Global Site
Displaying present location in the site.
NEC Cloud IaaS Supports DX Offerings
Advanced Technologies and Methodologies Supporting DX OfferingsNEC launched NEC Cloud IaaS as a domestically made, in-house cloud platform service in 2014 and revamped it in 2020 to support the information system security management and assessment program (ISMAP), enhance price competitiveness, and improve platform quality for the company’s DX offerings.
This paper will explain how continuing to use domestic clouds as well as in-house clouds is significant, what systems are being developed and how they are operated, and what skill sets are in place as the mega cloud is increasingly being adopted to enable digital transformation (DX). The paper will also discuss future cloud computing initiatives in Japan that leverage these achievements.
1. The Role of Domestic Cloud Computing in Digital Transformation
NEC procures servers, storage, network equipment, and management software manufactured/provided by NEC as well as products from other companies; combines these to plan, design, and implement the services required by customers as Infrastructure as a Service (IaaS); and then develops the processes, procedures, and talent to operate these services.
These activities have shown us that having our own domestic cloud enables us to provide the quality and security demanded by customers. In addition, by operating a large-scale, domestic cloud for NEC’s own use, we continue to maintain expertise in IaaS system configuration and operations that support digital transformation (DX).
2. Business Areas Addressed by Domestic Cloud Computing
2.1 Domestic cloud required for digital transformation in the government sector
The first business area that the domestic cloud should address is cloud computing in the government sector. Domestic cloud computing is needed as a place to put sensitive data held by governments, municipalities, and public institutions.
In the future, based on the concept of best of breed, the ideal systems without any special requirements should be constructed using open, cost-competitive hyperscalers based in other countries. On the other hand, systems that handle classified information for governments should be constructed in a private cloud environment operated by a domestic vendor. The use of multicloud computing is expected to make advancements in government sectors.
2.2 Domestic cloud computing needed for DX utilization in core business systems
Cloud lift of core business systems for Japanese companies is another area where domestic cloud computing is used. This is because for digital transformation of core business systems in Japanese companies, some ingrained cultural ideals and needs do not align with Western hyperscalers in terms of operational quality, system failure response and follow-up.
Where foreign hyperscalers strictly follow service specifications and agreements as written in regard to disclosure of information and actual response to system failures, domestic cloud providers often put the customer first and bend to the needs of the customer. This difference is one of the reasons that major Japanese companies will select a domestic cloud provider to promote DX.
2.3 Network connectivity required to promote DX
Many Japanese companies have systems that are installed on-premise locally or co-located in DCs that cannot be moved to the cloud. To promote DX, there is a growing need for network technology to seamlessly connect systems that have lifted/shifted to the cloud, systems that are still on-premise/co-located, as well as systems that are comprised in multiple cloud environments.
This need is especially high in the transitional period of shifting to the cloud where some legacy systems will remain co-located in the data center while cloud computing is being deployed in stages elsewhere.
3. NEC Cloud IaaS Architecture
3.1 Government clouds and the need for enhanced security
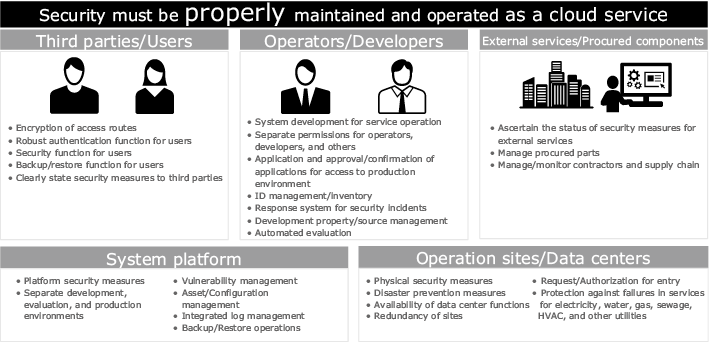
The information system security management and assessment program (ISMAP) is a Japanese government program for assessing the security level of government information systems. It aims to ensure the level of security that cloud service providers (CSP) must comply with and contribute to the smooth implementation of cloud services through evaluation and registration of CSPs that meet the security requirements of the government.
The ISMAP steering committee receives applications from CSPs being audited and reviews applicants for compliance to standards for governance, management, and control measures by examining more than 1,000 requirements that are defined in detail at each layer. If the applications are accepted, the CSP’s cloud services are registered on the ISMAP cloud services list. Some examples of requirements for registration are:
- Strong authentication for users, such as provision of multi-factor authentication
- Application/approval processes for access to production environments and strict control of operators
- Separation of components, to provide fault tolerance or security
- Automated vulnerability assessment, such as periodic scans to ascertain status, and more.
A wide review of the operational procedures of NEC Cloud IaaS as well as development to further strengthen its infrastructure was done to meet the wide range of ISMAP requirements. Actual results that provided proof of its operational procedures were then submitted to the ISMAP auditing organization. After a review process that lasted approximately six months, NEC Cloud IaaS was registered on the ISMAP cloud service list in March 2021 (Fig. 1).
3.2 Cost reduction and enhanced competitiveness by product procurement
In designing the configuration of the High Availability Plus (HA-Plus) execution platform for NEC Cloud IaaS, our priority was to select a product that could be stably procured at the lowest cost that also met our requirements. To do this, we made a side-by-side comparison of not only NEC products but also those from outside vendors before making our selection. We compared the following items:
- Ability to be procured globally
- Ability to implement a globally standard architecture
- No service downtime or other negative impact during maintenance and replacement
3.3 Enhanced resiliency and service lifecycle
The HA-Plus service for NEC Cloud IaaS has reduced downtime and improved availability compared to our conventional services. Our basic policy for improving availability is as follows:
- Design for availability, including redundant components, so that a single point of failure does not disrupt service
- Catch errors in the application layer and perform retransmission instead of expecting the lower layer (TCP/UDP) to do the retransmission
- Provide redundancy of three or more components to eliminate the need for immediate action if one component fails
In addition, multiple zones have been constructed to ensure that user application services can continue even in the event of widespread failures, such as failures that occur to storage devices. Users can specify a specific zone when creating a virtual server, which enables operations to continue in other zones even if a failure occurs in one certain zone.
3.4 Seamless connection between co-location and cloud
NEC Cloud IaaS provides a network connection service within the hosted data center that connects customer’s co-located server racks to the NEC Cloud IaaS network. This enables customers to implement systems connected to their co-located equipment with low latency.
Also, by using our public cloud connection services, the data center can be connected to other public clouds via a closed network to realize a multicloud system that enables the use of other clouds and services to meet customer needs.
4. Service Operation and Management of NEC Cloud IaaS
Since its launch in 2014, NEC Cloud IaaS has deployed services operation and management to handle approximately 10,000 incidents per year and 50 enhancements or modifications per year based on specified rules and processes. Many users utilize multiple services such as co-location in combination with NEC Cloud IaaS. Proper service operation and management are conducted so that users can safely and securely use our services.
4.1 Service portal
The NEC Cloud IaaS service portal provides customers with features to perform operational and management tasks (contracts, arrangements, billing), customer communication (portal, inquiries, notices), and service desk (provision of services) (Fig. 2).
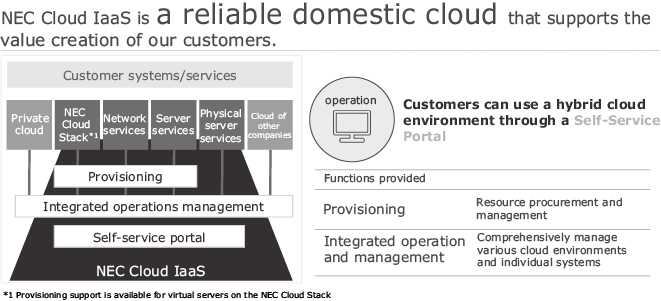
In addition to NEC Cloud IaaS, support is also currently provided for other services such as co-location and provision of hyperscaler clouds through the same portal, and we are working to make it possible not only to apply for services but to also use the portal for tasks such as applying for admission into the data center, access to the service desk, or other permissions using the same ID.
This service portal is used not only by users but also by NEC’s own sales force, system engineers (SE), and operational staff of various services. It is a tool for the safe and secure execution of operational processes for large-scale service businesses.
4.2 Service operation
NEC Cloud IaaS is currently operated by rules and processes defined for more than 100 service menus and more than 50 modifications per year. It is unfortunate that failures occur, but we are working to improve operations by taking measures such as predictive detection, redundancy in design, workarounds, and other solutions to reduce the impact of failures on services. These efforts combined with automated reports help to reduce the impact of failures on business operations.
4.2.1 Operational improvement group
To quickly resolve issues, we have established an operational improvement team that understands the operational requirements and can make efficient improvements.
The operational improvement group is organized into teams for each functional component. Each group understands development requirements, user requests and security requirements, sets priorities, and puts actions forward. The group has become the core ingredient in providing continuous stable operations while development and automation proceed at a rate that is more than double the efficiency compared to when the group was not yet in place.
4.2.2 Operational automation
Automation efforts are continuing to advance by dividing them into automation triggers and automated processes. Automation triggers use monitoring tools to monitor the system for changes and to detect anomalies. Automated tools for the web and command automation tools are currently being used.
For example, after an anomaly is detected by a monitoring tool, we use a command automation tool to automatically block network devices and isolate the section with the anomaly, thereby ensuring that normal communication paths continue. Automated web tools are used to automatically check the functionality of new NEC Cloud IaaS features when they are released and to input data to web pages for tasks such as creating IDs.
4.3 Internal control and regulation certification
NEC Cloud IaaS is compliant with various regulations for security and internal control, including SOC 2 Type 2, ISO27017, ISO27018, ISMAP, and others.
For ISMAP, as mentioned in Section 3, NEC Cloud IaaS meets the standards for governance, management, and control measures that are defined in detail at each layer. To obtain and maintain certification, confirmation that the design information and performance results meet the requirements are done, which are then verified and reported by an auditor.
5. Future Initiatives
5.1 Multicloud utilization in DX offerings
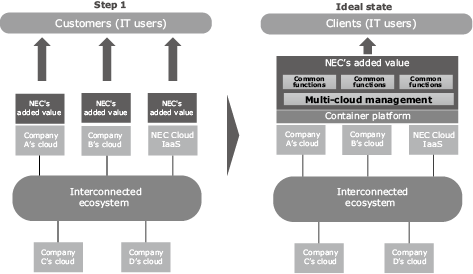
With the variety of clouds in existence today, businesses that are making advancements in DX will wish to procure the services they need from the necessary clouds and combine them to develop their desired system. On the other hand, NEC will differentiate itself as a cloud service provider by leveraging our own strengths as a domestic cloud vendor, such as quality, security, white box operations, and other features unique to domestic cloud computing, as well as being able to provide the rich functionality offered by global hyperscaler cloud providers. Next-generation domestic cloud services will require the capability to provide customers with a multicloud environment that combines the strengths of several or multiple cloud vendors, and the services will also require the capability to link the services provided by these cloud vendors with customers’ on-premise environments.
5.2 Next-generation domestic cloud architecture
To provide services utilizing the multicloud, our first step is to work on value-added services for the hyperscaler cloud. We will manage the hyperscaler cloud with the added value of our knowledge accumulated through operating NEC Cloud IaaS and provide it as a DX offering, combining the functions of multiple services to solve specific issues. As the next step, we aim to automatically deploy developed applications and stored data to multiclouds simply by designing multicloud utilization policies through multicloud management and container technologies (Fig. 3).
Authors’ Profiles
Senior manager
Service Platform Department
Senior manager
Service Platform Department
Senior manager
Service Platform Department
Senior manager
Service Platform Department
Deputy General Manager
Service Platform Department
General Manager
Service Platform Department
 PDF
PDF