to be used in a wide range of businesses. Companies can use it to keep track of the physical conditions of employees when they go to the office or stay at home. At airports, face recognition can be used to control the spread of infectious diseases by checking someone’s physical condition at the time of immigration as well as a variety of other applications. When driving a car, the driver’s physical condition can suddenly change. As the number of elderly people who live on their own increases in an aging society, we can respond to the need to protect and care for the elderly. Furthermore, even in telemedicine, which has already begun operation in some regions, we can expect that the accuracy of examinations will further increase if more information can be provided to doctors.
6. Conclusion
In this article, we have explained NEC’s technologies and applications of face recognition and iris recognition, which are recognized as best in the world. In the future, we will work on research and development with the aim of expanding use scenes where high reliability is required. In addition, we will apply the technologies cultivated through biometric identification to a wide range of applications, including healthcare.
References
- 1)
- 2)
- 3)
Authors’ Profiles
NEC Fellow
Senior Engineer
Biometrics Research Laboratories
Senior Principal Researcher
Biometrics Research Laboratories
Deputy General Manager
Biometrics Research Laboratories
Principal Creator
Biometrics Research Laboratories
Principal Researcher
Secure System Research Laboratories
 PDF
PDF


