Global Site
Breadcrumb navigation
World's Leading Symmetric-Key Cryptography Research:Kazuhiko Minematsu
Featured TechnologiesMarch 27, 2019

Researcher Kazuhiko Minematsu ( Profile ) has continued to produce world class research results for many years in the area of symmetric-key cryptography. We spoke with him about the role of cryptographic technology in society, how it has evolved, and his research results to date.
Cryptographic technology increasing in importance throughout the world
― How is cryptographic technology utilized within society?
Cryptography is a technology which is currently used in every form of communication including the internet and mobile phones. In addition to the symmetric-key cryptography that I research, cryptography includes various technologies such as public key cryptography, hash functions, and digital signatures, but it is safe to say that some form of cryptographic technology is employed in the communication methods that we typically use. Cryptography is the most deeply rooted technology which supports a wide variety of security technologies.
The shift toward IoT is now advancing around the world, and various devices are being connected to the Internet. As a result, security will be needed in previously unforeseen situations. For example, the need for a lightweight and stable cryptographic technology that can be equipped even in a small device is an area which is dramatically increasing. Furthermore, cryptography is also used in blockchains, which are currently receiving a lot of attention, and it is also an important factor which influences the performance. Cryptography continues to be a prominent technology throughout the world.
When it comes to symmetric-key cryptography, it used to be a field which required a significant amount of craftsmanship mainly by industry researchers, but in recent years many technologies have been theorized, and it has become systematized as a field of study. It has perhaps become an area ready for young people to research.

Senior Principal Researcher
Doctor of Science
Secure System Research Laboratories
Developing cryptography methods that streamline calculations up to theoretical limitations
― What types of research and development have you conducted on symmetric-key cryptography?
During my student years, I originally majored in information theory and statistics. I started the symmetric-key cryptography research three years after joining NEC. I felt that it was a research theme that suited me and selected it in consultation with my boss at the time. That being said, it was a completely new field for me, so it took a lot of time to acquire the relevant knowledge. I remember doing nothing but reading research papers at work for about a year and a half.
After that, it took several years before I was able to finally write a research paper, and the message authentication method that I submitted to the CRYPTREC Japanese cryptography standards list was posted to the recommended candidates list. This was probably the first major result that I achieved in my cryptography research career.
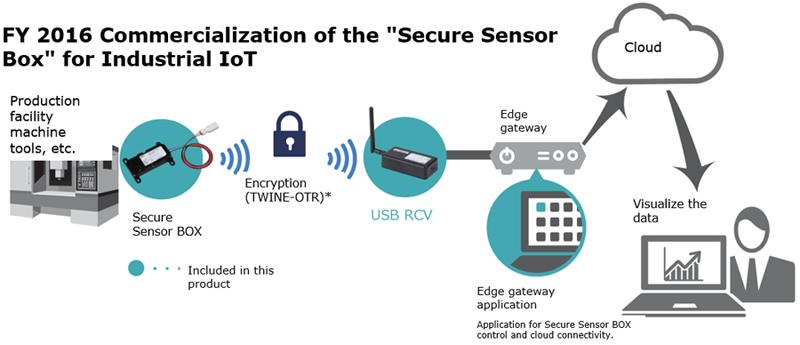
After that achievement, I continued to conduct various types of research, and one topic that I can point out is the development of the "TWINE" lightweight block cipher. This result was undertaken together with a colleague of mine at the time, and we improved the classical approach to create ciphers called a generalized Feistel structure using our own method. We succeeded in developing this method in 2012. However, I believe that the technology can still be said to be one of the world's best lightweight block ciphers. Its advantages are a smaller hardware footprint than the standard AES cipher and high-efficiency on software.. For those reasons, it is extremely compatible with IoT and is being equipped in the IoT products that NEC is currently deploying.
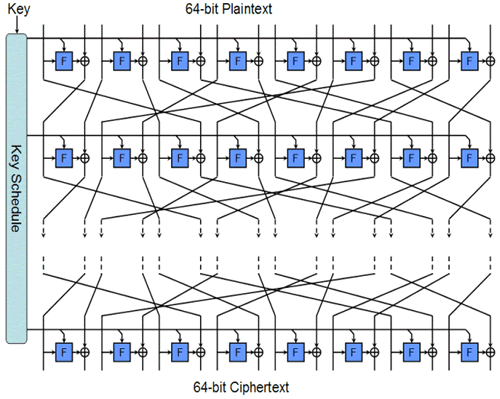
In addition, the "OTR (Offset Two-Round)" authenticated encryption was also a significant result. "Authenticated encryption" is a type of symmetric-key cryptography, and it is a technology which can simultaneously perform encryption and authentication. Because you cannot determine whether decrypted plain text has been manipulated with a plain encryption, the risk inevitably increases. Therefore, the introduction of authenticated encryption is needed in situations which require a high degree of security such as IoT. However, because authenticated encryption performs message authentication in addition to encryption, it almost doubled the computation cost, which is a problem. In contrast, OTR streamlines the computation to an extreme degree through custom processing called two-round Feistel encryption. Because the encryption and decryption is computed within the same processing system, the computation cost is almost the same as the encryption alone. In other words, we have reached the theoretical limit. Because OTR uses a block cipher as its internal module, if we use Twine instead of the standard (AES), we can expect further performance gain. NEC is currently combining the two cryptography technologies as "TWINE-OTR" and starting to implement it in IoT and other products.
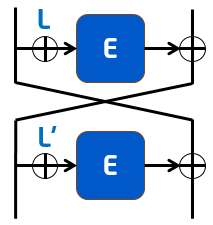
"TWINE-OTR" authenticated encryption
Verifying the logic and pointing out the flaws in cryptography that is spreading around the world
― What kinds of activities are you engaged in to develop safe cryptography?
To tell you the truth, the job of a cryptography researcher is not just about developing cryptographic technologies. Analyzing the security of published cryptographic methods is also an important area of research required of cryptography researchers. Analyzing cryptographic technologies published by other research institutions, discovering the logic gaps and presenting at conferences is extremely significant for the progress of science as a whole and the safety of society. Perhaps it can be said that analyzing cryptography that is already being used in society to confirm the safety and risks is the social responsibility of cryptography researchers such as myself.
For example, there is the GCM authenticated encryption method which is certified as a standard by the U.S. National Institute of Standards and Technology (NIST) and used around the world. Through collaborative research with Nagoya University, I discovered a defect in the security proof for this method and presented at CRYPTO 2012, the top cryptography conference. The research paper which refined this evaluation received the award for best paper at FSE 2015, the top conference for symmetric-key cryptography.
Likewise, in 2018 I jointly analyzed an end-to-end encryption method shown in the white paper of a famous social networking service together with the University of Hyogo, presented at the ESORICS 2018 international conference, and also received the innovative research paper award at SCIS 2018, the largest conference in Japan.
Furthermore, there is the widely known OCB2 authenticated encryption method, which is also an ISO standard. In November of 2018, I discovered a problem in this cryptography method together with a young researcher. When this research was published as breaking news, the report became a major issue within the community. Because it was a well-known cryptography method that was thought to have absolutely no problems, I couldn't believe it at first when we discovered the problem.
All cryptography researchers take an earnest posture to ensure the safety of society and to advance cryptography as a science. Following the mathematical logic and analyzing the security proof for each cryptographic method to verify the logic is also an important part of our research.

― What are your future goals?
Cryptography is a research field which is currently becoming commoditized. For example, going forward it will probably be difficult for some time for the field of symmetric-key cryptography to achieve significant advances in performance such as suddenly speeding up by ten times. However, for this very reason I think that cryptographic development with features that other researchers would not conceive of has great significance. Currently, I am engaged in research using various approaches to see whether a new form of cryptography could be developed and commercialized on its own.
Moreover, NIST started a new authenticated encryption competition. Winning this competition means that your entry will become a global standard, so creating an authenticated encryption scheme which is adopted here and used throughout the world is currently my primary objective.
- ※The information posted on this page is the information at the time of publication.
