Global Site
Breadcrumb navigation
NEC’s advanced technologies for data-driven society
Achieving both security and usability of personal dataOctober 1, 2020

How can we unleash the value of data?
Over the decade since the mention of “personal data being the oil of the 21st century” at the DAVOS 2011 World Economic Forum, we have seen a wide range of diverse services using data and AI permeate throughout our lives. On the other hand, mass information breaches, unauthorized use of Web browsing history, and extreme personal information collection are becoming more common, as well as other various problems related to personal privacy. Faced with such circumstances, new regulations have been enforced to promote appropriate use of personal data, as exemplified by EU’s GDPR*1 and the CCPA*2 of the State of California.
In the near future, the advent of a data-driven society is expected to offer diverse advanced services through data linkage beyond corporate and industrial borders and simultaneously promote economic growth and social problem solving. Nevertheless, these possibilities can be destroyed if we cannot wipe away people’s distrust as well as enterprises’ burden of meeting complicated legal and regulatory requirements and anxieties about reputation risks.
- *1:GDPR: EU General Data Protection Regulation
- *2:CCPA: California Consumer Privacy Act

For the development of a data-driven society
To create a data-driven society, NEC considers it necessary to develop a reliable data platform on which anyone can feel secure in sharing and using personal data as new social infrastructure.
By equipping this data platform with both “a mechanism for secure and reliable data entrustment” and “a mechanism of privacy-conscious data linkage,” we should be able to expand the horizon of data use for many individuals, enterprises, and public agencies. We are hoping that collaborations across the boundaries of industries give rise to an explosive engendering of new services and business models.
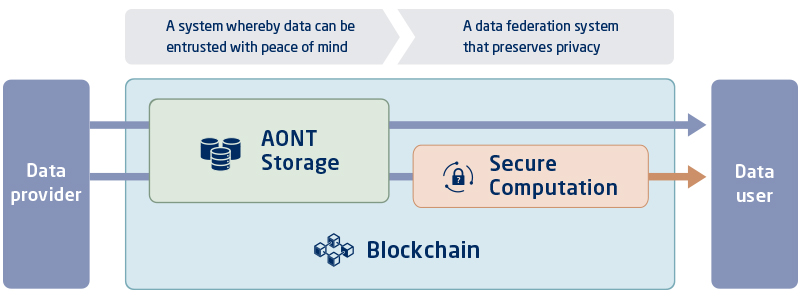
Mechanism for secure and reliable data entrustment
Personal data provided on the cloud is exposed to a variety of risks, including cyber attacks from outside and internal crimes by cloud administrators. NEC’s AONT (All-or-Nothing Transformation) storage technology (hereinafter “AONT Storage”) can significantly reduce information breach risks by means of data encryption and segmented storage in multiple cloud storages.
Data providers tend to feel anxious and hesitant to provide data the moment they sense the possibility that their personal data can be unintentionally mishandled. NEC’s blockchain technology can be used for strict access control based on user agreement and inter-corporate contract as well as for keeping records of the entire data life cycle from the generation of data to its use and erasure. This makes it possible for data providers to know by whom, when, and for what purpose their data was used, along with the integrity of the data, anytime.
AONT Storage
- Distributed storage of encrypted data on different cloud servers eliminates the risk of breach and loss
- Guarantee of recovery of data loss up to a certain volume

Blockchain
- Distributed management of data access, use history, and other information by multiple administrators
- Realize practical processing speed that supports large-scale environments as social infrastructure

Mechanism of privacy-conscious data linkage
Today, to pass on data, we can only directly hand over the data to the recipient. However, once the data is handed over, it becomes difficult to delete it afterwards or restrict its use beyond the intended purpose―which is why individuals and companies try not to externally release data whenever they do not have to.
NEC’s Secure Computation technology provides a new data linkage method that passes on only the calculation result without disclosing the data itself. This dispels the concerns for erasure after provision and unintended use, lowering the barrier to prior consent to data linkage.
- *Under the current Japan’s personal information protection law, consent must be obtained from the individual to whom the personal information belongs before providing the personal information to a third party.
Secure Computation (Secret sharing approach)
- Process data while keeping data confidential and output only analysis results.
- MPC (Multi-Party Computation) offers a high level of security by dividing input data into three segments using secret sharing

Aiming for a seamlessly connected society
In a society with progressive data utilization, the activities of individuals, enterprises, and public agencies are visualized in real-time and their seamless connection enables co-creation of new value. For example, enterprises can provide optimized services to individuals in collaboration with other industries while protecting their own corporate secrets and customer privacy. At the same time, enterprises can raise their corporate values by sharing that data with the national and local governments and showing that that data is contributing to the enrichment of social security and environmental improvement. Local governments can use corporate and personal data as evidence to quickly and repetitively going through the PDCA cycle, thereby continuously executing cost-efficient policies.

Use cases
Aiming to create a society that simultaneously pursues economic growth and social problem solving, NEC is working on the technology development for data platforms. We hope to get in touch with public organizations and business operators that are interested in working together with NEC on social implementation. Please inquire with us about any concerns and questions you may have regarding privacy with respect to data use and inter-corporate collaborations.

 Towards Trustworthy Cloud Storage
Towards Trustworthy Cloud Storage