Global Site
Breadcrumb navigation
Lightweight Program Tamper Detection
Product overview
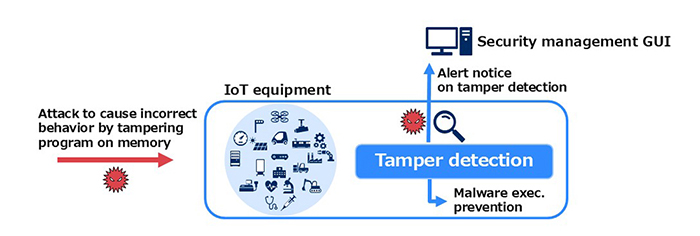
Lightweight Program Tamper Detection is a lightweight and fast software product to detect and prevent malwares and program tamper for IoT equipment with hardware resource constraints such as small memory capacity and low CPU performance.
Use cases and benefits
Securing IoT equipment and users
IoT users concern security risks caused by connecting IoT equipment to network. Incorrect equipment behaviors due to malwares and program tamper are risks to cause huge damage on various domains. For example, the incorrect equipment behavior shuts down factory operations in manufacturing domain, harms to life in medical domain, and shuts down social infrastructure in traffic domain. Introducing Lightweight Program Tamper Detection software to IoT equipment gives those users a sense of security by making them be aware of malwares and program tamper immediately.
Preparing for vulnerabilities
The attacks to exploit vulnerabilities are matters of concern, since many vulnerabilities of equipment software are discovered. Moreover, the attacks are often executed before software updating for removing vulnerabilities. If introducing Lightweight Program Tamper Detection software to equipment, such attacks can be detected immediately.
Feature and functionality
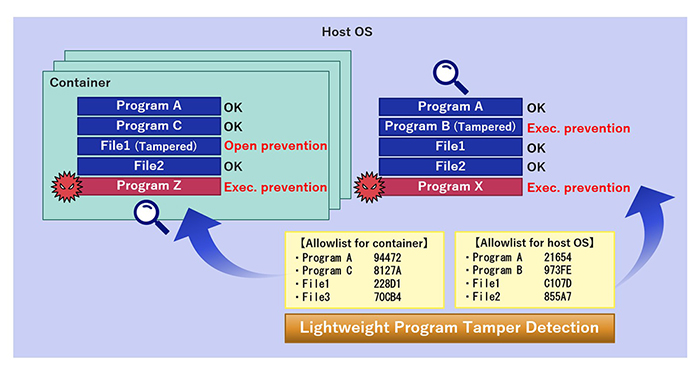
Lightweight Program Tamper Detection software is an allowlist-based product for IoT equipment. It maintains the equipment in normal condition by stopping execution of unallowed programs.
The Lightweight Program Tamper Detection software consists of the tamper detection module and the introduction support tool below.
Tamper detection module
Lightweight
The tamper detection module implemented on about 100Kbytes ROM is appropriate for equipment with small memory capacity.
Malware execution prevention
If the program files are registered in allowlist and not tampered, they are executed. Otherwise, their startup is blocked.
Process tamper detection
The tamper detection module periodically inspects the execution codes on memory to detect processes tamper. It is important to inspect processes, since the advanced attacks to tamper processes by exploiting vulnerabilities are increasing.
Load suppression
It is possible to make only small impacts on the functionality and performance of equipment by adjusting the inspection intervals and the inspection timings according to CPU load by processes inspection.
Container adaptability
The tamper detection module executed on host OS prevents malware execution and detects tampering the program files and processes in containers. There is no impact on development and deployment of the container images because it is unnecessary to deploy the tamper detection module in containers.
This functionality is available for Linux currently.
Introduction support tool
It does not take a lot of time and efforts to register many programs in allowlist, since the introduction support tool automatically generates allowlist from the system images of equipment.
Supported platforms
Tamper detection module
| Supported CPU | Arm Cortex-A series Intel x86/x64 compatible CPU |
| Supported OS | Linux QNX NEW |
Introduction support tool
| Supported CPU | Intel x86/x64 compatible CPU |
| Supported OS | Ubuntu 20.04 LTS |
| Necessary software | OpenSSL |
Please let us know if using other than the above platforms.
The specification of Lightweight Program Tamper Detection might be changed without notice.
 Larger view
Larger view