Global Site
Breadcrumb navigation
Lightweight-architecture tamper detection technology to protect IoT devices
Featured TechnologiesApril 2, 2018

In recent years, we have been seeing progress in the utilization of IoT for an efficient operation of social infrastructure systems. To give some examples, smart factories are aiming to streamline production by leveraging IoT, and smart cities are promoting efficient urban management through the use of IoT. Most of these IoT devices are currently incapable of introducing security measures because their CPU speed and memory capacity are limited compared to computers and servers. For example, while several tens to hundreds of megabytes of memory space are required to run an average anti-virus software, only few IoT devices satisfy that requirement.
On the other side, cyber attacks are beginning to target not only servers and computers, but also IoT devices. For instance, fatal damage can be predicted as an outcome of attacks on IoT devices at a chemical plant. Attacks on the IoT devices of a manufacturing plant can give rise to concerns about product design information leaks and defective manufacturing.
In the past, security incidents such as those below have occurred in different parts of the world.
- Pipelines in Turkey were attacked, causing explosion (2008)
- Nuclear facilities in Iran were attacked, causing delay in nuclear development (2010)
- Ironworks in Germany was attacked, which stopped its operation (announced in 2014)
In 2016, malware MIRAI inflicted enormous damage to Web hosting service providers and DNS service providers worldwide, infecting millions of IoT devices, including routers and smart home appliances.
Cyber attacks committed through the Internet are globally targeted and cross borders. It is essential for the safety and security of society to protect IoT devices from such cyber attacks and ensure stable operation of social infrastructures.
Attacks on IoT devices can be categorized into two groups: attacks on the communication between IoT devices or with servers (sniffing and alteration of communication content), and attacks on the IoT devices themselves. We already have technologies that protect servers, IoT devices, and the communication among them from tampering or detect such threats. However, we are still in the process of developing technologies that can provide strong protection for IoT devices against cyber attacks and those that can detect attacks on IoT devices in order to minimize damage from attacks.
In response to this situation, NEC developed high-speed tampering detection technology that can also be applied to IoT devices with significantly lower-memory capacity and lower CPU speed compared to servers and computers. This now enables instant detection of any tampering with an IoT device, which can further make it possible to isolate any tampered devices and take measures for recovery swiftly.
Features of the new technology
-
Fast tampering detection with no impact on device operations
Conventional tampering detection spends too much time on checking the entire software, which makes it practically incapable of real-time tampering detection. The new tampering detection method that NEC developed achieves high-speed tampering detection with no impact on device operations by inspecting each segmented function of the software as needed. In addition, the constant real-time inspection can ensure higher security even for IoT devices operating over a long term compared to Secure Boot, which uses Trusted Platform Module (TPM) known for start-up inspection.
Specifically, NEC's new technology monitors control commands transmitted to devices from the server and scans executable codes of the function corresponding to the respective commands in real-time. As an example, when a device with functions A, B, and C as shown below receives a command to use function C, only function C is scanned, reducing inspection time by skipping the scanning of functions A and B. We demonstrated with our prototype that a function with an implementation size of 2 KB can be scanned in about 6 msec. The minimized impact on IoT device operations now enables the technology's application to equipment that does not tolerate delay, such as conveyor robots.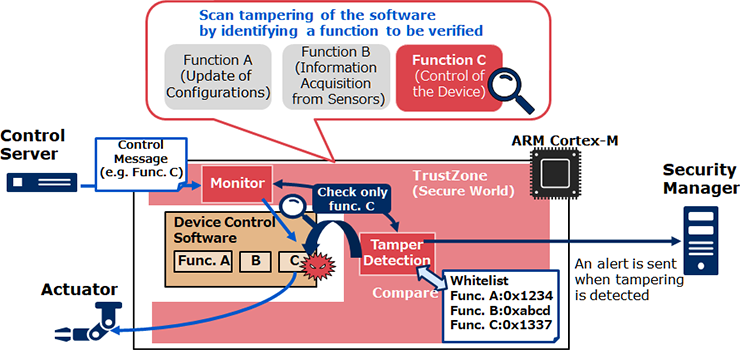
-
Achieving both the protection of the tampering detection function itself and a lightweight architecture
NEC implemented the tampering detection function using ARM Cortex-M's TrustZone function. TrustZone is a function that creates a protected area in the memory. Attacks on the tampering detection function itself, even some that disable the function, can be prevented by using this function. Additionally, thanks to not needing to introduce it as another piece of software as a protective mechanism for the tampering detection itself, the program's architecture can be made lightweight.
In our prototype, we demonstrated that a tampering scanning function, a white list, and a server notification function can be implemented on a total memory of 4 KB or less. This enables this technology's application even to sensors, which have very limited memory size.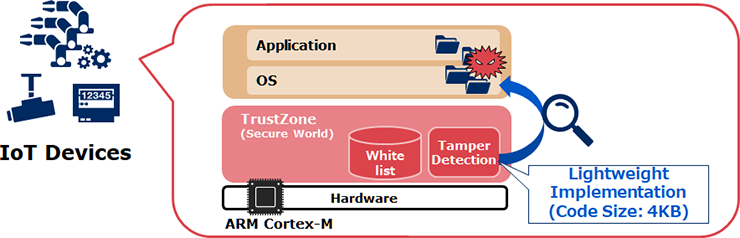
Today, we are seeing an increasing number of "smartization" using IoT in various fields, including plants, cities, household appliances, and automobiles. NEC will continue to contribute to "smartizing" the society through dispelling security threats for IoT devices.
- *Company and product names mentioned herein are the trademarks or registered trademarks of their respective owners.
- ※The information posted on this page is the information at the time of publication.
