Global Site
Displaying present location in the site.
Multi-Bank Identity Confirmation Platform — A New Way to Verify User Identity Using Digital Technology
The rapid expansion of digital services in recent years has been accompanied by an increase in crimes such as identity theft and spoofing, making it urgent to establish more reliable identity confirmation methods and making them widely available. Thanks to revisions to business laws and progress in open application programming interfaces (open API), verified identity information accumulated by banks over the years can now be utilized by external entities. In this paper, we will examine the advanced information distribution platforms developed by NEC to help businesses and other organizations to utilize this data, providing both an overview and a more in-depth look at some of the platform’s technological aspects, including security functions to ensure secure data distribution, as well as its operability. We conclude by discussing the future prospects of this technology.
1. Introduction
The tremendous pace at which digitalization has been proceeding in the economy and society overall has made it possible to provide many services remotely—including financial services. Traditional face-to-face transactions are becoming less and less common, increasing the likelihood of fraud, identity theft, spoofing, and other criminal activities. This has made it necessary for enterprises to not only apply more rigorous checks to verify a user’s identity, but also to ascertain whether that user actually exists at all.
In the financial industry, identity confirmation is based on extremely strict protocols as laid down by relevant business laws. To enable the use of digital technology to further improve convenience and strengthen the identity confirmation process, the Act on Prevention of Transfer of Criminal Proceeds was revised in 20181), thereby permitting identity confirmation to be done completely online through a method called eKYC (electric Know Your Customer).
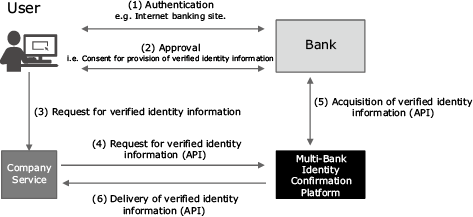
In terms of target user coverage, as well as the reliability of the verified identity information owned by banks, the bank inquiry stipulated in Revised Act, Article 6, Paragraph 1, Item 1 (Fig. 1) is expected to play a key role in any authentication platform developed not only for enterprises subject to the Act on Prevention of Transfer of Criminal Proceeds, but also any enterprise that offers digital services. In response, NEC has developed and released a multi-bank identity confirmation platform that facilitates inquiries to multiple banks2) (Fig. 2).
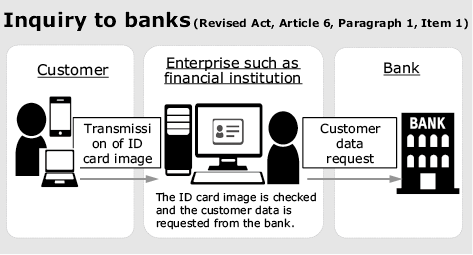
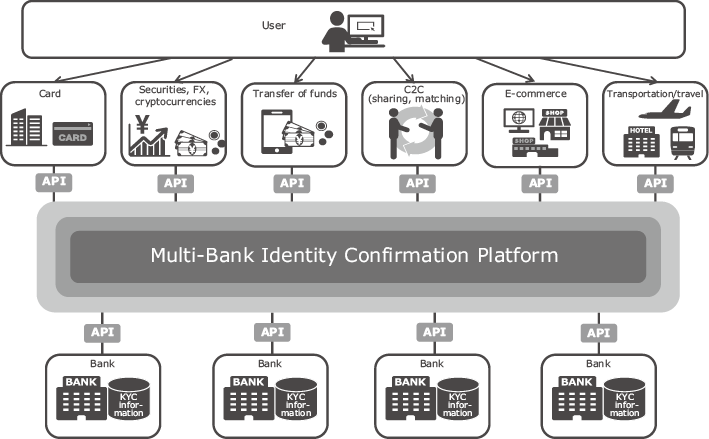
This platform functions as a data distribution mechanism that provides verified identity information owned by banks to various enterprises in accordance with consent from users. Any business subject to the Act on Prevention of Transfer of Criminal Proceeds can identify users online by checking identity confirmation documents transmitted as image files and verified identity information owned by banks (names, addresses, dates of birth, etc.), instead of having to use conventional identity confirmation information sent by postal mail. Also, because bank data can now be collated with information obtained from users when they apply for services, a more detailed picture of the user can be obtained and services tailored more precisely.
Because inquiries to multiple banks are now possible simply by connecting to this platform, any potential problems that may occur when specifications for system connection are developed or modified or when testing is performed will be significantly reduced.
2. Technology Components That Constitute This Platform
As shown in Fig. 3, this platform connects multiple enterprises. It uses open APIs (publicly available application programming interfaces whose specifications are open to external users) to provide functions that ensure safe and secure distribution of verified identity information. It features technology components that can be divided into three basic areas: enterprise connection, bank connection, and a system platform that supports the operation of this platform. Now let’s take a look at these features.
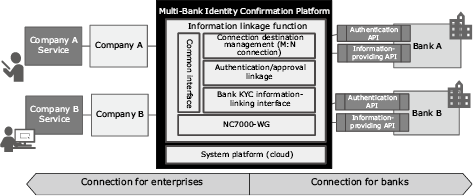
2.1 Enterprise connection
For enterprises, we have made the interface public in the open API format (REST/JSON format). To make this interface public, we use the NC7000-WG API linkage service3) which is NEC’s open solution for web services. The API linkage service features the following:
- (1)Safety
- Security functions indispensable for safe opening of an API
- Flow restriction functions such as limitation in the number of accesses and open/close control of the service
- (2)Lightweight
- High-performance message transfer by caching
- (3)Flexibility
- Flexible, customizable mechanism by adding individual logics to each API using custom plugin
By optimizing utilization of the functions offered by the API linkage service, this platform achieves safe data distribution between enterprises and banks (Fig. 4).
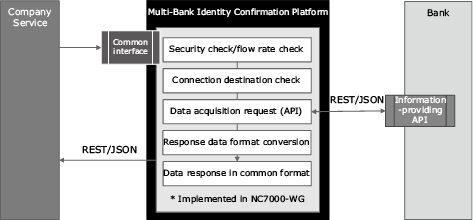
2.1.1 Managing connection destinations (establishing the M:N connection)
When using this platform, availability of connectable banks varies as specified in the applications submitted by enterprises. For example, while Enterprise A may obtain information from Bank A and Bank B, Enterprise B can only get information from Bank B. Operating in conjunction with the contract management system, this platform ensures that each enterprise user can connect only to designated banks.
2.1.2 Bank KYC information-linking interface (common interface)
After learning the various message formats used by different banks, this platform provides enterprises with the data in a common, standardized interface. Differences exist between banks; for example, while postal code data is included in the address entry at Bank A, it is a separate entry at Bank B. By learning the differences between interfaces, this platform makes it possible to rapidly deploy services without having to consider differences between the interfaces used by different banks.
2.1.3 Bank KYC information-linking interface (flow control)
This platform controls the amount of traffic that flows into the platform by setting a limit on the number of connections. This function is also used to prevent any traffic surges that can impose a bigger load on bank systems.
2.2 Bank connection
2.2.1 User authentication/approval
When acquiring personal information, banks first obtain consent from users for provision of their identity authentication and personal information in compliance with the OAuth 2.0 Authorization Framework specified in RFC 67494). Then the users check that their data is up-to-date and permit companies and services to acquire their information. Finally, the companies and services acquire user information from the banks via this platform (Fig. 5).
2.2.2 Assuring traceability
From the bank’s perspective, the connection source is this platform only. However, the verified identity information is actually provided to enterprises specified by the user. This means that it is necessary to improve traceability in the distribution of verified identity information between enterprises and this platform as well as between banks and this platform. Thanks to the core role this platform plays in distribution of that information, data distribution history can be visualized, showing when the data was acquired, by what user, via what enterprise, and from what bank.
2.3 System platform
This system is designed while incorporating our most advanced technologies to ensure safe, secure distribution of verified identity information.
2.3.1 Cloud platform
To ensure adaptability to future expansion of services, this system uses a cloud platform to ensure maximum security and redundancy, while maintaining stable services on a continuous basis.
2.3.2 Platform security
Security is based on the concept of defense in depth, with powerful protective measures installed at every layer from the operating system layer to the application layer.
Communication between this platform and users, as well as between this platform and banks, is protected with Transport Layer Security (TLS), an encryption protocol designed to keep network data traffic secure, in order to minimize the risks of en-route eavesdropping and forgery.
As shown in Fig. 6, the whole system is protected with functions such as access restriction, IDS/IPS (Intrusion Detection System/Intrusion Prevention System that detects and prevents attacks targeted at vulnerabilities in systems and networks), and WAF (Web Application Firewall to protect web applications from attacks).
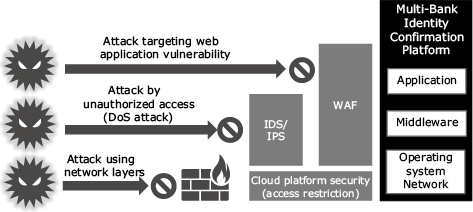
Platform security is further enhanced by 24/7 manned surveillance which ensures a rapid response to any security incident that may occur.
3. Conclusion
In this paper, we have seen NEC’s technological commitment to use cases in which verified identity information owned by banks is distributed in the open API format and then utilized for identity confirmation at enterprises.
In response to the trend towards open API, it is expected that the operational functions and data owned by banks will be incorporated more broadly in daily life and accessed by various enterprises and industries. As proposed in “Report of Review Committee on Open APIs: Promoting Open Innovation”5) published by the Japanese Bankers Association, it is also anticipated that the commitment to open API will move forward in other businesses leading to the evolution of an ecosystem where banks and other enterprises will mutually exchange a variety of data.
In addition to the verified identity information owned by banks, we have confirmed that there exists a need for other data—such as financial assets. In view of this, we are working to expand the functionality of our authentication API to better handle the complex authentication procedures needed for various business services. NEC is committed to expanding the performance and capabilities of this platform, while improving convenience and operability and maintaining data integrity.
Reference
- 1)
- 2)
- 3)
- 4)
- 5)
Authors’ Profiles
Senior Manager
Digital Integration Division
Manager
Digital Business Infrastructure Division
Assistant Manager
Digital Business Infrastructure Division
 Financial Services Agency: Announcement of “Cabinet Order on Arrangement of Relevant Cabinet Orders and Transitional Measures Associated with Enforcement of the Act on Partial Revision of the Act on Prevention of Transfer of Criminal Proceeds” (Japanese), November 2018
Financial Services Agency: Announcement of “Cabinet Order on Arrangement of Relevant Cabinet Orders and Transitional Measures Associated with Enforcement of the Act on Partial Revision of the Act on Prevention of Transfer of Criminal Proceeds” (Japanese), November 2018 Japanese Bankers Association: Report of Review Committee on Open APIs: Promoting Open Innovation, July 2017
Japanese Bankers Association: Report of Review Committee on Open APIs: Promoting Open Innovation, July 2017