Global Site
Breadcrumb navigation
Secure computation technology for analyzing data with the information concealed
Featured TechnologiesJuly 23, 2019

With secure computation technology, highly sensitive data can be analyzed with their contents concealed. We spoke with developer about the details and advantages of this technology.
Results of computation are output, while the contents of the data remain concealed using high level of security

Assistant Manager
Secure System Research Laboratories
― What kind of technology is secure computation technology?
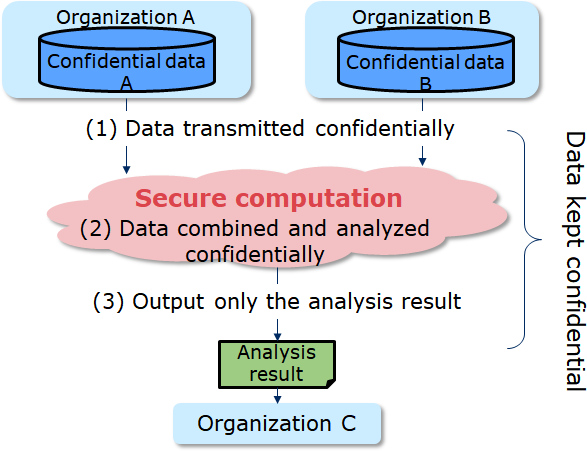
With this technology, users can perform computations while the data is still concealed. Users performing computation cannot observe the contents of the data, they can only access the results of the computation that are output. This makes the technology effective when working with personal data, trade secrets, and other confidential information.
While there are several ways to perform secure computation, we work with a method based on secret sharing. In this method, data is divided into multiple pieces, each of which is then distributed to a few servers for calculation. The data is randomized to maintain concealment, and dividing it into multiple servers makes the possibility of restoring it to its initial state extremely difficult, enabling users to maintain a high level of security. This technology is expected to be used for handling personal information, bio information, and corporate confidential information.
Secure computation using the secret sharing method is a field in which NEC has become a world leader. In fact, according to a research paper NEC published in 2016, this technology has successfully raised processing throughput to approximately 1.3 million, when in the past it was limited to 90,000*1. This paper was awarded Best Paper at the ACM Computer and Communications Security 2016, one of the world’s top class international security conferences. This resulted in research in this area flourishing around the world. You could say that we are truly pioneers leading the research on this technology.
And improved throughput is not the only advantage of NEC’s secure computation. Our technologies combine high safety and ease of development. They are being developed through collaborative research with Bar-Ilan University in Israel.
For safety, we use a unique technology that detects anomalies and irregularities in servers. With secure computation, multiple servers cooperate on computations, but it is impossible to eliminate all risk of irregularities or anomalies in every one of the servers. Nonetheless, detecting these sorts of irregularities quickly and accurately is extremely important to prevent danger. Our research paper on our independently developed detection technology was accepted at both Eurocrypt 2017 and IEEE Security & Privacy 2017—two other top class international security conferences—and received praise for the technology’s high safety and reliability.
We are also engaged in research with regards to the ease of development. In 2018, we built a development environment that makes it easier to create secure computation programs (November 5, 2018 press release link https://jpn.nec.com/press/201811/20181105_02.html). This makes it possible to do such things as complete work in just a few days using general system engineers, when it would previously have taken experts a month to do. The key point of this environment is that users can utilize a programming language resembling Python, a language widely used in machine learning. This research paper was also accepted at the ACM Computer and Communications Security 2018.
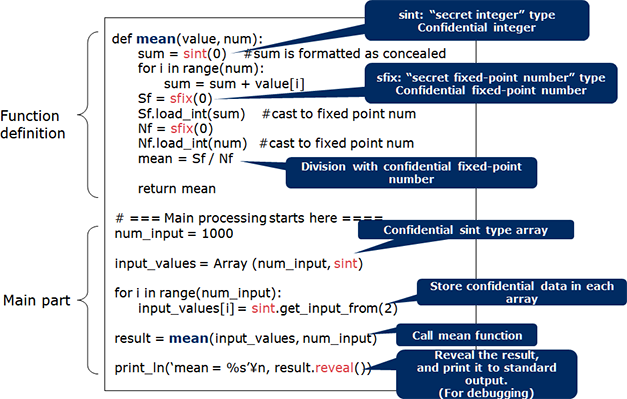
(Processing that calculates the mean)
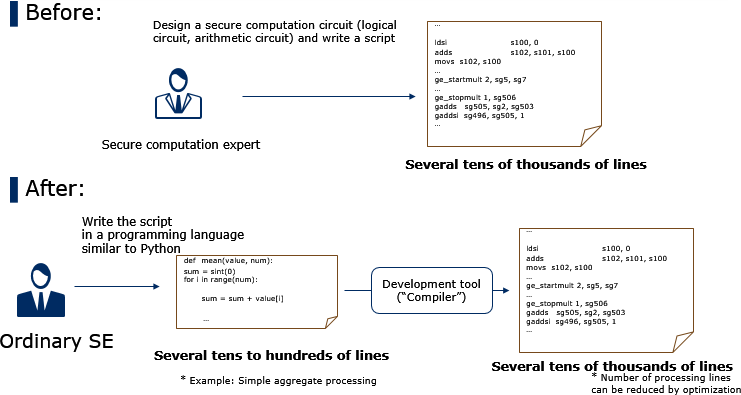
This development environment and a portion of source code of the execution engine are currently available to the public. I don’t think any other corporation in the world has published source code relating to their secure computations. I believe that in addition to publishing research papers, it is also important to make source code publicly available so that its performance can be evaluated and its safety verified. I hope everyone gives it a try.
( https://github.com/nec-mpc)
https://github.com/nec-mpc)
It would be great if users found utilizations that we didn’t consider, making this research even more exciting.
- ※1:Compared with semi-honest secure three-party computation.
Integrating genome information held by multiple medical institutions for analysis
― What kinds of things are you planning on applying it to?
The first step is application to medical research. Through collaborative research with Osaka University, we were recently able to demonstrate the practicality of this technology toward genome information analysis.
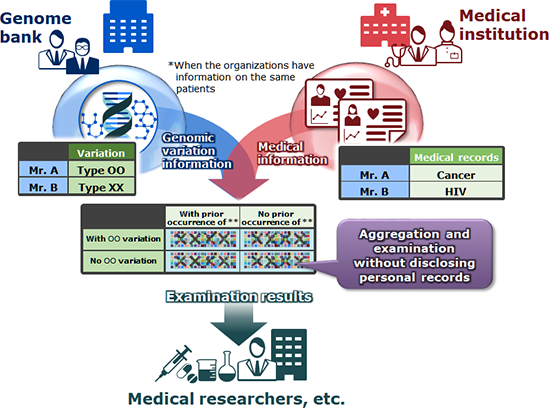
Genome analysis, the research into which is being carried out in the medical area, requires a large volume of genome information. However, genome information is highly sensitive data. Genome information remains the same for your entire life; it can’t simply be changed like an ID or a password. Not to mention the same information can affect both a parent and their child. Furthermore, it may reveal high susceptibility to certain diseases, so leaks are out of the question. What was needed was a way of collecting data while also ensuring it remains concealed.
To this end, NEC collaborated with the Graduate School of Medicine at Osaka University to verify the practicality of using secure computation in applications for integrated analysis of genome information held by multiple medial institutions. This would allow users to connect genome information that was once enclosed within the walls of their respective medical institutions and analyze large volumes of data all together. And of course, secure computation by way of secret sharing is used to prevent the contents of the data from being seen during processing. Furthermore, the system is made so that only the total value is output, and only when that total value exceeds a set number of patients fitting certain conditions, preventing privacy violations from the aggregate results. Research demonstrated the ease of development and the high processing speed, showing that the genome information of approximately 8,000 individuals could be analyzed in about 1 second, gaining high evaluation for the practicality of the technology from the professors of Osaka University.
In the future, we are also considering application of this technology in information banks. An information bank is a system in which individual citizens consent to providing their personal information for use in marketing and other purposes, and receive benefits for doing so. This system was born out of the idea that management of personal information, which has typically been controlled by corporations, should be returned to the individual. Financial institutions certified to operate this system have recently started appearing in Japan as well.
The information is obtained from individuals, so absolute confidentiality must be guaranteed in order to gain their trust. Using secure computation ensures that data from individuals can’t be identified even by information banks. We therefore believe that secure computation will become a key component of information management going into the future.
We are also considering combined applications with NEC’s strong technology. For example, NEC leads the world in face recognition and other forms of biometric authentication, which are highly compatible with secure computation.
Furthermore, we believe that new possibilities will emerge when combined with analytic technologies like heterogeneous mixture learning. Until now, analytic technologies such as these could only handle data within a single organization. This is because such data contains trade secrets, and therefore couldn’t be shared with other corporations or organizations. However, with secure computation, data from multiple organizations can be computed all together. An unprecedented volume of trade secret data can be used for analysis while maintaining its confidentiality, so it may be possible to obtain new findings.
Using confidential information to solve social problems instead of profit corporations
― What issues will you tackle in the future?
We think that proposing the formation of new standards and establishment of new legal systems will also become more important. Secure computation is a new technology that was never considered in societies of the past. Therefore, it may be difficult for use of this technology to spread under existing legal systems. This is true not only in Japan, but all over the world. NEC is currently in discussions with competitors, university professors, government officials, and legal experts as we lead work on designing new systems.
It is our belief that using secure computation to safely share personal information contained within individual corporations as an asset for society as a whole and create useful systems will have a significant impact. After all, this will mean that the information can be used to solve social problems, rather than simply profiting corporations. As researchers, we are committed to properly sharing information on our technologies with the rest of society. I look forward to this leading to further discussions throughout the world.

- ※The information posted on this page is the information at the time of publication.
Contact below for review and demonstration of applicability
NEC Central Research Laboratories, Research Planning Division
Contact
More on NEC's secure computation
Research Papers (International Conventions)
- T. Araki, A. Barak, J. Furukawa, M. Keller, Y. Lindell, K. Ohara and H. Tsuchida. "Generalizing the SPDZ Compiler For Other Protocols". ACM CCS 2018.
- Jun Furukawa, Yehuda Lindell, Ariel Nof, Or Weinstein, "High-Throughput Secure Three-Party Computation for Malicious Adversaries and an Honest Majority", EUROCRYPT 2017.
- Toshinori Araki, Assi Barak, Jun Furukawa, Yehuda Lindell, Ariel Nof, Kazuma Ohara, Adi Watzman, Or Weinstein. "Optimized Honest-Majority MPC for Malicious Adversaries - Breaking the 1 Billion-Gate Per Second Barrier", IEEE S&P 2017.
- Toshinori Araki, Jun Furukawa, Yehuda Lindell, Ariel Nof, Kazuma Ohara, "High-Throughput Semi-Honest Secure Three-Party Computation with an Honest Majority", ACM CCS 2016. (Best Paper Award)

 Explanatory material for NEC's secure computation
Explanatory material for NEC's secure computation