Global Site
Displaying present location in the site.
July 26th, 2021
Machine translation is used partially for this article. See the Japanese version for the original article.
Introduction
In Amazon Web Services (hereinafter called "AWS"), we tried building an HA cluster using VPC endpoint.
A VPC endpoint is an AWS service that allows you to privately connect a VPC to other AWS services without having to go over the Internet.
This time, we will build an "HA cluster based on VIP control" with a private connection using the VPC endpoint.
(HA cluster based on VIP control is one of the cluster configurations using EXPRESSCLUSTER on AWS.)
Contents
1. VPC Endpoint
A VPC endpoint is an AWS service that allows you to connect VPC and other AWS services privately without having to go through an Internet gateway, NAT gateway, NAT instance, etc.
For example, when accessing S3 from an EC2 instance placed in a VPC, accessing S3 from an EC2 instance can be achieved through a private access path that does not go over the Internet by using the VPC endpoint.
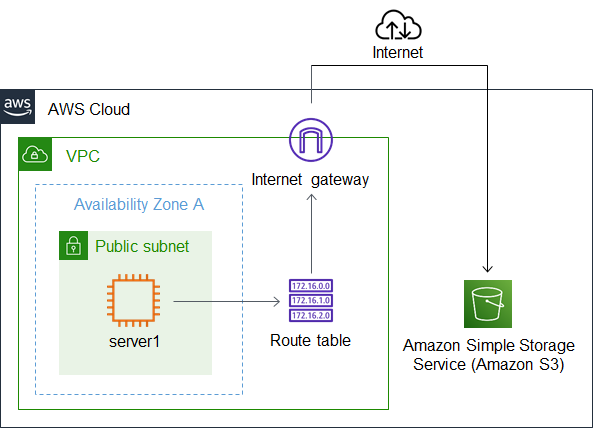
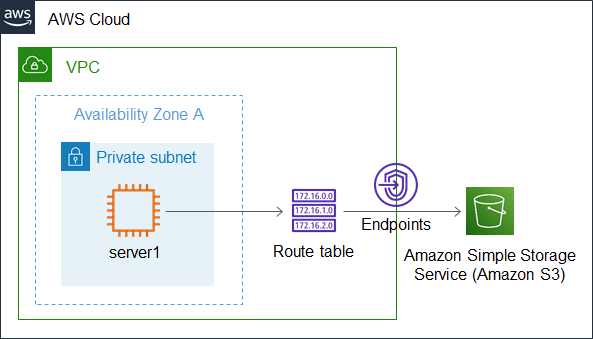
The benefits of using VPC endpoints is follow:
- Reduce AWS usage fees by eliminating the need for NAT gateways, NAT instances, etc. when accessing AWS services from a private subnet.
- Access to AWS services without over the Internet provides a more secure access path.
2. HA Cluster Configuration
The HA cluster configuration is a two-node mirror disk type, and is a "HA cluster based on VIP control" using AWS Virtual IP Resources.
HA cluster based on VIP control configuration requires the instance to communicate with the region endpoint through HTTPS in order for the instance to perform VIP control processing by AWS CLI.
In the above configuration, the instance accesses AWS services (Amazon EC2 APIs) without access to the Internet through the VPC endpoint.
Windows and Linux are available for the instances that make up the HA cluster. This time, we will build a HA cluster using Linux for instance.
From now on, the instance assumes that you have installed the AWS CLI, set up the region, set the security key, and set up the network.
3. HA Cluster Building Procedure
3.1 Preparation for HA Cluster Construction
Create a VPC in advance. The configuration of the VPC is as follows:
- VPC (VPC ID : vpc-1234abcd)
- - CIDR:10.0.0.0/16
- - Subnets
- ■ Subnet-1a (Subnet ID : sub-1111aaaa) : 10.0.10.0/24
- ■ Subnet-2a (Subnet ID : sub-2222aaaa) : 10.0.110.0/24
- ■ Subnet-2b (Subnet ID : sub-2222bbbb) : 10.0.120.0/24
- -RouteTables
- ■ Main (Route table ID : rtb-00000001)
- > 10.0.0.0/16 --> Local
- > 0.0.0.0/0 --> igw-1234abcd (Internet Gateway)
- > 20.0.0.100/32 --> eni-1234abcd (ENI ID of server1)
- ■ Route-A (Route table ID : rtb-0000000a)
- > 10.0.0.0/16 --> local
- > 20.0.0.100/32 --> eni-1234abcd (ENI ID of server1)
- ■ Route-B (Route table ID : rtb-0000000b)
- > 10.0.0.0/16 --> local
- > 20.0.0.100/32 --> eni-1234abcd (ENI ID of server1)

3.2 Creating VPC Endpoints
This time, I'm going to create a VPC endpoint using AWS CLI (AWS CLI version is "1.14.3").
AWS CLI, like the AWS Management Console, does not need to run from an environment with EXPRESSCLUSTER X installed and can be run from any environment.
From now on, the result of executing the command described will be the result of running on Linux. Basically, it is the same in Windows.
3.2.1 VPC Settings
Set up the VPC. Run the following command to set the DNS resolution attribute of the VPC to Yes.
- DNS resolution : Yes
Run the following command to set the DNS host name attribute of the VPC to Yes.
- DNS host name : Yes
3.2.2 Creating Security Groups
Create a security group to associate with the VPC endpoint.
The AWS EC2 API allows security groups to control access to VPC endpoints.
Each instance must communicate https to the region endpoint to run the AWS CLI, and the security group allows communication at HTTPS.
First, run the following command to create a security group for your pre-created VPC (vpc-1234abcd).
- Group name : SG-HTTPS
- Discription : SG-HTTPS
- VPC : vpc-1234abcd
{
"GroupId": "sg-1234abcd"
}
Then run the following command to add a rule that allows HTTPS to communicate with the inbound rules of the security group. For outbound, leave the default and do not add or delete any rules.
- Security group details
- - Inbound rules
- ■ Type : HTTPS
- ■ Protocol : TCP (6)
- ■ Port range : 443
- ■ Source : 10.0.0.0/16
- - Outbound rules
- ■ Type : All traffic
- ■ Protocol : All
- ■ Port range : All
- ■ Destination : 0.0.0.0/0
3.2.3 Creating VPC Endpoints
The service name specified by the VPC endpoint varies for each AWS service used.
Run the following command to verify the service name that corresponds to the Amazon EC2 API from the list of service names available on the VPC endpoint. Make a note of the name of the service you have checked here, as it will be used in the procedure described below.
(* The aws service name used this time is "com.amazonaws.us-east-1.ec2".)
{
"ServiceDetails": [
… (Abbreviation) ...
],
"ServiceNames": [
"aws.sagemaker.us-east-1.notebook",
"aws.sagemaker.us-east-1.studio",
"com.amazonaws.us-east-1.access-analyzer",
… (Abbreviation) ...
"com.amazonaws.us-east-1.dynamodb",
"com.amazonaws.us-east-1.ebs",
"com.amazonaws.us-east-1.ec2", <-- Service name for Amazon EC2 API
"com.amazonaws.us-east-1.ec2messages",
"com.amazonaws.us-east-1.ecr.api",
"com.amazonaws.us-east-1.ecr.dkr",
"com.amazonaws.us-east-1.ecs",
… (Abbreviation) ...
"com.amazonaws.us-east-1.transfer.server",
"com.amazonaws.us-east-1.workspaces",
"com.amazonaws.us-east-1.xray"
]
}
Run the following command to create a VPC endpoint.
- VPC : vpc-1234abcd
- VPC endpoint type : Interface
- Service name : com.amazonaws.us-east-1.ec2
- Subnet associations
- - subnet-2222aaaa
- - subnet-2222cccc
- Security group : sg-1234abcd
{
"VpcEndpoint": {
"PolicyDocument": "{\n \"Statement\": [\n {\n \"Action\": \"*\", \n \"Effect\": \"Allow\", \n \"Principal\": \"*\", \n \"Resource\": \"*\"\n }\n ]\n}",
"VpcId": "vpc-1234abcd",
"NetworkInterfaceIds": [
"eni-00000001",
"eni-00000002"
],
"SubnetIds": [
"subnet-2222aaaa",
"subnet-2222cccc"
],
"PrivateDnsEnabled": true,
"State": "pending",
"ServiceName": " com.amazonaws.us-east-1.ec2",
"RouteTableIds": [],
"Groups": [
{
"GroupName": "SG-HTTPS",
"GroupId": "sg-1234abcd"
}
],
"VpcEndpointId": "vpce-00000000000000001",
...(omission)...
}
}
After you create the VPC endpoint, verify that the AWS CLI can run from each instance that configures the HA cluster.
Run the command below to verify that the VPC information is displayed.
{
"Vpcs": [
{
"VpcId": "vpc-1234abcd",
"InstanceTenancy": "default",
"Tags": [
{
"Value": "VPC-01",
"Key": "Name"
}
],
"CidrBlockAssociationSet": [
{
"AssociationId": "vpc-cidr-assoc-1234abcd",
"CidrBlock": "10.0.0.0/16",
"CidrBlockState": {
"State": "associated"
}
}
],
"State": "available",
"DhcpOptionsId": "dopt-1234abcd",
"CidrBlock": "10.0.0.0/16",
"IsDefault": false
}
]
}
3.3 Creating an HA Cluster Based on VIP Control
Create a "HA cluster based on VIP control". EXPRESSCLUSTER failover groups only register AWS Virtual IP Resources and Mirror Disk Resources.
For the configuration procedure, see "EXPRESSCLUSTER X for Windows HA Cluster Configuration Guide for Amazon Web Services".
 Documentation - Setup Guides
Documentation - Setup Guides- Windows > Cloud > Amazon Web Services
- Linux > Cloud > Amazon Web Services
The following is an example of EXPRESSCLUSTER configuration when Linux is used as the instance that makes up a HA cluster.
- EXPRESSCLUSTER
- - Failover group
- ■ AWS Virtual IP resource
- > IP Address : 20.0.0.100
- ■ Mirror disk resource
- > Data Partition : /dev/xvdb2
- > Cluster Partition : /dev/xvdb1
4. Checking the Operation
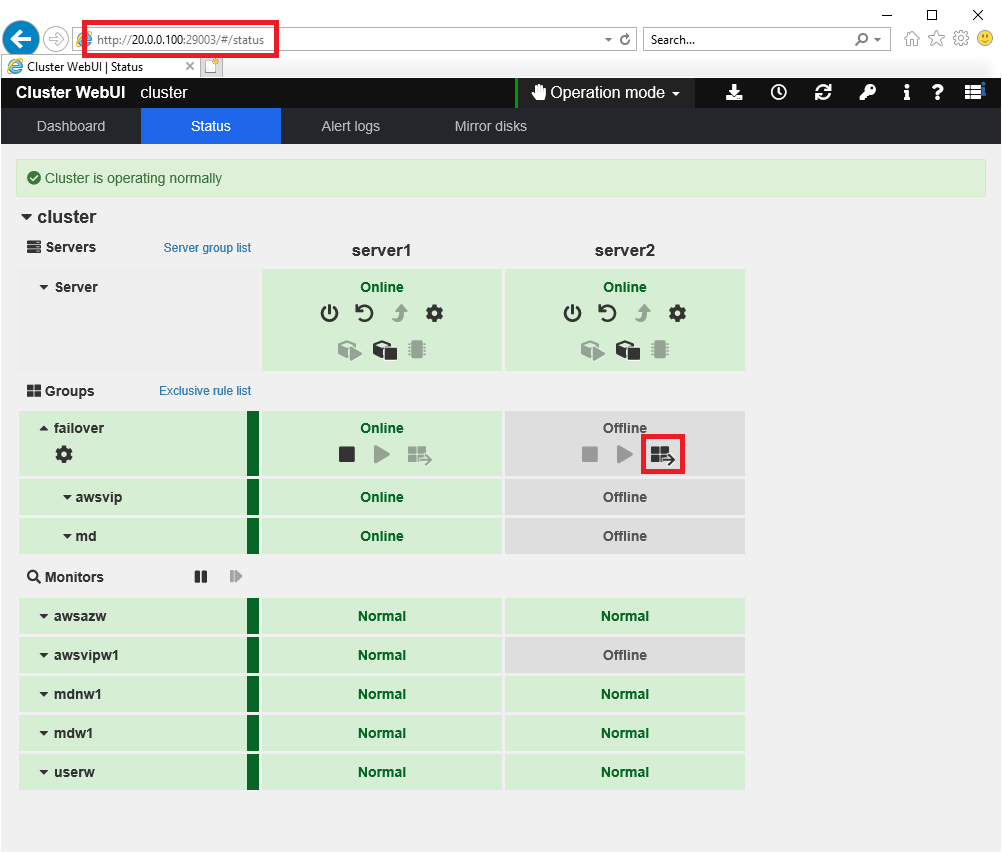
Connect to Cluster WebUI with the virtual IP address (20.0.0.100) you set in AWS Virtual IP Resources and verify that it is working properly. Also, if the failover group is failed over to the standby server, make sure that you can still connect with the same virtual IP address(20.0.0.100).
Conclusion
This time, we introduced the procedure for building a HA cluster with a private connection using VPC endpoints.
Using the VPC endpoint, we were able to confirm that a HA cluster that does not access the Internet from a private subnet can be built.
If you consider introducing the configuration described in this article, you can perform a validation with the  trial module of EXPRESSCLUSTER. Please do not hesitate to contact us if you have any questions.
trial module of EXPRESSCLUSTER. Please do not hesitate to contact us if you have any questions.

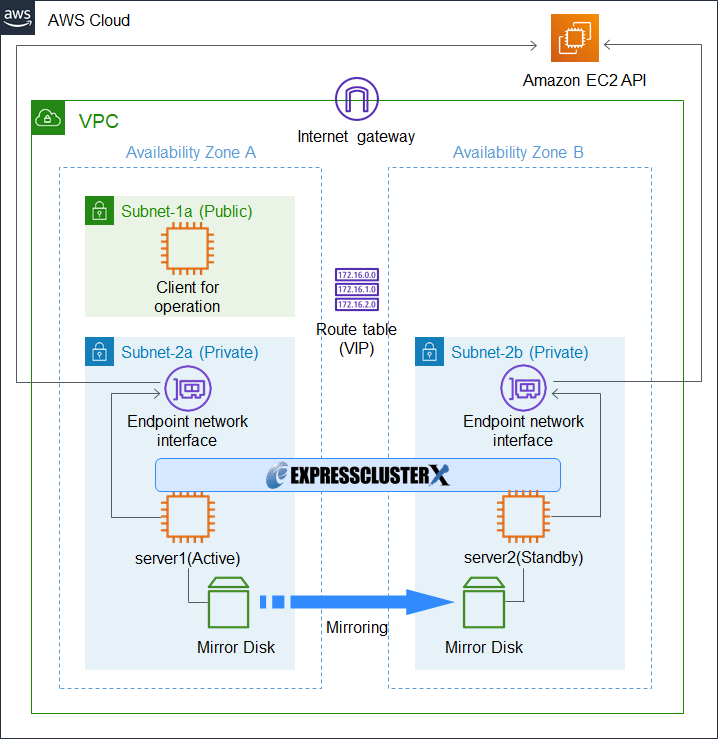
 Larger view
Larger view