Global Site
Breadcrumb navigation
Working with CTEM
NEC Security BlogAug 29, 2025
This blog introduces “CTEM (Continuous Threat Exposure Management),” a concept that has been gaining attention in the cybersecurity field. CTEM is a framework for continuously assessing an organization's risk to cyberattacks by responding to them in order of priority.
Table of Contents
- 1. Introduction
- 2. Overview of CTEM (Continuous Threat Exposure Management)
- 3. Five-steps in CTEM
- 3-1. Scoping (Identifying the Scope of Attack)
- 3-2. Discovery (Detecting and Collecting Vulnerability Information)
- 3-3. Prioritization (Setting Priorities)
- 3-4. Validation (Verification)
- 3-5. Mobilization (Mobilizing and Executing Countermeasures)
- 4. Comparison of Traditional Vulnerability Management Processes and CTEM
- 5. Summary
Introduction
The expansion of teleworking, the increase in IT assets driven by digital transformation (DX), and the progress of cloud migration—these diversifying workstyles and accelerated digitalization within modern organizations are giving rise to a continuous stream of new cybersecurity risks. Furthermore, cyberattacks are becoming increasingly sophisticated  [1], with threats that cannot be fully prevented by conventional countermeasures such as large-scale ransomware attacks, supply chain attacks, unknown malware, and zero-day attacks on the rise. Under these circumstances, it is critical to thoroughly implement vulnerability management to ensure an organization's cybersecurity.
[1], with threats that cannot be fully prevented by conventional countermeasures such as large-scale ransomware attacks, supply chain attacks, unknown malware, and zero-day attacks on the rise. Under these circumstances, it is critical to thoroughly implement vulnerability management to ensure an organization's cybersecurity.
However, many organizations still face challenges such as difficulty in fully accounting for their IT assets and inadequate resources to address these issues  [2]. To improve this situation, it is essential to allocate appropriate resources and implement measures for continuous asset tracking. In this article, we introduce CTEM as one of the effective approaches.
[2]. To improve this situation, it is essential to allocate appropriate resources and implement measures for continuous asset tracking. In this article, we introduce CTEM as one of the effective approaches.
Overview of CTEM (Continuous Threat Exposure Management)
CTEM (Continuous Threat Exposure Management) is a framework proposed by Gartner in 2022  [3] for organizations to continuously assess and manage their risk of cyberattacks.
[3] for organizations to continuously assess and manage their risk of cyberattacks.
CTEM approach involves continuously and systematically evaluating and managing the accessibility, threat exposure, and exploitability of assets that could be targeted by cyberattacks.
With the recent increase and diversification of cyber threats, CTEM has gained significant attention in the cybersecurity field. According to Gartner's prediction  [3], by 2026, organizations appropriately setting their security priorities based on a CTEM could potentially realize a two-third reduction in breaches
[3], by 2026, organizations appropriately setting their security priorities based on a CTEM could potentially realize a two-third reduction in breaches  [4].
[4].
Currently, there are several cybersecurity companies beginning to offer CTEM-related products and solutions, and market growth is anticipated.
Five-steps in CTEM
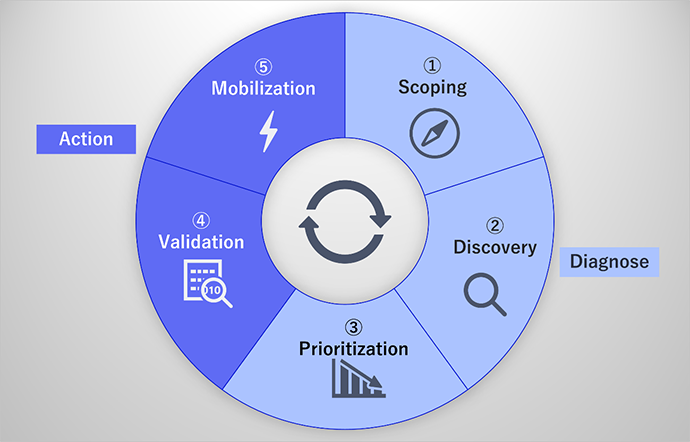
Gartner describes CTEM with the following five steps, which are cycled and performed continuously as shown in Figure 1.
Scoping (Identifying the Scope of Attack)
Discovery (Detecting and collecting vulnerability information)
Prioritization (Setting priorities)
Validation (Verification)
Mobilization (Mobilizing and executing countermeasures)
We will now explain these five steps.
1. Scoping (Identifying the Scope of Attack)
First, begin by identifying information assets both inside and outside the organization and defining what needs protection.
Gartner states that “The scoping required for CTEM extends beyond the focus of typical vulnerability management programs”  [3]. This means the scope must include not only devices and applications containing traditional vulnerabilities, but also corporate social media accounts, online code repositories, supply chain systems, and more.
[3]. This means the scope must include not only devices and applications containing traditional vulnerabilities, but also corporate social media accounts, online code repositories, supply chain systems, and more.
Begin by conducting an inventory of IT assets within the organization and performing surveys. Then, implement tools like IT asset management systems to identify assets that could be attacked.
2. Discovery (Detecting and Collecting Vulnerability Information)
After defining information assets and protection targets in the scoping process, it is then possible to detect specific vulnerability information within those defined scopes.
Gartner states that “Confusion between scoping and discovery is often the first failure when building a CTEM program.”  [3] The importance is not just the volume of discovered assets and vulnerabilities, but rather accurately defining the scope of attack based on business risk and potential impact before collecting vulnerabilities.
[3] The importance is not just the volume of discovered assets and vulnerabilities, but rather accurately defining the scope of attack based on business risk and potential impact before collecting vulnerabilities.
To be specific, the vulnerabilities are detected not only through vulnerability scanning tools, but also by gathering information through internal interviews of asset management methods and operations, as well as by utilizing threat intelligence.
3. Prioritization (Setting Priorities)
In the Discovery process, a large number of vulnerabilities are often detected. However, it is not realistically possible to address all vulnerabilities in all cases. In CTEM, it is important to prioritize addressing vulnerabilities that directly impact business continuity.
Gartner states that prioritization should factor in the following points  [3]:
[3]:
- Urgency
- Security
- Availability of compensating controls
- Tolerance for residual attack surface
- Level of risk posed to the organization
For example, rather than mechanically prioritizing vulnerabilities based simply on their threat level calculated from traditional CVSS scores  [5], it is necessary to evaluate and combine factors to determine which assets impact the business. A vulnerability affecting an asset with the second-highest CVSS score but directly impacting the business should be considered a higher priority than one affecting an asset with the highest CVSS score but not in use.
[5], it is necessary to evaluate and combine factors to determine which assets impact the business. A vulnerability affecting an asset with the second-highest CVSS score but directly impacting the business should be considered a higher priority than one affecting an asset with the highest CVSS score but not in use.
4. Validation (Verification)
First, verify whether the security measures in place are effective against the prioritized vulnerabilities. For information assets containing vulnerabilities with a high priority rating, analyze the attack pathways and verify if the protection is enough and/or if there is a potential threat to business continuity. The effectiveness of security measures is verified by simulating actual cyberattacks and attack pathways using specific techniques such as penetration testing and Branch and Attack Simulation (BAS)  [6]. Additionally, it is also helpful to get feedback from third parties, such as cybersecurity experts, to evaluate whether the countermeasures are appropriate.
[6]. Additionally, it is also helpful to get feedback from third parties, such as cybersecurity experts, to evaluate whether the countermeasures are appropriate.
5. Mobilization (Mobilizing and Executing Countermeasures)
Based on the validation results, implement the countermeasures considered necessary.
Gartner emphasizes that it is important to ensure teams understand and utilize the CTEM findings by reducing any obstacles to approvals, implementation processes, and mitigation deployments  [3]. This means that, in addition to deploying effective countermeasures for information assets such as patching, it is also necessary to conduct employee training for secure information asset management and operations, as well as continuous process improvement after implementing countermeasures, as required.
[3]. This means that, in addition to deploying effective countermeasures for information assets such as patching, it is also necessary to conduct employee training for secure information asset management and operations, as well as continuous process improvement after implementing countermeasures, as required.
Comparison of Traditional Vulnerability Management Processes and CTEM
| CTEM Steps | Traditional Vulnerability Management | CTEM |
| Attack surface identification | Mainly consists of devices and software included in products and services. | Includes not only devices and applications, but also corporate social media, repositories, supply chains, etc. |
| Vulnerability detection | Relies on specific data sources such as vulnerability scanning tools and vulnerability databases like NVD  [9]. [9]. |
Utilizes multiple data sources, including threat intelligence and information gathered from employees, not just vulnerability scanning tools. |
| Prioritization | List vulnerabilities by severity using metrics such as CVSS scores. | Besides vulnerability severity, identify high-risk pathways to critical assets and prioritize them. |
| Verification | Simulate actual cyberattacks and breach pathways to verify the effectiveness of security measures. | Based on priority, simulate actual cyberattacks and breach pathways to verify the effectiveness of security measures. |
| Execution of countermeasures | Implement direct countermeasures for information assets, such as patching. | In addition to countermeasures for information assets, educate employees and improve processes for new countermeasures. |
The table 1 above shows that implementing CTEM enables more comprehensive and effective vulnerability countermeasures compared to traditional vulnerability management processes.
Personally, I am involved in software and service development for internal security measures, performing vulnerability assessments and countermeasures for the software and services we provide.
We believe that applying CTEM methodologies can help reduce business risk while also reducing the effort required to address low-priority assets that do not store critical information or servers where attacks cannot be successfully executed.
On the other hand, it requires greater preparation both technically and organizationally compared to traditional vulnerability management processes. Most CTEM-related services currently available on the market cannot cover all five steps with a single security product and are provided by combining multiple products. The challenges are to ensure the necessary costs for the initial preparation and to enhance the knowledge of security measures and vulnerabilities for the implementers.
Summary
In this article, we have described “CTEM (Continuous Threat Exposure Management),” which has been a focus in the cybersecurity field.
In traditional vulnerability management processes, continuous threat identification and prioritization have been challenges. CTEM is a method that enables rapid response to an ever-changing attack environment by continuously monitoring and managing an organization's cybersecurity and through dynamic prioritization based on both the severity of vulnerabilities and their business impact. We will continue to keep our eyes on the market expansion of CTEM-related solutions and their actual success stories.
References
- [1]情報セキュリティ10大脅威 2025
 https://www.ipa.go.jp/security/10threats/10threats2025.html
https://www.ipa.go.jp/security/10threats/10threats2025.html - [2]2024年度 中小企業における情報セキュリティ対策に関する実態調査- 報告書 -
 https://www.ipa.go.jp/security/reports/sme/nl10bi000000fbvc-att/sme-chousa-report2024r1.pdf
https://www.ipa.go.jp/security/reports/sme/nl10bi000000fbvc-att/sme-chousa-report2024r1.pdf - [3]How to Manage Cybersecurity Threats, Not Episodes
 https://www.gartner.com/en/articles/how-to-manage-cybersecurity-threats-not-episodes
https://www.gartner.com/en/articles/how-to-manage-cybersecurity-threats-not-episodes - [4]Gartner、2024年の戦略的テクノロジのトップ・トレンドを発表
 https://www.gartner.co.jp/ja/newsroom/press-releases/pr-20231114-techtrends
https://www.gartner.co.jp/ja/newsroom/press-releases/pr-20231114-techtrends - [5]共通脆弱性評価システムCVSS概説
 https://www.ipa.go.jp/security/vuln/scap/cvss.html
https://www.ipa.go.jp/security/vuln/scap/cvss.html - [6]BAS(Breach and Attack Simulation)
 https://www.macnica.co.jp/business/security/glossaries/bas/
https://www.macnica.co.jp/business/security/glossaries/bas/ - [7]NIST SP800-40 パッチおよび脆弱性管理プログラムの策定
 https://www.ipa.go.jp/security/reports/oversea/nist/ug65p90000019cp4-att/begoj9000000bb4h.pdf
https://www.ipa.go.jp/security/reports/oversea/nist/ug65p90000019cp4-att/begoj9000000bb4h.pdf - [8]簡単!Excelからはじめる脆弱性管理 ~トリアージ~
https://jpn.nec.com/cybersecurity/blog/241108/index.html - [9]National Vulnerability Database
 https://nvd.nist.gov/
https://nvd.nist.gov/
Profile

Koudai Suzuki
Responsibility Area: Secure Technology Development
Specialization: Secure Development, Agile/Scrum
Engaged in developing security-related services for internal use within the NEC Group.