Global Site
Displaying present location in the site.
Underwater Surveillance System to Counteract Associated Underwater Threats
Vol.8, No.1 September 2013, Special Issue on Solving Social Issues Through Business ActivitiesIn order to contribute to creating a safe and secure society by focusing on the field of public safety, NEC Radio Application Division proposes a recently developed underwater surveillance system capable of inspecting suspicious underwater intrusions that are generally considered to be hard to assess. Acts of terror that target public transportation services and installations are occurring continually worldwide. These threats adopt ingenious technical innovations and exploit changing situations, the tactics adopted are flexible and varied. Our recently developed underwater surveillance system is described below. It manifests high stability, reliability and may be adopted flexibly for use in underwater environments. This paper introduces solutions that may suitably support it and to discuss the results of actual testing in the marine environment.
1. Introduction
The continual occurrence of acts of terror in recent years that target public transportation services, including aircraft, trains and buses, governmental institutions and large-scale installations have caused countries worldwide to argue for the need for effective countermeasures. In Japan, too, the crisis control management solutions of key infrastructures such as power plants, airports and harbors are being hastily reviewed in order to be able to adopt early countermeasures. Considering the location of Japan as an island surrounded on all four sides by waters, key waterfront facilities should be prepared for threats both from on and under the water, as well as for land born attacks.
Under these circumstances, NEC Radio Application Division has been proposing and developing systems for monitoring suspicious underwater intrusions by focusing on the field of public safety with the aim of creating a "safe and secure society." As light and radio waves have problems in reaching underwater, the threats should be mainly identified by acoustic waves. However, the detection of underwater intrusions is difficult because the propagation of acoustic waves is affected significantly by underwater environments. These include changes in the water temperature, salinity, underwater pressure, submarine topography and ambient noise. While land surveillance can easily be enhanced by various means including radar, camera and by installing an entrance gate, etc., it has been hard to apply measures to provide effective underwater surveillance. In addition, threats always vary according to the type of target under attack by incorporating innovative and ingenious technologies, countermeasures to deal with such threats are required to be as flexible as possible.
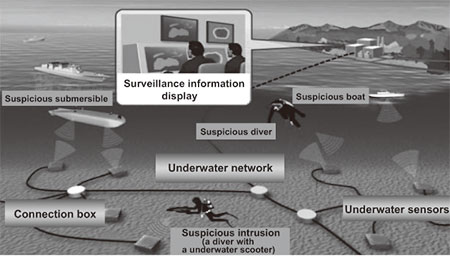
The proposed underwater surveillance system constructs an underwater sensor network on the seabed; the network is composed of various sensors and suitable connection boxes to connect these sensors. Fig. 1 is a schematic diagram that explains our underwater surveillance system that implements a flexibility enabling a sensor layout that accords to the underwater environment, redundancy that is assured by multiple transmission paths, maintainability that facilitates sensor replacement after the start of service, and extendibility that can deal with various types of threat. Below, we describe specific technologies associated with the system.
2. Hardware
Fig. 2 shows the overall configuration of the system. The hardware configuration can be classified into the land and underwater blocks, and the underwater block further classified into the network equipment and sensors.
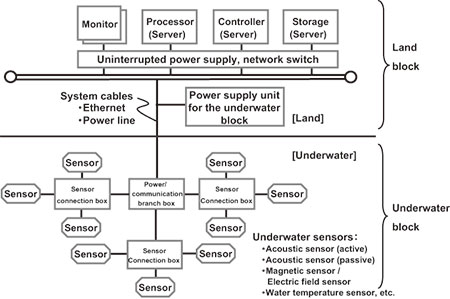
2.1 Land Block
The land block consists of the servers that manage all of the sensor data integrally, process the signals and display the surveillance results, the general-purpose network equipment and the power supply unit to the underwater block.
2.2 Network Equipment of the Underwater Block
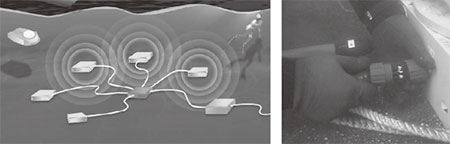
The network equipment of the underwater block consists of the equipment for feeding power to the underwater block components, the communications equipment for exchanging various information and the underwater cables. The scale is determined by the surveillance range and the oceanic environment, including the sea bottom topography. The network can take a mesh configuration as required in order to improve the survival (avoidance of overall system down) by selecting routing, even in the case of a cable disconnection due to intentional obstruction. Fig. 3 (left) shows a representation of the sensor connection box, and Fig. 3 (right) a view of underwater connection work. Connectors with underwater connection/disconnection capabilities are adopted to enable addition, change and replacement of sensors underwater and to facilitate maintenance and system extension/reduction1).
2.3 Sensors of the Underwater Block
Sensors of optimum performance are selected for the underwater block to suit the type of intruder (diver, submersible, boat, etc.), surveyed area and the underwater environment, including the sea bottom topography. The main connectable sensors are as follows:
(1) Active acoustic sensor
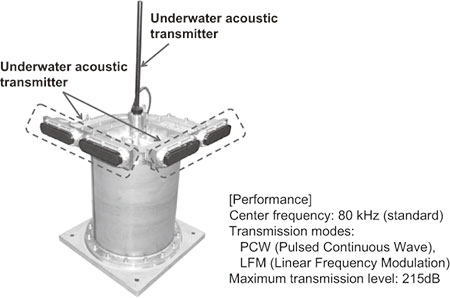
The active acoustic sensor (Fig. 4) transmits acoustic waves underwater and receives the echoes to obtain the distance, direction and depth of the target. Such a sensor may be installed on the seabed or on a bridge pier and the detection range is about 800 meters if for example the intruder is a diver. In addition to a sensor with the structure shown in Fig. 4, a portable type may also be used for improved convenience. The sensor may also be suspended from a mooring ship, in which case the detection range would be about 200 meters if the intruder was for example a diver.
(2) Passive acoustic sensor
The passive acoustic sensor (Fig. 5) receives the sound (screw noise, diver's respiration, etc.) emitted by the intruder, calculates the direction and distance, and classifies the type of the intruder.

(3) Non-acoustic sensors
Non-acoustic sensors refer to the sensors detecting intruders by means other than by acoustic waves. They include magnetic sensors that detect the magnetism radiated from the intruder and the electric field sensors that detect any electric fields.
Combining a range of sensors as described above enables a sequence of countermeasures against various kinds of threads. With any sensor, the detectable distance varies depending on the conditions including the intruder type and the underwater environment.
3. Processing Technologies
Below we introduce the processing technologies used in the signal processing of typical acoustic sensors and the underwater integrated processing that integrates and displays the information detected by the sensors.
3.1 Acoustic Sensor Signal Processing
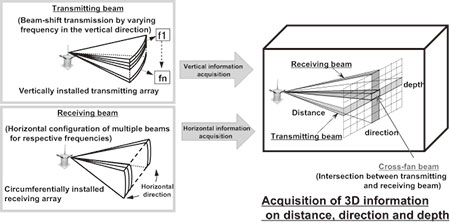
The parts transmitting and receiving the acoustic waves of the active acoustic sensor consist of arrays of multiple piezoelectric elements (hereinafter "elements"). These arrays can be used to form a desired beam, while the cross-fan system shown in Fig. 6 is used to enable identification of the direction, distance and depth of the target.
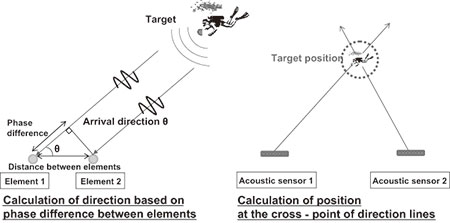
With the passive acoustic sensor, as shown in Fig. 7, the signal arrival direction is calculated based on the phase difference between arrays of multiple elements so that the target location can be identified by combining multiple passive acoustic sensors with different installation positions and acquiring the cross-point of their measurement directions. The nature of the target can also be classified by creating a database of the frequency-related characteristics of sounds generated by various targets (spectral characteristics or acoustic signature) in advance and by collating the received sound with it.
3.2 Underwater Integration Processing
The underwater integration processing integrates the data detected from multiple acoustic sensors and displays it as underwater integrated data on the map information. This provides data on a target that could be a threat (position, arrival time, etc.) with high accuracy and in an easily understandable manner to support a land based observer in applying quick, effective countermeasures against the target. Fig. 8 shows the processing blocks of the overall system from the initial target detection via sensors to the display and alarms. Fig. 9 shows an example of an integrated underwater information display.
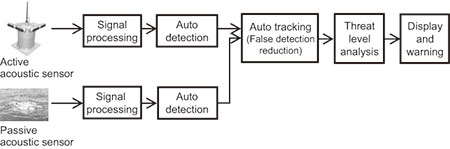
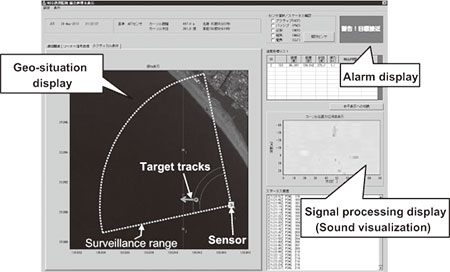
As data obtained by auto detection contains a large number of redundant (false detection) signals due to multiple acoustic reflections from the surface and bottom of the sea as well as noise, etc., many errors may be produced if unfiltered data is used that may suggest the existence of an intrusion and/or its location. To prevent such occurrences, the data is filtered using the MHT (Multiple Hypothesis Tracking) algorithm in the auto tracking processing at a later stage. We have observed that the auto detection results (false detection) are discontinuous due to noise, etc., and have developed this algorithm so that true data related to the target can be traced from the multiple detection results by eliminating any false detections. In addition, the threat level analysis processing scores the threat level from the information on the movements of traced targets and judges whether or not it should be dealt with. Then, the target trajectory with the threat level is displayed on a photograph or a map together with the location data acquired from the sensor. In case the threat level exceeds the assessment criterion, the target is judged that it should be dealt with, and the alarm is generated. There is also the processing for displaying the signal processing results, which visualizes the acoustic waves to enable intuitive confirmation of the existence of a target.
4. Results of the At-Sea Test
In March 2012 at sea around the port of Numazu, Shizuoka Prefecture, we evaluated performances of both the active and passive acoustic sensors, using a diver and a jet ski as the main targets.
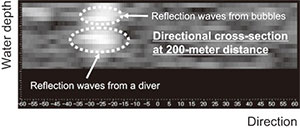
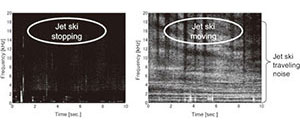
Let us first review the results of the diver detection (signal processing display) of the active acoustic sensor. Fig. 10 depicts the vertical cross-sectional display of direction-vs.-depth obtained by detection of a diver at a distance of 200 meters when using the cross-fan beam. The reflection waves from the diver and regurgitated bubbles can be confirmed in the areas enclosed by broken lines in the figure. Next, Fig. 11 is the result of the detection of a jet ski (signal processing display) using the passive acoustic sensor. The figure shows that the detection level varies particularly in the low-frequency range. This is due to movements of the jet ski. Consequently both the actual existence of the target and its spectral characteristics are critical.
5. Conclusion
This paper has introduced an underwater surveillance system that is designed to be commercialized in the public safety field. The system enables the adoption of previously hard to apply countermeasures against underwater threats at key coastal facilities. The system features a high surveillance capability and flexibility by adopting the significant technical expertise that we have cultivated in developing previous sonar defense solutions. When the system is linked with existing image sensors such as land based radar and Infrared cameras /high-sensitivity cameras, it is possible to provide an overall high reliability surveillance system that can deal satisfactorily with surveillance targets in various environments, ranging from underwater to sea surface and land locations. We believe that the service will be improved further by advancing its scope to include the prediction and prevention of incidents by applying cloud computing and big data handling solutions.
Reference
- 1)M. Nakano et al.: Flexible integrated maritime security network system, Maritime Systems and Technology mastAmericas 2011 Conference, 6-C3, 2011. 11
Authors' Profiles
Manager
Radio Application Division
Integrated Undersea Warfare Systems Group
Manager
Radio Application Division
Integrated Undersea Warfare Systems Group
Assistant Manager
Radio Application Division
Integrated Undersea Warfare Systems Group
Assistant Manager
Radio Application Division
Naval Systems Department
Assistant Manager
Radio Application Division
Integrated Undersea Warfare Systems Group
Radio Application Division
Integrated Undersea Warfare Systems Group