Global Site
Breadcrumb navigation
Biometric Based Digital Signature Fundamentally Solves the Risks of Managing Face Information and Private Keys
Featured TechnologiesFebrualy 26, 2025

The use of face recognition is currently spreading worldwide. However, a major concern for system operators is the management of sensitive facial information such as face images and facial features extracted from them. In addition, users are often reluctant to register their facial information due to concerns over how companies will manage it.
To address this situation, NEC recently developed a new authentication method that does not require the management of facial information. The biometric based digital signature technology, which is the basis of this method, can also be utilized in digital wallets, reducing the management risk of digital assets such as cryptocurrencies. We spoke with our researchers to learn more about this technology.
Achieving face recognition without the need to manage facial information

―Please tell us about the biometric based digital signature technology that NEC recently announced.
Iwai: It is a technology that enables face recognition without using facial information itself, but rather by using a key generated from facial information. Since this technology eliminates the need to manage facial information, it enables the operation of more secure face recognition systems at a lower cost than before. Facial information, which cannot be replaced, is highly sensitive data that requires extremely strict management. If such information were to leak, it could cause irreversible damage. In contrast, if the key is leaked, it can be changed, so the level of safety and security is significantly improved. Since it is no longer necessary to prepare a robust security system specifically for facial information, the hurdles to adopting face recognition can be mitigated. At the very least, there is no longer any need to hesitate in introducing of biometric recognition due to the need to manage facial information.
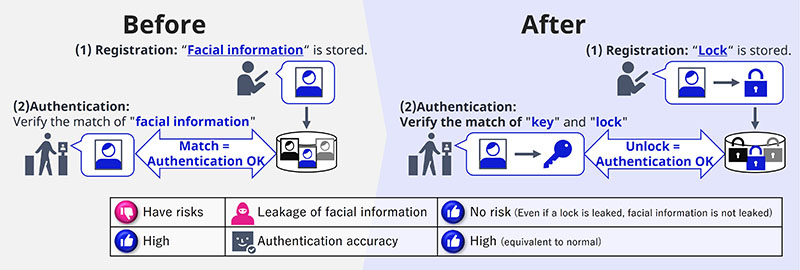
Tamiya: The main technical challenge we faced was the "fluctuation" inherent in facial information. Facial information can vary depending on the angle at which the photo is taken, lighting conditions, facial expressions, and so on. In contrast, the keys remain unchanged despite these fluctuations. With conventional face recognition, the registered facial information is compared with facial information captured during authentication to calculate the similarity. The fluctuations are absorbed in measurement of the similarity. However, converting facial information into a key makes it difficult to accurately measure the similarity. Therefore, the accuracy of face recognition will be compromised. That was one of the major challenges for us.
The breakthrough came with the development of a technology that estimates the similarity even when facial information is converted into a key. This technology enables face recognition without the need to manage facial information while maintaining the accuracy of the face recognition engine. We anticipate a variety of use cases for this technology. Naturally, it can enhance security in the financial sector and make face recognition easier to operate at individual retail stores. In addition, we are also considering applications in mobility sector, where increasing connectivity is expected.
Higo: NEC is engaged in AI-based drug development, and we are also advancing proof-of-concept studies in this area. The technology is utilized in the development and administration of personalized vaccines for cancer patients. These vaccines are developed based on the genomic analysis of each individual patient and must be accurately administered to the correct patient. Therefore, we are now working to develop a system that utilizes this technology to ensure accurate and secure vaccine administration. Although personalized vaccines are still in the clinical trial stage globally, we hope to further our research to enable practical demonstrations of this technology, including applications in real-world clinical settings.
Achieving high speed authentication

Assistant Manager
Secure System Platform Research Laboratories
― Would it be accurate to say that you added a step to conventional face recognition that converts facial information into a key?
Tamiya: Yes, that is the concept. For this reason, there was an issue of reduced speed due to the additional step.
The technology I mentioned earlier is also effective in this context. Because it allows us to estimate the similarity while converting facial information into a key, we are able to narrow down the candidates of possible matches. Normally, one would need to compare the key generated from facial information with all registered keys. However, since we can now measure the similarity, we are able to exclude data that is clearly different from the matching candidates.
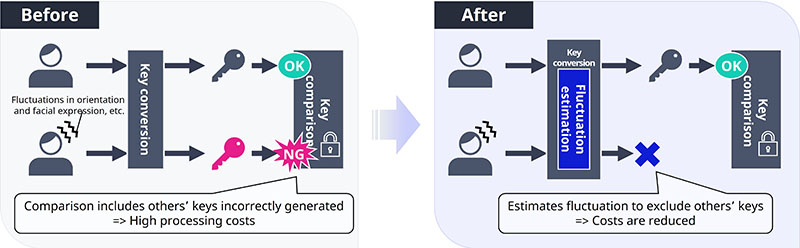
Sugizaki: In addition to algorithmic improvements, we also worked on improving speed from the implementation side. For example, one major challenge was the large size of the face image data to be captured during authentication. Since face images are quite large, transmitting them can be time-consuming. To address this, we developed and added a function to reduce the image size to an optimal level sufficient for authentication. We also optimized performance at various layers, such as efficiently connecting the C++ used for the cryptographic algorithms with JavaScript used for the user interface in the browser.
Through trial and error, I believe we have achieved a user experience that is comparable to conventional face recognition. You can experience a demonstration of face recognition using our technology in the Digital ID and Smart Work DX Reference Office on the 24th floor of the NEC headquarters building. It allows you to see the actual speed and accuracy of the technology, so I hope that many people will try it out.
Developing secure digital wallets for digital assets
Higo: To elaborate further, this technology is based on digital signatures. To put it simply, a digital signature is a kind of certificate proving that you possess the key to unlock a lock. In digital signature methods, the unique key that only a particular person possesses is called a "private key," and the digital signature serves as proof that you are the holder of this private key.
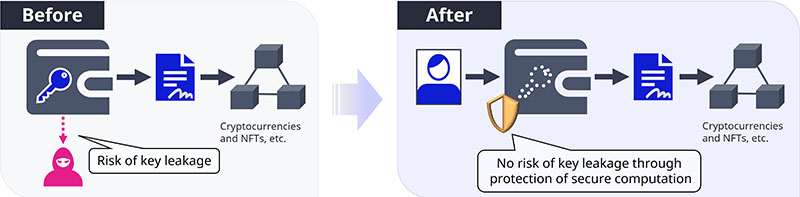
With our technology, we can generate this digital signature from facial information. It uses the aforementioned key generated with high accuracy from facial information as the private key but rather than generating the signature from this private key, it can directly generate the signature from facial information. We achieved this by developing a technology that generates the signature with secure computation technologies that enables computation while the data remains encrypted.
Therefore, the private key does not need to be stored, and is never present in system memory. Even if someone attempts to obtain the private key, it is secure because the private key does not exist in the first place. Furthermore, it is impossible to recover either the private key or facial information from the digital signature in the system.

Assistant Manager
Secure System Platform Research Laboratories
Tamiya: In addition, since this technology is directly based on the digital signature mechanism, it is compatible with services and systems that currently use digital signatures. For example, digital signatures are essential in the world of digital assets, such as cryptocurrencies and NFTs. You can use the services simply by scanning your face using your digital wallet apps.
Higo: Conventional digital wallets were designed to store private keys. They enable transfers by creating data proving your intent to send a certain amount of money to a specified recipient using the private key. However, with this technology, you no longer need to store the private key on a smartphone or other devices. There is no need to worry about losing access to your assets if you lose your smartphone since no private key stored on it. Instead of a randomly generated private key, you can issue a signature using your face, allowing digital assets to be managed more securely and properly tied to the individual.
Otsuki: We believe that this technology has great potential as a key management solution for digital wallets, and we are now actively working on standardization and promotion outside of NEC. BGIN (Blockchain Governance Initiative Network) is discussing the standardization of key management and governance schemes for digital wallets, and we are participating in this forum to promote and raise awareness of key management using biometric information. BGIN plans to release a white paper soon that compares this technology with existing digital wallets in terms of security, availability, and convenience.
Iwai: In order for our technology, which converts face and other biometric information into keys, to gain broader adoption, it is important not only to promote it to our customers but also to strengthen our presence within global standardization organizations. We will continue these efforts going forward.
A tech company integrating biometric recognition, security, AI, and communications

Researcher
Secure System Platform Research Laboratories
―Please tell us about the future prospects and goals for this technology.
Sugizaki: We would like to continue devising ways to accelerate the speed of this technology. Because the processing load increases as the scale of implementation grows, we need to pursue further acceleration with an eye on future large-scale, real-world deployments. Eventually, we hope to implement this technology in NEC’s walk-through face recognition systems.
Tamiya: I think that NEC's face recognition has already achieved a high level in terms of accuracy and speed. For this very reason, what will be needed going forward is a higher level of security, operational convenience, and other value-added features. In order to make NEC's face recognition technology available to even more people, we intend to continue research that incorporates our cryptographic technology.

Researcher
Secure System Platform Research Laboratories
Otsuki: In fact, facial information is currently the subject of active debate both in Japan and overseas as a type of data requiring special consideration. As we continue to advance this technology, we hope to develop solutions that can fundamentally address these concerns.
Higo: Yes, that is true. While biometric authentication is convenient, there are also those who do not want to use it because they somehow feel uneasy about it. I believe that biometric authentication is certainly an excellent technology, so I hope that our research and development can help people safely and securely use this technology in various fields.

Director
Secure System Platform Research Laboratories
Iwai: In that sense as well, NEC is a company that can achieve both convenience and safety in biometric authentication. We possess advanced technologies in both biometric recognition and security, and have our own research laboratories that pursue cutting-edge technologies in each of these fields. This technology was developed by four young researchers who are active at the forefront of global research.
Moreover, NEC is a globally rare company that can single-handedly provide a wide range of solutions, including AI, communications, and more. Since security will become an essential foundation in various areas such as generative AI and digital twins, which are expected to grow in the future, we intend to pursue research and development in a wide range of fields.


Biometric based digital signature that generates signatures from biometric information has been researched globally since the 2000s. However, issues such as reduced authentication accuracy and processing speed remained.
This technology newly developed by NEC maintains recognition accuracy and generates digital signatures from facial information without sacrificing processing speed. One of the key features is that, when converting facial information into a key, the system can estimate the same similarity as conventional face recognition systems. As a result, this technology achieves accuracy and speed that are comparable to those of conventional face recognition. Another major advantage is that digital signatures can be generated using facial information instead of a private key, making it directly applicable to the systems such as electronic contracts and digital assets. In addition, since the system does not store or manage facial information, security costs and risks during operation can be significantly reduced.
- ※The information posted on this page is the information at the time of publication.
Related information
- April 1, 2025 Press release
NEC has developed technologies that enable a secure workflow for personalized cancer vaccines and has proven their capabilities - February 26, 2025 Press release
NEC develops biometric based digital signature technology that enables face recognition without storing facial information
Related papers
- Haruna Higo, Toshiyuki Isshiki, Saki Otsuki and Kenji Yasunaga (Tokyo Institute of Technology), "Fuzzy Signature with Biometric-Independent Verification," 2023 International Conference of the Biometrics Special Interest Group (BIOSIG), 2023.
- Saki Otsuki, Hiroto Tamiya, Akito Watanabe (Tokyo Institute of Technology), Haruna Higo, Kengo Mori, Kenji Yasunaga (Tokyo Institute of Technology), Toshiyuki Isshiki, "Distributed Fuzzy Signatures based on Key-Homomorphic Signatures," 2024 Symposium on Cryptography and Information Security, 2024.
- Hiroto Tamiya, Haruna Higo, Toshiyuki Isshiki, Kengo Mori, Satoshi Obana (Hosei University), Saki Otsuki, "Distributed Fuzzy Signatures based on Two-Party Signing Protocols," 2024 Symposium on Cryptography and Information Security, 2024.
- Yukimasa Sugizaki, Saki Otsuki, Hiroto Tamiya, Akira Nakashima, Toshiyuki Isshiki, "A fast algorithm for closest vector problem over triangular lattice and its evaluation," 2025 Symposium on Cryptography and Information Security, 2025.
- Saki Otsuki, Hiroto Tamiya, Kengo Mori, Toshiyuki Isshiki, Shin’ichiro Matsuo (Georgetown University), Satoshi Obana (Hosei University), "Key Management for Digital Wallets Using Distributed Fuzzy Signatures," 2025 Symposium on Cryptography and Information Security, 2025.