Global Site
Breadcrumb navigation


NEC Secure Computation
Secure Computation for data utilization
Secure Computation is a technology enables computational processing with encrypted data in secure computing environment. NEC Secure Computation provides flexible uses for corporate marketing activities based on purchase history and people-flow data. It also enables secure data distribution outside the organization in fields such as finance, medical and healthcare, manufacturing, and government agencies handling a huge amount of personal data and trade secrets.
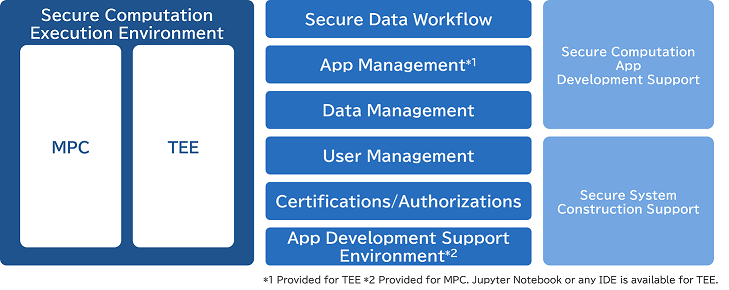
Achieve both Security and Utilization of Data
In recent years, DX has been progressing rapidly in various fields and there is a growing movement to gain new insights by utilizing confidential information in companies such as personal data and trade secrets. On the other hand, providing data to other companies has safety issues in the use of confidential information such as concerns about information leakage and unauthorized use.
Secure computation enables data analysis in highly confidential fields such as financial, medical, and plant operation, marketing businesses, "information banks" manage/provide information and cross-organization data analysis through collaboration between the same and other industries. Based on its extensive experience and achievements in building large-scale, mission-critical systems, we make proposals that consider the data safety throughout the system. From the conceptual phase to actual operation of a system using secure computation, we provide comprehensive support for customer's environment.
What is "Secure Computation" processes encrypted data?
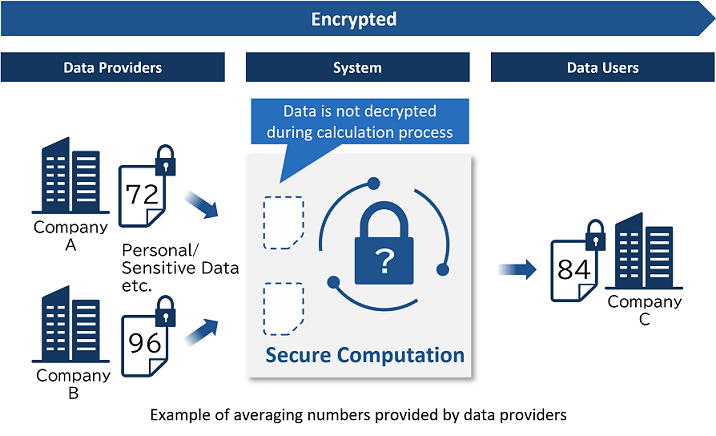
Since conventional computational methods require temporary decryption the data during processing, there is the risk of data leakage. Secure computation enables you to obtain only the calculation result while remaining the data encrypted without directly referencing the raw data in a secure computing environment.
Features
NEC Secure Computing has the following three features:
1. Supports multiple secure computation methods
There are several methods for secure computation. NEC offers Secret Sharing method (MPC*1) and Hardware method (TEE*2). We propose the suitable method according to the safety and processing speed required by the application.
- *1MPC:Multi-Party Computation
- *2TEE:Trusted Execution Environment
2. Easy development of secure computing applications
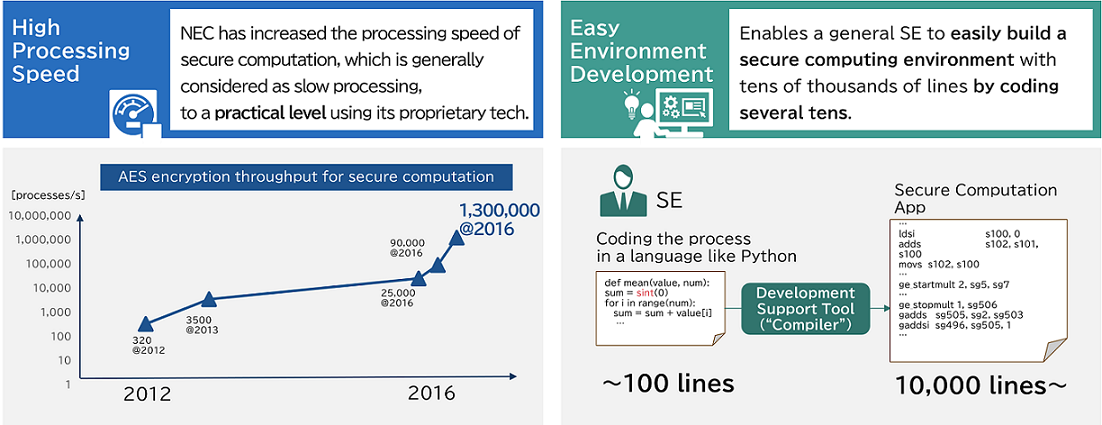
Developing secure computing applications requires a high level of expertise in general. NEC provides its own development environment to shorten the development period.
3. Consulting and total integration capabilities
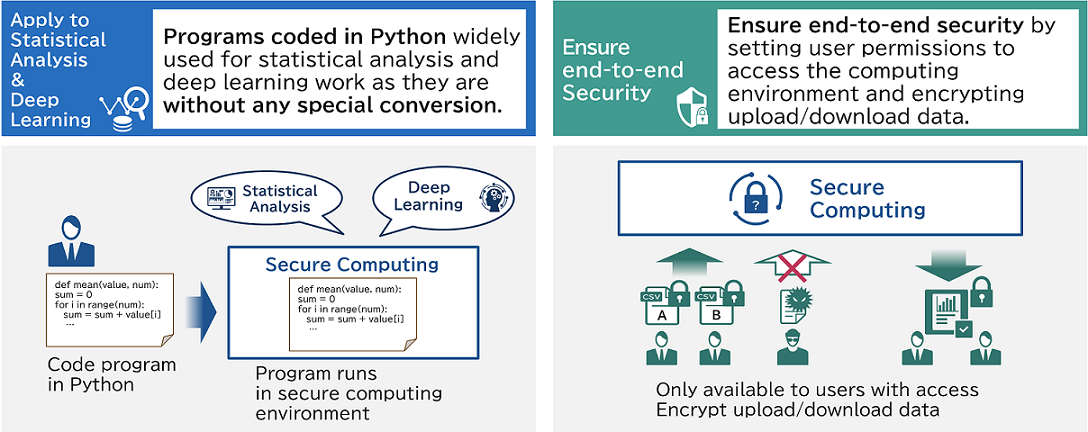
Handling confidential data requires to build a system that is highly secure and trusted by data providers. It is important not only to introduce secure computation, but also to ensure safety throughout the system.
NEC proposes systems with those knowledges of consulting capabilities to implement cybersecurity measures from the design stage and total integration capabilities to realize large-scale, mission-critical systems.
Multiple methods for Secure Computation
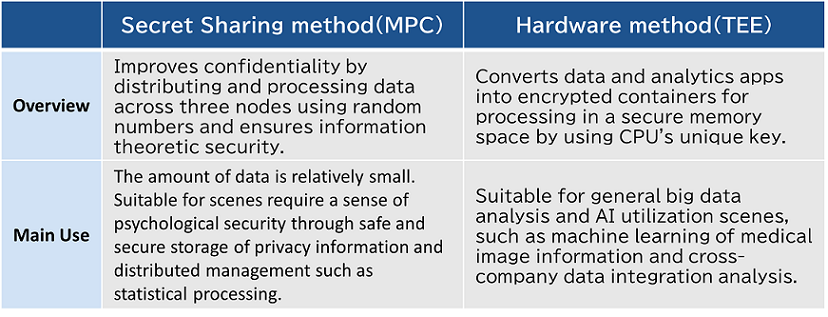
NEC offers Secret Sharing method (MPC) and Hardware method (TEE).
We propose the optimal method according to the safety and processing speed required for the application; MPC for scenes where multiple companies bring data together and perform more secure analysis such as in the fields of finance, medical care, healthcare, etc., and TEE for scenes where analysts try and error various analysis methods, such as using existing analysis applications and learning models on public clouds.
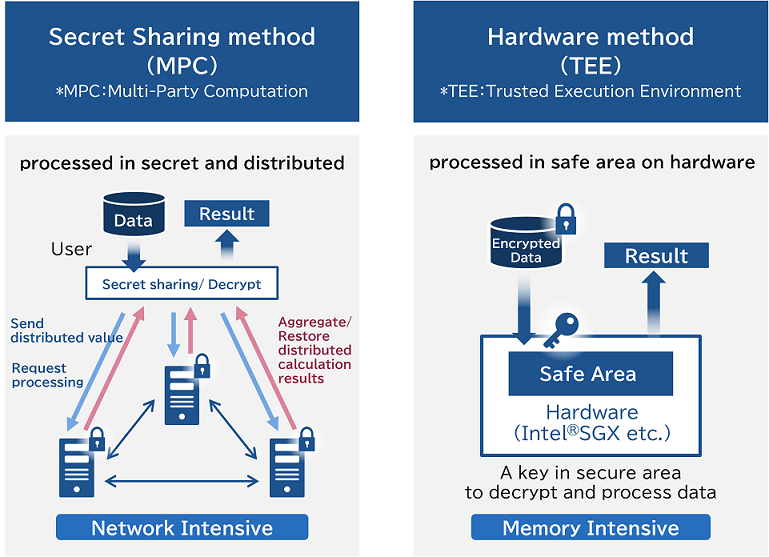
Secret Sharing method(MPC)
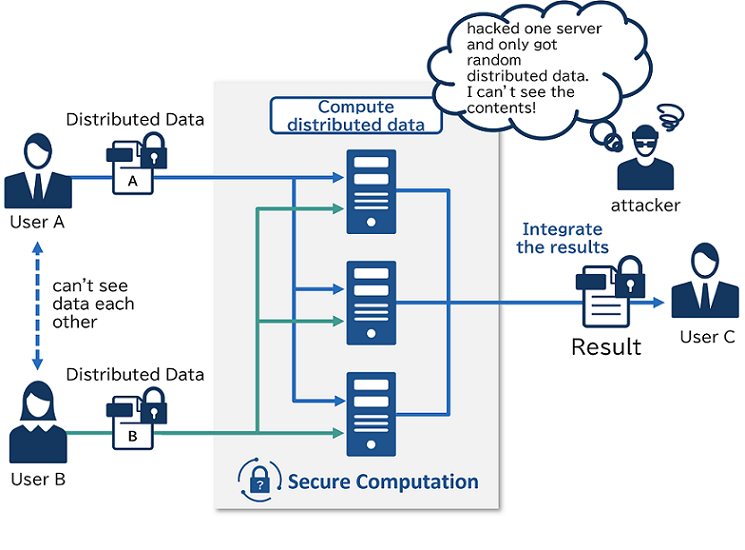
In MPC, data is encoded in random numbers and distributed to three servers.
These three servers cooperate with each other to perform arbitrary calculations with encrypted data. Even if one server is hacked, the hacker would only get random distributed data and not be able to get the original data.
Although MPC is generally considered as slow processing, NEC has increased the processing speed to a practical level in some processes using its proprietary technology. We also provide NEC’s unique development support tool makes it easier to develop secure computing applications used to be considered difficult even for general system engineers to program using this method. In addition, we are expanding the library for secure computing applications to shorten the development period.
Hardware method(TEE)
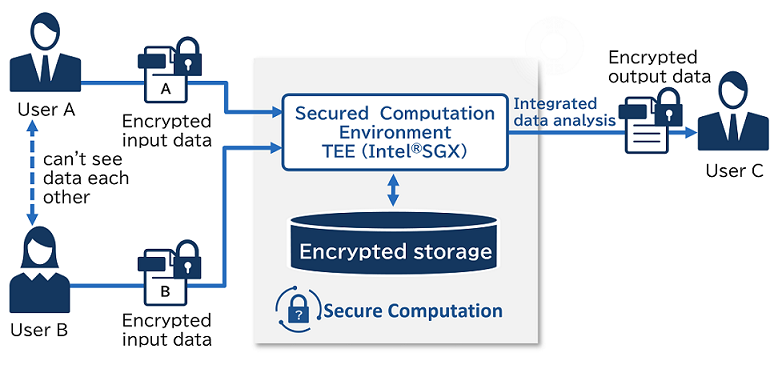
TEE uses hardware security technology (Intel ® SGX) to perform calculations using the secure memory space on the server.
In collaboration with Intel and Fortanix, NEC has made it possible to easily describe SGX programming, which is generally difficult to understand, using Python used in a wide range of fields such as statistical analysis and machine learning. This contributes to reuse existing applications developed in Python.
Cases
The followings are scenes where secure computation is expected to be used in practice.
- *The use cases are assumed and do not guarantee feasibility or effectiveness.
- *In accordance with the Personal Information Protection Law, the prior consent of the data provider is always required for the collection and use of data (including provision to a third party).
Gain insights using third-party data
Digital Marketing
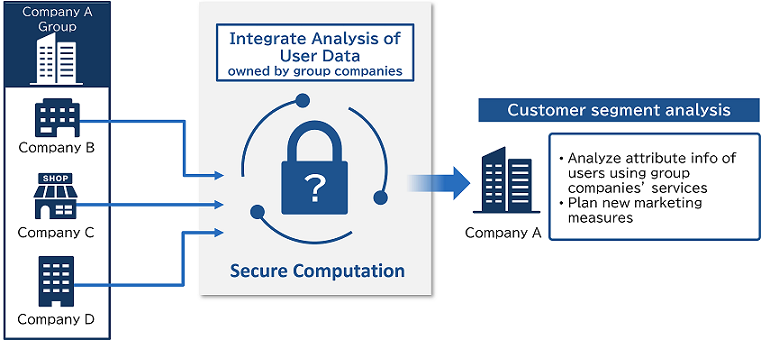
There is an issue among group companies that user data owned by each company cannot be provided to other companies. Secure computation enables integrated analysis of user data of group companies and precise analysis of customer segments, making it possible to plan new marketing measures according to user attributes.
Provide data analysis services
Maintenance of industrial equipment (predictive detection)
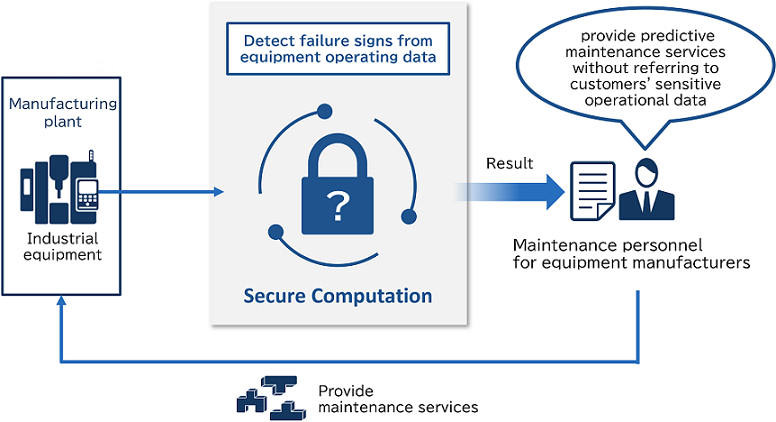
Since operating data of industrial equipment is sensitive information, there is a problem that it cannot be provided to the manufacturer. Secure computation makes it possible to provide predictive maintenance services by detecting signs of failure without directly referencing to the customer's operating data.
Personal Credit Service
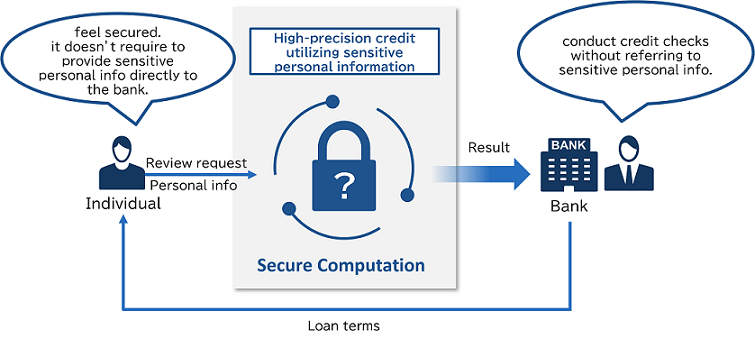
There is a problem that financial institutions do not provide sensitive personal information for credit in the preliminary screening. Secure computation enables financial institutions to review sensitive personal information without directly referencing and it is expected to acquire new customers by lowering the hurdle at the time of application. High-precision credit also could personalize loan terms.
Data analysis by consortium (inter-organizational collaboration)
Supply chain optimization
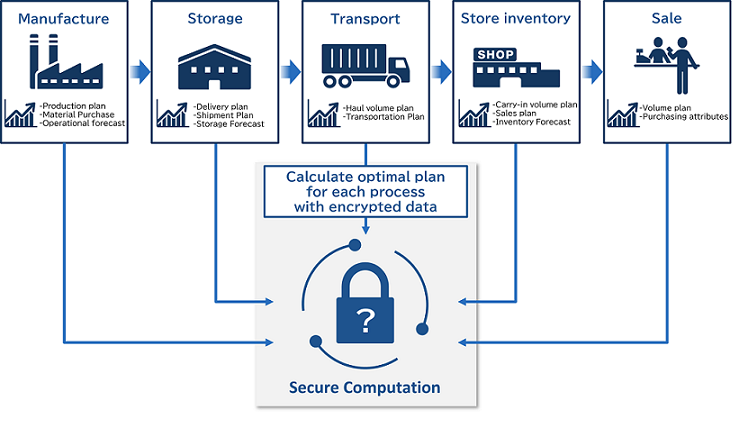
Among the companies making up the supply chain, there is a problem that planning data, which is a trade secret, should be closed to the outside. Secure computation encrypts and calculates the data that occurs in each process in the supply chain, allowing different companies to calculate the optimal plan for each company without disclosing the data.
Visualization of cost-effectiveness in shopping districts
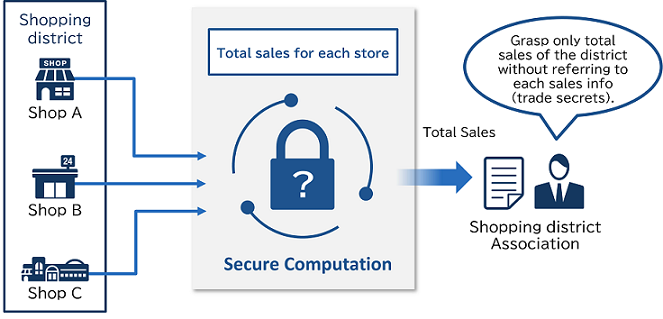
Although the associations in shopping districts need to calculate cost-effectiveness of measures such as events, there is a problem that individual sales information for each store cannot be provided. By using secure computation, it is possible to calculate the cost-effectiveness precisely by adding up the sales of each store.
News
Related Links
English
- *Intel, Intel SGX are trademarks or registered trademarks of Intel Corporation or its subsidiaries on the US and other countries.
- *Other company names or product names on the website are trademarks or registered trademarks.
