Global Site
Displaying present location in the site.
Information Security and Cyber Security
Governance
Information Security and Cybersecurity Framework
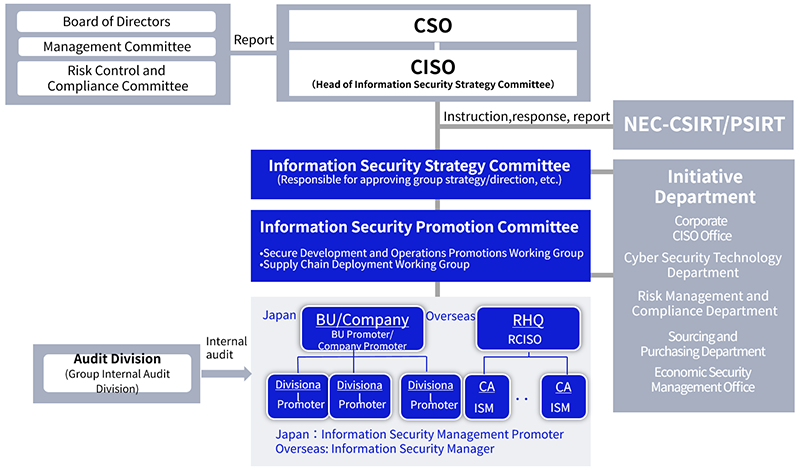
The NEC Group’s information security implementation framework comprises the Information Security Strategy Committee, its subordinate organizations, and related organizations.
Chaired by the Chief Information Security Officer (CISO) of NEC Corporation, the Information Security Strategy Committee discusses, evaluates, and improves information security measures, investigates the causes of incidents, sets the direction of recurrence prevention measures, and discusses how to apply the results of its activities in the information security business. The committee also regularly briefs the President of NEC Corporation on the status of measures adopted by the committee to obtain approval. In addition, we conduct annual penetration tests via a third-party organization to assess vulnerability risks. We also conduct audits of all external servers four times a year.
These actions ensure that vulnerabilities are dealt with in a timely manner.
The CISO oversees the Corporate CISO Office, which promotes information security measures, and the Computer Security Incident Response Team (CSIRT), which monitors for cyberattacks and resolves incidents quickly whenever they occur. The Information Security Promotion Committee and Working Groups plan and promote security implementation, discuss and coordinate implementation measures, ensure that all instructions are followed, and manage the progress of measures, among other things.
General managers at NEC Corporation have responsibility as information security managers for ensuring information security for the relevant organizations, including the Group companies under their supervision. They work to ensure that rules are understood within their organizations, introduce and deploy measures, while continuously checking and reviewing the implementation progress to improve the situation.
In FY2025, CSIRT’s Cyber Threat Intelligence (CTI) team gathered and analyzed over 46,000 items of data (IP addresses, file hashes, web addresses and domain names) related to cyber threats within NEC Group to generate threat intelligence. Furthermore, by using CTI to hunt threats, the CTI team is proactively reducing risks.
We have introduced cyber risk assessments (CRA) carried out by the “Red Team,”1 and are enhancing our capabilities as an organization by building greater organizational resilience to cyberattacks and expanding reporting requirements for security management practices. We have designed attack scenarios based on threats to the NEC Group, ICT usage conditions, incident status and levels of information handled, for which the Red Team conducts surveillance and controlled attacks to assess resilience and risks.
- 1.A team that conducts simulated cyberattacks mimicking real-world threats against companies and organizations, assesses the organization’s resilience to attacks and risk levels, and recommends improvements and additional countermeasures.
The NEC Group’s Information Security Implementation Framework
Strategy
NEC evaluates risks from various perspectives including the need for countermeasures as well as possible impacts both on corporate management and on society, and selects Priority Risks that it has evaluated as having major impacts and that need to be addressed. With these risks in mind, we are deploying measures to counter cyberattacks that are becoming increasingly sophisticated, while complying with the U.S. National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) 2.0 and Cybersecurity Management Guidelines Ver. 3.0 by Japan’s Ministry of Economy, Trade and Industry.
At NEC, we leverage the insights and know-how gained from in-house initiatives to create opportunities, providing expertise in security measures to help strengthen customer security strategies.
As a specific example, together with NEC Security, Ltd., NEC offers services that visualize vulnerabilities in externally exposed IT assets at high risk of attacks, as well as authentication information such as IDs and passwords that may have been leaked to the dark web2, all without altering customer IT environments. These services help reduce risks and enhance security.
- 2.Websites that are not displayed by general search engines, and require special tools or browsers.
Risk Management
Information Security Management
To facilitate the establishment of a variety of groupwide measures, we have introduced an information security management system and security policy, both of which we continuously work to maintain and improve.
Information Security Risk Assessments
The NEC Group conducts risk assessments and implements countermeasures by analyzing deviations from baseline criteria and carrying out detailed risk analysis, with both methods conducted separately. First, we ensure that security is implemented in line with criteria that serve as a baseline, and when more advanced management is necessary, we conduct a detailed risk analysis and implement finely tuned countermeasures.
Risk Management for Information Security Incidents
Information security incidents are subject to mandatory reporting. The contents of these reports are analyzed, and the results are put through a PDCA cycle for risk management assessment. Incident information is centrally managed for the entire NEC Group, and changes in the number of incidents, trends by organization and type of incident, and other data are analyzed. NEC then reflects this analysis in groupwide measures while also measuring the effectiveness of these measures.
Critical Information Management
Based on the Three Lines Model, the NEC Group establishes a scheme to manage critical information by clarifying the roles of the three lines.
The NEC Group has a framework to classify and manage the corporate secrets it handles based on the security level. Each organization checks details of all the information it handles, and clearly identifies its security level to ensure that all necessary information is properly managed. We also have rules for handling, storing and managing critical information according to importance, as well as thorough measures to prevent information leaks.
Addressing Security Risks Arising from Increasing Geopolitical Risks
As the geopolitical situation changes and digital transformation advances rapidly, private companies are also becoming targets of national cyberattacks, and companies that possess critical information such as advanced technological information are facing increasing security risks. The rapidly increasing sophistication and complexity of cyberattacks, along with external factors such as geopolitical risk, may hamper timely mitigation of security risks.
These are treated as emerging risks.
In the event that personal or confidential information held by NEC or contained in its products, services, or systems is leaked or exposed through unauthorized access or cyberattacks and used fraudulently, NEC may be subject to disciplinary action by regulatory authorities due to its position of legal responsibility. As a result, NEC may not only lose the trust of its customers as a Social Value Innovator, but its business performance may also be adversely affected.
The risk of unauthorized access and cyberattacks exists not only for NEC’s own products, services and systems, but also for those of its customers, contractors, suppliers, business partners and other third parties.
As a mitigation measure, we are implementing robust and flexible measures throughout the Group based on the US Cybersecurity & Infrastructure Security Agency (CISA) Zero Trust Maturity Model. Based on Cybersecurity Management Guidelines Ver. 3.0 formulated by the Ministry of Economy, Trade and Industry and the NIST Cybersecurity Framework (Version 2.0), we are strengthening intelligence (proactive defense) and resilience (ability to recover from attacks) against cyberattacks. In addition, presenting security risks to all employees on a cybersecurity dashboard as part of our data-driven transformation is supporting quick management decisions and autonomous front-line actions. Thus, we are transforming the expertise and countermeasure doctrines developed through our front-line experience into solutions that we offer to our customers. Furthermore, based on Security by Design, which considers security from the design stage, we are enhancing measures that include our supply chain in order to provide safe, high-quality services.
Please refer to our Cybersecurity Management Report for details about our initiatives.
Metrics and Targets
Medium- to Long-term Goals, Priority Activities and Progress, Achievements, and Issues
Medium- to Long-term Goals, and Priority Activities
(Scope: NEC Corporation unless otherwise specified) Period: April 2021 to March 2026
M: Indicates the main non-financial targets related to materiality.
-
Strengthen measures against cyberattacks
-
Establish rules and governance for security proposal implementation
M: Human resource development: Triple the number of Certified Information Systems Security Professionals (CISSP)- Strengthen supply chain security management
- Establish a safe system integration process
-
Eliminate security-related incidents caused by partner companies by inspecting their standards and enhancing cybersecurity measures
FY2025 Goals, Progress, Achievements and Issues, and FY2026 Goals
FY2025 Goals
-
Drive information security transformation
- Counter nation-state-level threats
- Comply with NIST Cyber Security Framework (version 2.0) and improve third-party evaluation results
- Have AI Red Team automate attack diagnostics
- Enhance threat intelligence performance - Realize zero trust security to support digital transformation (DX)
- Reinforce global authentication platforms
- Enhance internal fraud prevention measures
- Automate vulnerability management and other information security operations - Evolve awareness and control
- Implement information security surveys
- Strengthen the risk assessments of Group companies
- Visualize critical information management status
- Counter nation-state-level threats
-
Establishing, practicing and enhancing governance for security proposal implementation
- Establish security implementation framework and processes at Group companies in and outside Japan
- Ensure thorough vulnerability management and correction processes for NEC Group products and services
- Develop and deploy human resources who can make security proposals and implement them based on appropriate knowledge and skills
Progress, Achievement, and Issues
-
Drive information security transformation
- Counter nation-state-level threats
- Implemented additional audits through outside audits
- Implemented self-diagnostics of VPN equipment
- Optimized the utilization of external intelligence - Realize zero trust security to support digital transformation (DX)
- Constructed Hub & Spoke global authentication platforms
- Enhanced internal fraud prevention measures and implemented risk behavior monitoring
- Automated vulnerability management and other information security operations through Tanium x ServiceNow - Evolve awareness and control
- Implemented new measures for improving security awareness
- Strengthened the risk assessments of Group companies
- Realized understanding and visualization of important information through file labeling - Received “Special Award” at 2024 Japan DX Awards and “Grand Prize” at 2024 Japan Security Awards
- Counter nation-state-level threats
-
Establishing, practicing and enhancing governance for security proposal implementation
- Completed formulation of security rules and assignment of security personnel to major Group companies in Japan
- Completed formulation of security rules and assignment of security personnel to four Group companies outside Japan as model cases for application of security rules to Group companies outside Japan
- Completed modernization of vulnerability management system, eliminated the dependency on specific individuals for Product Security Incident Response Team (PSIRT) operations and realized earlier notification of high-risk vulnerability information (43% reduction)
- 560 people have obtained CISSP certification in the NEC Group (as of March 31, 2025). Furthermore, we entered into a partnership agreement with ISACA in the United States to develop human resources with knowledge and certification in information security auditing in our business divisions.
FY2026 Goals
-
Drive digital security transformation (DSX)
- DX security
- Reinforce global security platforms
- Reinforce AI security (Security for AI)
- Prevent leaks of important information through AI labeling and data loss prevention (DLP) - Cybersecurity
- Enhance global SOC/CSIRT
- Generate intelligence through deception
- Automate diagnostics through attack diagnostic AI agents - Rules and governance
- Optimize security rules in and outside Japan (risk assessment, rules for overseas subsidiaries, etc.)
- Enhance internal fraud prevention measures
- Respond to security clearance systems (responses for facilities, people and organizations)
- DX security
-
Establishing, practicing and enhancing governance for security proposal implementation
- Creation of a PSIRT system in coordination with Group companies in Japan
- Establishment of a security implementation framework and processes at Group companies outside Japan
- Mobility of security personnel and reskilling of personnel responsible for security
Main Initiatives
Details are described in the Cybersecurity Management Report.
Establishment of Information Security Rules
NEC has released the NEC Group Information Security Statement and established and streamlined a variety of rules, including overall information security rules, rules for managing corporate secrets, and IT security rules.
Information Security Education and Awareness Training
NEC provides a web-based training course on information security for all NEC Group employees (including dispatched workers, contractors, and workers with a de facto mandate), in addition to holding micro-theme talks in small groups after watching original videos, in an effort to increase information security knowledge and skills. The content of the training is updated every year to reflect information security trends, including information management, external security measures, and subcontractor management. In addition, NEC conducts information security surveys to measure awareness of information security in a questionnaire format for all NEC Group employees (including dispatched workers) to foster a high level of information security culture.
Enhancing Information Security Management at Partner Companies
Please see below for more details.
Information Security Certification
The NEC Group has aligned its overall information security rules with the international standard ISO/IEC 27001 (main standard and control measures) and manages information security in accordance with these rules. It has also acquired ISMS certification (ISO 27001) for almost all of its medical, financial, cloud and government and public business units, for which information security is critical.
Providing Secure Products, Systems, and Services
NEC has structured a security implementation framework for secure development and operation of the products, systems and services it provides to customers. This framework involves the Cybersecurity Strategy Department and information security managers in each business division at NEC, and security implementation processes are stipulated in the Cybersecurity Management Rules. NEC Group companies are also promoting the establishment of a security implementation framework and the formulation of cybersecurity management rules similar to those of NEC.
NEC implements security spanning from the planning and proposal phase to the operation and maintenance phase based on the concept of “security by design” (SBD) to ensure security. In the development of products, systems, and services, we create and utilize checklists to confirm that security tasks are being implemented in each phase. Based on these checklists, operational projects are managed and the status of security measures is efficiently inspected and monitored through the Cybersecurity Checklist Management Security Implementation Assessment System developed to centrally manage and visualize the implementation status of security tasks. In the operation and maintenance phase, we ensure security by collecting and distributing information on vulnerability in a centralized manner and by providing it to business divisions and customers.
Furthermore, as a measure to address security vulnerabilities, we have established the Product Security Incident Response Team (PSIRT) to collect and handle information on vulnerability related to NEC Group products. We appropriately handle such undisclosed information by having a point of contact for external inquiries and publishing a vulnerability disclosure policy.
NEC has also established a cloud-based software development platform as our standard internal environment for system development. This platform utilizes security vulnerability testing tools and other tools that streamline and automate security implementation to improve the productivity, quality, and security of system development. In addition, by consolidating the development environments of our supply chain, including operational projects and subcontractors, into this platform, we have centralized security management for those development environments to address risks such as information leaks during development and copyright issues arising when using generative AI.
Measures against Cyberattacks
As cyberattacks grow increasingly complex and sophisticated, the NEC Group focuses on the protection of information assets entrusted by customers and business partners as well as its own. To this end, the Group has implemented comprehensive cybersecurity management by conducting uniform and advanced measures worldwide based on cybersecurity analysis, and established an incident response framework with CSIRT.
Given that the NEC Group creates and provides social solutions for countries worldwide, an information security incident caused by a cyberattack or any other factor could diminish the social credibility of the entire NEC Group and significantly impact its business management. For this reason, the Group considers a comprehensive and global approach to cybersecurity risks to be essential for business continuity.
The NEC Group is strengthening its global measures against increasingly sophisticated cyberattacks while using generative AI and other technologies based on a multilayered defense approach.
Cyber risk assessments by the “Red Team”
- Regular cyber risk assessments are conducted with the aim of improving the NEC Group’s cyber resilience and accountability.
- A global assessment consisting of three investigations on 1) the management status of critical information, 2) risks that include public server vulnerabilities and data leakage, and 3) internal and external security breaches from an attacker’s point of view, are conducted to identify security risks that have been overlooked in security measures and operations, and actions are taken to implement improvements based on these.
- Audit organizations and security specialists are employed to conduct third-party attack diagnoses.
Generating and Utilizing Threat Intelligence
- The NEC Group’s cyber threat intelligence (CTI) team consists of specialists who possess an understanding of the threats facing NEC, detects their early signs as well as their precursors, and implements advanced proactive defense measures.
- The CTI team leverages the endpoint detection and response (EDR) tools deployed at all NEC Group companies, the network detection and response (NDR) that CSIRT independently developed, and a log analysis platform to hunt for unknown threats.
- The team has also created a research environment to enhance its ability to generate unique CTI proactively, analyze threats in detail and enhance organizational security resilience. Enhancing Organizational Security Resilience
Enhancing Organizational Security Resilience
- We have developed a manual to ensure rapid responses to ransomware attacks.
- Management, relevant departments and specialists hold training exercises for security incidents at least once every six months.
Advanced Cybersecurity Measures Using AI
- We promote the use of AI, including generative AI, and also achieve automation, efficiency, and sophistication in a wide range of fields, including cyber risk assessment diagnostics, threat intelligence generation and utilization, NDR detection, incident investigation, and targeted attack email training.
Cybersecurity Dashboard Drives Culture Change
- In order to improve the security awareness of employees, we have made available our cybersecurity dashboard, which visualizes the status of cyberattacks on the NEC Group, threat intelligence information, and the security risk status of each company and division.
- The cybersecurity dashboard is utilized at meetings attended by members of senior management and by all subsidiaries outside Japan to help enable swift management decisions and help security personnel manage more effectively.
 Larger view
Larger view