Global Site
Displaying present location in the site.
Asset Management Solution Based on RFID
Vol.1, No.3, Summer 2004, Special Issue: Advanced Technologies and Solutions toward Ubiquitous Network SocietyNEC is introducing an asset management solution making full use of RFID (Radio Frequency Identification.) This policy will be aimed at the enhancement of information security, software license management and improvements in job/asset efficiency. The integration of asset-related information, updating the latest information and identification of the locations of assets will be thus enabled. In particular, the use of RFID will provide solutions for the possibility of identifying information regarding the location of assets and the movement of goods. In systems terms, the information on the RFID tag is captured by the RFID reader, and this information is sent through the RFID Manager to the Location Information Middleware. The Location Information Middleware then converts the RFID reader’s information into location information; the location information and the RFID tag information are sent on to the Integrated Asset Management Database. Here the location information is tied to the asset information so that the asset location information can be identified in real time.
1. INTRODUCTION
Based on recent trends such as those relating to the enhancement of their information security systems, organizations are increasingly recognizing a need for asset management measures. For example, a rise in the awareness of legal compliance issues backed by the need for social contributions and a review of the management and usage of assets aiming at improvements to jobs and assets. These issues are currently tending to become more complicated than ever.
Therefore, NEC has been developing solutions that allow organizational assets to be managed precisely and efficiently.
- (1) Collection of Physical Inventory Data Using Automated Tools
The key to the first step in asset management is to identify and visualize the actual situation. The required information can be collected automatically and at low cost by introducing a suitable tool for the automatic collection of the security setup information of the IT equipment, the latest information on patch applications and detailed information on the installed software. - (2) Utilization of Information about Assets
The key to the second step is how to make full use of the asset-related information that is dispersed inside each organization. The asset-related information includes asset purchase information, lease/rental contract information, maintenance contract information, information concerning the on-cost departments, personal information on owners, information on installation locations and information on floor layouts as well as IT equipment inventory information that can be obtained by automatic collection. What is important in all of this is that these items of information are managed in an integrated manner. - (3) Keeping the Data Up-To-Date
The key to the third step is to update the information that you now hold for effective utilization in the latest context. In fact, this part is the most difficult and most critical part. The most important functions include the workflow linkage function for automatic information updating in relation to workflow from the procurement to the disposal of each asset, the function enabling simplified operation in the addition and updating of information, and the function for the automatic checking of whether or not each piece of information is the latest.
2. ASSET MANAGEMENT SOLUTIONS FROM NEC
2.1 Information Security
The first step toward the information security of an organization is to identify the circumstances of the assets of that organization. It is important to ensure linkage to the tools required for the necessary actions based on identification of the actual circumstances.
- (1) Identification of the Whole Picture of IT Equipment in the Organization
It is important to identify the whole picture of all IT equipment using an automatic information collection tool that is as simple as possible. It is also desirable to arrange the system environment so that this information can be updated continually. - (2) Identification of the Application Situation of the Security Patch of the OS
One of the causes of security problems is the security hole of the OS. To prevent this, it is important to confirm the applications status of the OS security patch. - (3) Identification of the Updating Situation of AntiVirus Software
Another cause of security problems is virus infection. It is important to confirm that the latest virus check engines and pattern files are applied. - (4) Promotion of Optimization of PCs with Insufficient Security Measures
After identifying the status of security measures, promote actions for improving awareness towards the security of each individual and linkage to the force patch application solutions.
2.2 Compliance of Organization
One of the conditions for ensuring an organization’s compliance is execution of effective software license management. Negligence in compliance measures is regarded as a dishonest practice and may lead to the loss of social credibility of the organization and a crisis for the organization and the persons responsible. In addition, since accurate inventory management is obligatory for corporate auditing, asset management is critical for the organization’s satisfactory compliance (Fig. 1).
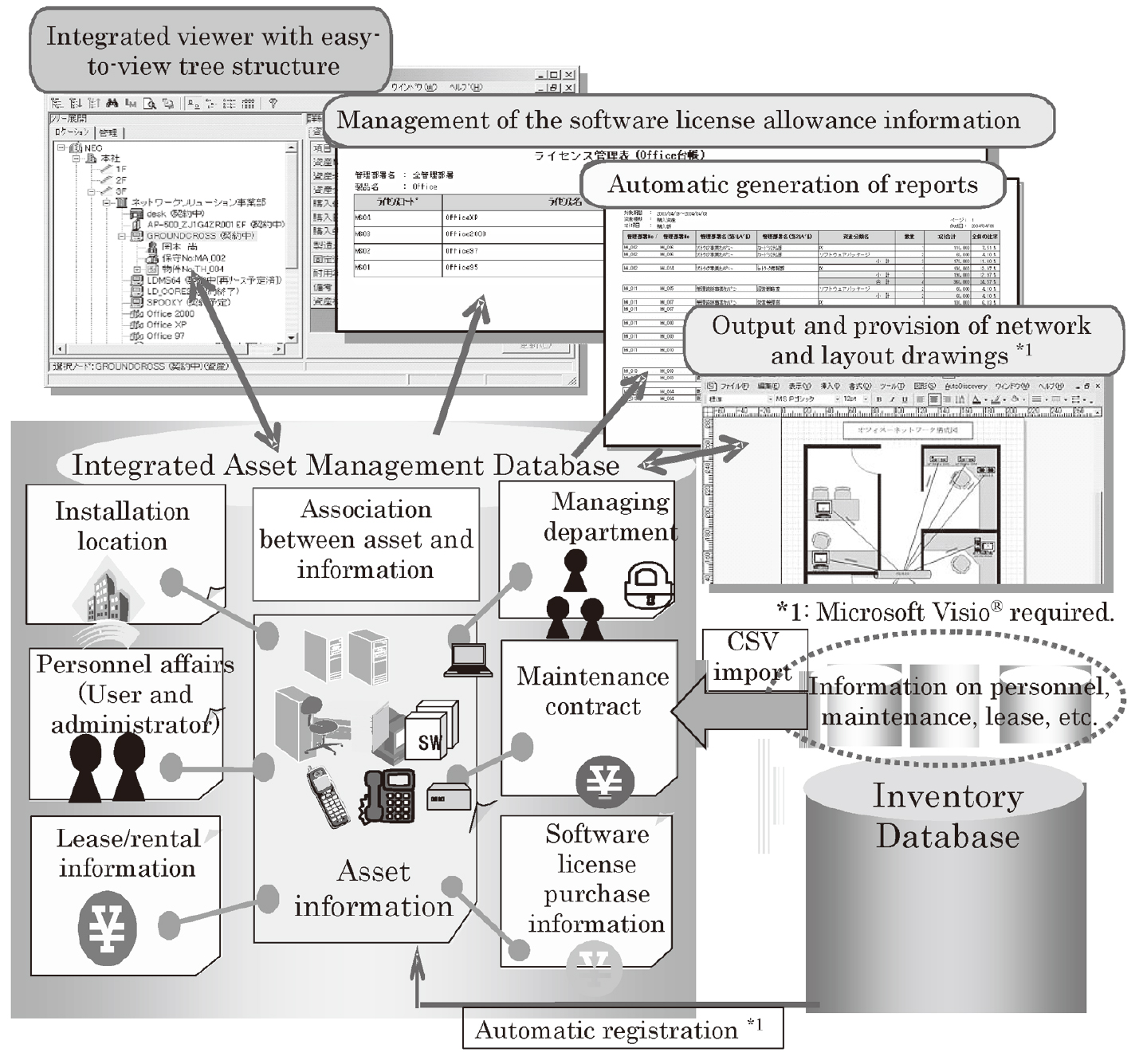
- (1) Implementation of Software License Management
The software license management should include a management mechanism which compares the detailed information on the actually installed software with the purchase license and compiles the results automatically into a report. If a piece of software with an expired license is installed, for example, it should be capable of informing the administrator of this. - (2) Implementation of an Accurate Inventory
The inventory for checking the actual stock status is obligatory for corporate auditing, and what is important for this operation is to manage the locations of actual stocks. A mechanism for managing the information on the locations of assets and maintaining the information at the latest level is essential.
2.3 Efficient Asset Utilization
One of the key points for the efficient utilization of assets is to utilize any unused assets and lessfrequently used assets effectively, as well as to analyze the situations of the currently used assets.
- (1) Effective Use of Idle Assets
Wasteful asset purchase can be prevented for example by collecting idle assets, which are not connected to the network, in one position and by announcing the information on them to the whole organization or purchasing department. By the announcement of asset information, an efficient idle-assets management system can be enabled by utilizing the real-time location information identification function provided by the RFID (Radio Frequency Identification) technology. - (2) Effective Use of Shared Assets
Shared assets vary greatly in frequency of use. Integrated management of the shared assets managed separately by different departments makes it possible to reduce overlapping of investments. The frequency of use of shared assets can also be identified automatically by utilizing the real-time location information identification function provided by the RFID technology.
3. CUSTOMER INCONVENIENCE
NEC will provide future solutions for solving the following problems that feature among current customer problems.
3.1 Integration of Information
Asset-related information regarding information security, compliance and effective asset use will be integrated to offer the foundations for enabling the unification of job processes.
3.2 Maintenance of Information at the Latest Level
Value-added solutions for maintaining data, which is now unified and effectively usable, as the latest accurate information will be provided as a real costreducing
solution for customers.
3.3 Identification of the Locations of Assets
Many customers are concerned by the problem of location identification in the management of actual assets. NEC will deal with this problem by detecting asset location information and movements using RFID technology.
4. INTEGRATION WITH RFID TECHNOLOGY
NEC is researching into the utilization of RFID technology for the “location identification” of assets in future solutions. The Identification of asset location
information, the identification of multi-location information and time linkage will make it possible to identify the circumstances of asset movements.
4.1 Real-Time Identification of Location Information
Automatic detection of the asset location information based on the RFID tags and readers enables an idle assets inquiry system, shared asset inquiry system and real-time identification of the asset location information at each floor with little human labor.
4.2 Identification of Goods Movements Information
Analysis of asset location information detected with multiple readers enables automatic identification of asset movement situations. NEC is developing solutions for customers’ problems such as the asset movement management accompanying changes in floor location and personnel and the automation of managements including the management of notebook PC issues (Fig. 2).
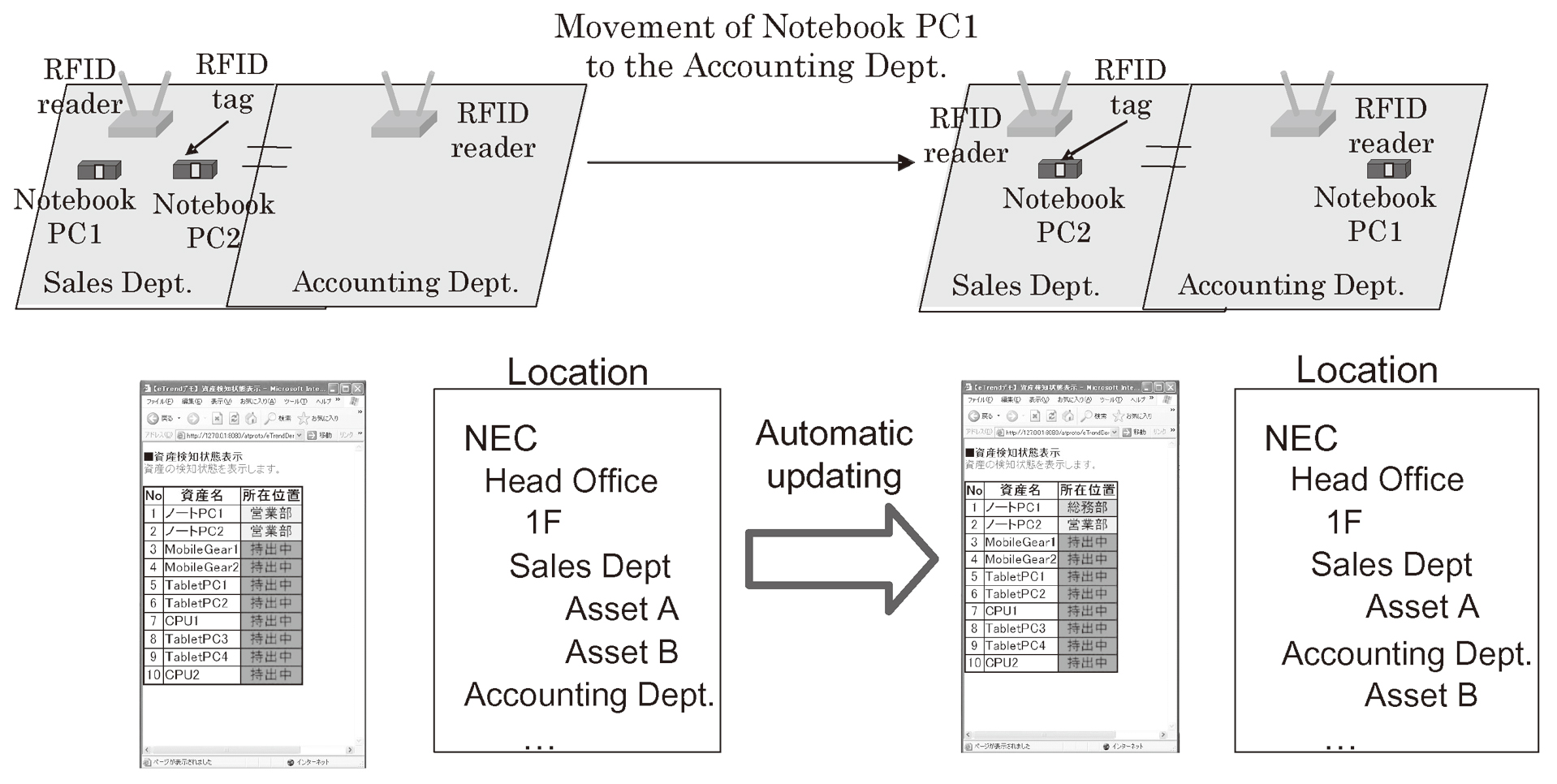
5. NEC’s ADVANTAGES IN THIS SOLUTION
5.1 Outline of the RFID Asset Management Solution
- (1) General
The RFID reader receives in real time the location information of each asset to which a RFID tag is attached. The received RFID tag information and RFID reader information are forwarded via the RFID Manager to the Location Information Middleware.
The Location Information Middleware converts the received RFID tag information and RFID reader information into the equipment location information (General Affairs Dept., Sales Dept., 1st Floor, 2nd Floor, etc.). The converted location information is handed to the Integrated Asset Management Database together with the RFID tag information.
The Integrated Asset Management Database links the location information and asset information so that real-time identification of asset location information is possible (Fig. 3)
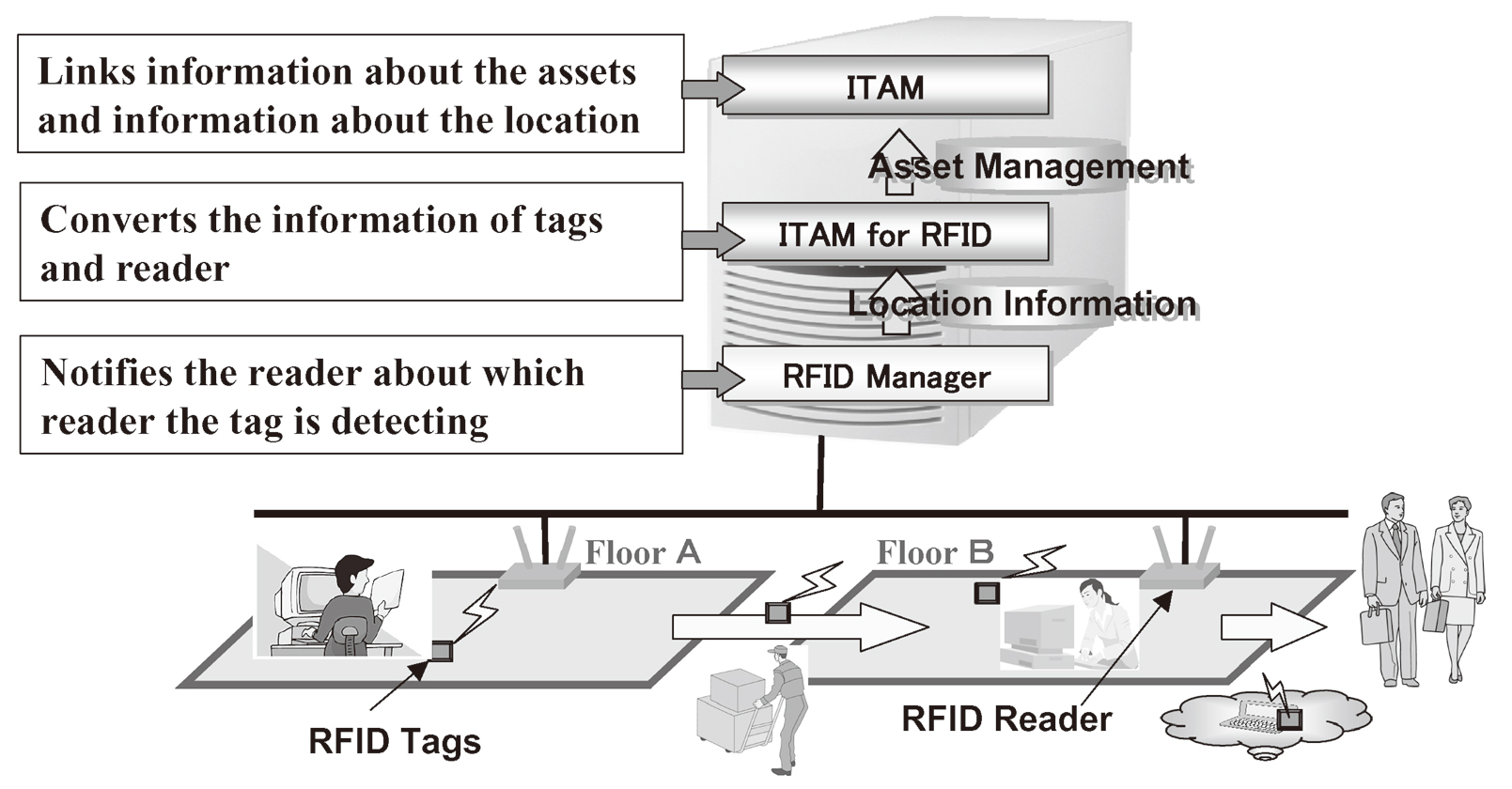
- (2) RFID Manager
The RFID Manager functions as the middleware for implementing solutions that make use of RFID.
This arrangement forms the basis for improving the system development efficiency and creates a highly reliable/usable system that has the following features.- 1)Efficient system development
- The RFID Manager can absorb any differences between individual devices (readers/writers and tags).
- It can deal flexibly with changes in devices, rearranging device configurations and lateral developments of the system.
- 2)Effective Tools for Systems Development and Maintenance
- It is equipped with a rich line-up of tools for use in performance analysis, operating situation report, etc.
- 3)Compatibility with Scalable Systems
- Even when building a system for handling a large amount of tags, the system can communicate the required information only to the applications.
- Hierarchical systems can be constructed so that each system can be given an optimum configuration according to its scale.
The RFID Manager module Ver. 1 to be released at the end of July 2004 provides the following functions.- ①An API (Application Program Interface) for the construction of systems based on RFID.
- ②An events control system that exchanges the tag information (ID/data) with the AP (Application Program) using the events format.
- ③A device management function that serves as the common device control function.
- ④A device plug interface that enables the use of new devices independently from the AP.
- ⑤A hierarchical configuration capability by concentrating multiple servers to which devices are connected as into a single server.
- ⑥A function for connecting the tag ID-related information to the server.
- ⑦Tools offering performance analyses and operating situation information for supporting the application and administration of the RFID system.
- 1)
- (3) Location Information Middleware
The Location Information Middleware collects the information detected from RFID tags by means of the NEC-developed middleware called the RFID Manager. The information detected from the tags includes the information on the RFID tag IDs and the RFID readers detecting them. The Location Information Middleware converts the RFID tag IDs into asset management numbers and the detecting RFID reader names into location information. It also maintains the latest location information of assets. When movement of an asset is detected, the middleware converts the data format of the location into a format that is usable by the Integrated Asset Management Database and forwards the data to this database. The Integrated Asset Management Database then applies the received location information in the database it uses. This makes it possible to identify the latest location information in the Integrated Asset Management Database and use this information together with other information managed by this database. The Location Information Middleware is the asset management compatible version developed as part of the traceability middleware being researched and developed by NEC as the middleware for the RFID services.
5.2 Superiority of NEC
- (1) Overall Supremacy of RFID-Compatible Software
NEC provides three-step components for asset management solutions based on RFID in an integrated form; it is thus capable of providing rapid solutions.- 1)RFID Manager
The RFID Manager integrates the interfaces for the RFID readers and writers, which are newly, released devices offering the foundations for handling the readers/writers from multiple vendors. These foundations are scalable even for systems incorporating multiple readers/writers that are to be introduced in the future. This approach also offers compatibility with future technical innovations in the RFID technology without changing the applications.
- 2)Location Information Middleware
This middleware is used to convert simple ID information detected from the RFID reader/writer into location information and forward it to the application.
- 3)Integrated Asset Management Database
This is a tool for making full use of the asset location information by managing it together with other information in an integrated manner. Thanks to this arrangement it becomes possible to obtain added value.
- 1)
- (2) Expertise Accumulated via Previous Solutions
NEC is leading its competitors in starting to tackle asset management solutions based on RFID technology and it has already accumulated significant expertise on the application of this technology. This is a result of the constant endeavors of NEC to provide a software infrastructure to match the environment of each customer.
6. CONCLUSION
- 1)NEC’s asset management solution has the aim of offering added skills for the solution of customers’ management problems, including security, compliance and effective asset utilization.
- 2)NEC has been leading other manufacturers in the provision of software solutions for solving current management problems, based on the RFID technology.
- 3)NEC will continue its efforts for the provision of asset management solutions for the future by making full use of its management expertise, including the use of RFID technology.
ACKNOWLEDGMENTS
The authors would like to express gratitude for the kind cooperation of the following persons in the compilation of this report:
- 2nd Computers Software Division, Chief Manager Mori, Product Manager Uchida and Expert Matsuda,
- Ubiquitous Platform Development Division, Senior Manager Ichinose,
- Market Development Division, Chief Manager Murayama.
Authors’ Profiles
Toshiyuki TSUJI joined NEC Corporation in 1994 and is currently in charge of the development of 2nd Computers Software Division.
Masao IGUCHI joined NEC Corporation in 1992 and is currently in charge of the development of RFID solutions.
Seiji KOUNO joined NEC Corporation in 1993 and is currently in charge of the development of basic software for implementing solutions based on RFID.
Narihiro MISU joined NEC Corporation in 1981 and is currently in charge of the development of RFID solutions.
Jun NOGUCHI joined NEC Corporation in 1989 and is currently in charge of the development of RFID solutions.
Masao KAWAMURA joined NEC Corporation in 1976 and is currently in charge of the development of RFID solutions.