Global Site
Breadcrumb navigation
Understanding Fargo Ransomware
NEC Security BlogMar 22, 2024
Dr. Sareena K P, Dr. Manikantan Srinivasan
NEC Corporation India Pvt. Ltd.
Late 2022 observed an emergence of a new wave of ransomware attacks named as Fargo targeting vulnerable Microsoft Structured Query Language (SQL) servers  [1]. Widely used across companies, Microsoft SQL servers are database management systems for storage and retrieval of data related to most Internet services and applications
[1]. Widely used across companies, Microsoft SQL servers are database management systems for storage and retrieval of data related to most Internet services and applications  [2]. These servers pose as a lucrative target for making quick profit as disrupting their functioning can have severe repercussions. Research indicates that Fargo and its variants have been in the horizon since 2021. This ransomware is attributed to the TargetCompany group, which is known to vary the encryption strategies and the file extensions in each major release of its ransomware based on the attack target
[2]. These servers pose as a lucrative target for making quick profit as disrupting their functioning can have severe repercussions. Research indicates that Fargo and its variants have been in the horizon since 2021. This ransomware is attributed to the TargetCompany group, which is known to vary the encryption strategies and the file extensions in each major release of its ransomware based on the attack target  [3].
[3].
This malware seems to be quite active indicated by the considerable number of Fargo ransomware attacks reported on the ID ransomware platform [4]. While prior reports
[4]. While prior reports  [1]
[1]  [3]
[3]  [5]
[5]  [6] present the analysis and indicators of Fargo and its variants, we attempt to decode its encryption strategy, geo-sensitive policies, propagation strategies by comparing three variants namely, Fargo
[6] present the analysis and indicators of Fargo and its variants, we attempt to decode its encryption strategy, geo-sensitive policies, propagation strategies by comparing three variants namely, Fargo  [1], Mallox
[1], Mallox  [6] and Fargo.YACH2
[6] and Fargo.YACH2  [3]. We also map the behaviour of Fargo to MITRE Tactics and Techniques. Finally, we analyse the possibility of recovery of files encrypted by Fargo.
[3]. We also map the behaviour of Fargo to MITRE Tactics and Techniques. Finally, we analyse the possibility of recovery of files encrypted by Fargo.
Key findings. Below are the key findings from our study.
-
Fargo family adopts the intermittent encryption strategy to accelerate encryption and to evade detection. (Encryption for impact)
-
Fargo reveals its functionality only in systems having non-Russian languages.
-
Fargo attempts to propagate to local network
-
Mapping of Fargo’s behaviour with MITRE ATT&CK techniques
-
Recovery of large files encrypted by the malware could be feasible using open-source tools.
Samples. This blog is based on the analysis of three samples:
| Name | Popular threat label | SHA-256 |
|---|---|---|
| Fargo | ransomware.garrantdecrypt/targetcomp | 2a549489e2455a2d84295604e29c727dd20d65f5a874209840ce187c35d9a439 |
| Mallox | ransomware.mallox/garrantdecrypt | ebdcf54719cceddffc3c254b0bfb1a2b2c8a136fa207293dbba8110f066d9c51 |
| TargetCompany (Fargo.YACH2) | trojan.msil/tedy | 4f4ee2de8f18bf758d72ac288e61071e1be2ddc54a140cd512c97f5473461036 |
Intermittent Encryption
For any ransomware, accelerating the encryption process is the key to increase the impact while making detection harder. Encryption process is both compute-intensive and I/O intensive. Consequently, detection mechanisms often rely on the intensity of the CPU and I/O operations as statistical indicators to detect ransomware. An encryption strategy that is both quick and light-weight, not only minimizes the time window for the defenders to respond, but also makes detection of ransomware challenging  [7].
[7].
The latest technology aiding cyber-criminals in this regard is intermittent encryption. Instead of encrypting the entire file contents, intermittent encryption enables the ransomware to encrypt only parts of the files, and yet make the files unrecoverable without the decryption key. The trend first observed with LockFile ransomware in mid 2021  [8] have since gained wider adoption among the ransomware adversaries.
[8] have since gained wider adoption among the ransomware adversaries.
Fargo adopts the technique of intermittent encryption to speed up the encryption of all target files in the filesystem. However, it customizes its strategy based on the size of the files as a measure to balance the overheads versus benefits of the intermittent encryption. A pattern of interleaved encrypted and unencrypted regions is observed in Fargo, Mallox and TargetCompany encrypted binaries as illustrated in Figure 1. However, the size of the encrypted and unencrypted portions varies across the three variants as well as based on the size of the file being encrypted.
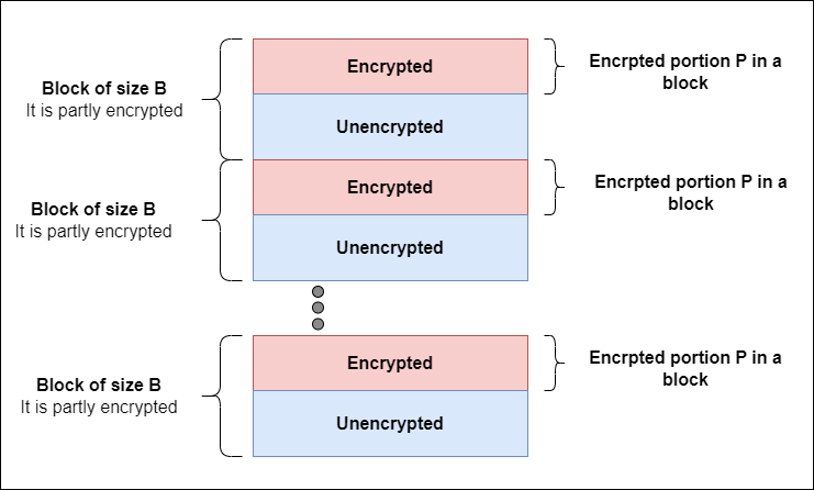
Figure 2 depicts the encryption algorithm adopted in Fargo. Files smaller than 10 Kilo Bytes are not encrypted. On the other hand, files of size greater than 10 Kilo Bytes and less than 50 Kilo Bytes are encrypted entirely. For file greater than 50 Kilo Bytes, Fargo divides the file into blocks. The size of the block (B in Figure 1) as well as the percentage of bytes encrypted within a block (P in Figure 1) varies with the file size. Files less than 260 Kilo Bytes are divided into blocks of equal size in the range of 4096-8192 Bytes, and within each block the first 4096 Bytes are encrypted. Consequently, within each block, few bytes are left unencrypted. We observe that for files < 260 KB, at most 255 bytes are left unencrypted. On the other hand, files > 260 KB are divided into 10 blocks of equal size. In each block, the first 15% of the bytes are encrypted.
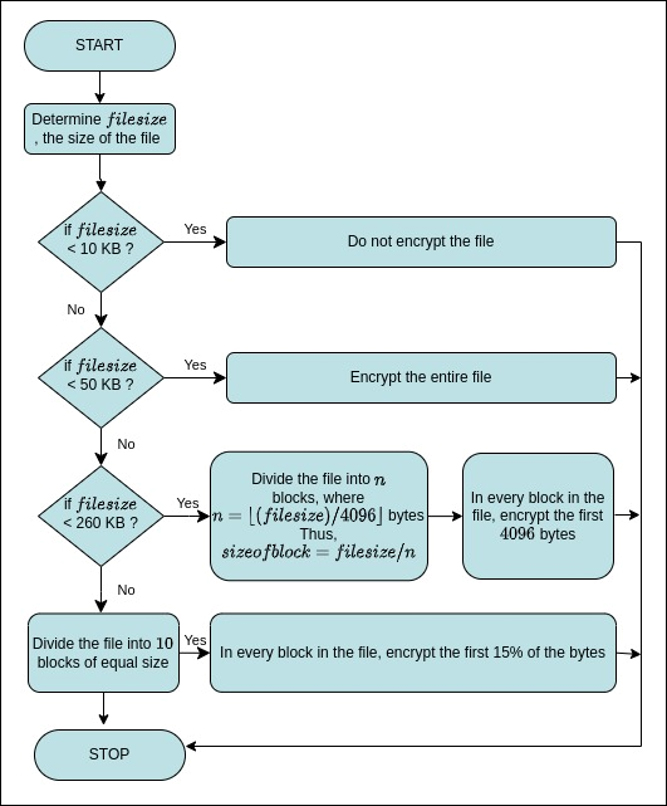
Difference across variants. Similar encryption strategy is observed in the Fargo.YACH2 variant of Fargo. However, another variant, namely Mallox uses a different configuration for intermittent encryption. In our analyses, we observe that Mallox divides larger files greater than 3 Mega Bytes into 100 blocks of equal size. Within each block, 30 to 40% of the bytes are encrypted. In contrast, smaller files less than 128 Kilo Bytes completely encrypted. Intermediate files were observed to be divided into 25 blocks of equal size, while encrypting more than 90% of contents in each block.
Strategy of maximum impact. As only parts of the files are encrypted, Fargo can encrypt large number of files in a shorter span of time. Thus, Fargo is able to maximize impact in a shorter time before getting detected by detection and mitigation tools. At the same time, the reduced scale of encryptions minimizes the intensity of I/O operations, and can help Fargo to be classified as light-weight process. This could be used to maintain stealth.
With portions of the files left unencrypted, research have demonstrated the feasibility of recovering files encrypted by intermittent encryption. We explore the possibility of recovery of Fargo-encrypted files in Section 5.
Geo-location sensitivity
Incorporating geo-location specific control paths in malware is a well-known technique adopted by threat actors for targeted attacks. While the modus-operandi of Fargo and its related variants have been discussed in prior works  [1]
[1]  [6]
[6]  [3]
[3]  [5], we observe geo-location specific control paths in the Fargo and Mallox variants as illustrated in Figure 3.
[5], we observe geo-location specific control paths in the Fargo and Mallox variants as illustrated in Figure 3.
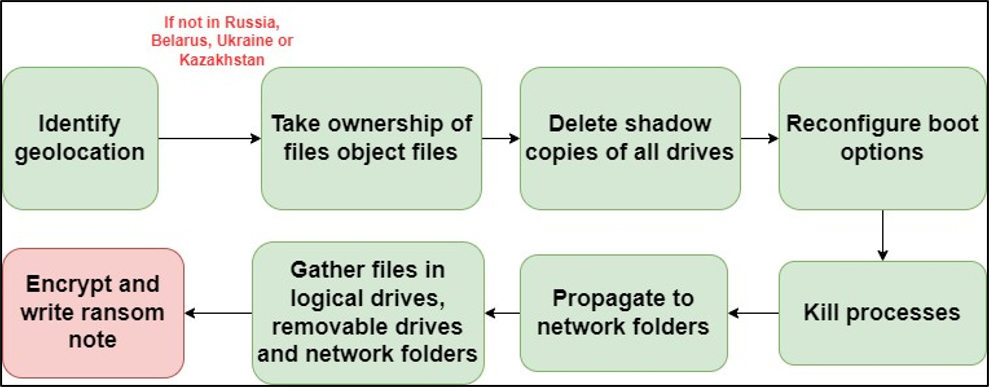
Fargo and Mallox ransomware check for specific language identifiers in the region format settings of the target machine to identify its geo-location. If the language pack indicates languages of Russia, Ukraine, Belarus or Kazakhstan, the malware quits immediately. Table 1 lists the language packs the malware checks for along with the associated country [11]. The ransomware functionality is invoked only if the geo-location of the target machine is not among the countries listed in Table 1 (Refer to Figure 4).
[11]. The ransomware functionality is invoked only if the geo-location of the target machine is not among the countries listed in Table 1 (Refer to Figure 4).
| Language Identifier | Language Identifier (decimal) | Language (Country) |
|---|---|---|
| 0x0419 | 1049 | Russian (Russia) |
| 0x043F | 1087 | Kazakh (Kazakhstan) |
| 0x0423 | 1059 | Belarusian |
| 0x0422 | 1058 | Ukrainian(Ukraine) |
| 0x0444 | 1092 | Tatar (Russia) |
Table 1 Language ID and the associated countries  [7]
[7]
Attribution. This geo-location sensitivity (verified with language pack) suggests that the threat actors behind Fargo ransomware are likely based in Russia. Russian authorities are known to control cyber-attacks within their borders, but are tolerant towards attacks targeting outside Russia  [9]. For instance, Russian authorities typically refrain from launching a cybercrime investigation against a fellow citizen unless a company or individual within the nation files an official complaint as a victim. Preventing any local affiliates from generating victims in their own jurisdictions is the simplest method for these threat actors to evade detection by domestic law enforcement agencies.
[9]. For instance, Russian authorities typically refrain from launching a cybercrime investigation against a fellow citizen unless a company or individual within the nation files an official complaint as a victim. Preventing any local affiliates from generating victims in their own jurisdictions is the simplest method for these threat actors to evade detection by domestic law enforcement agencies.
Local Propagation
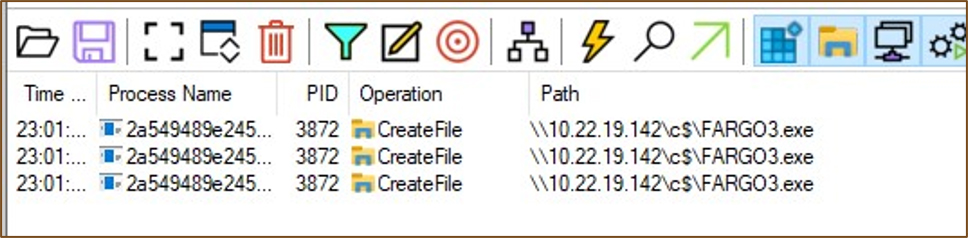
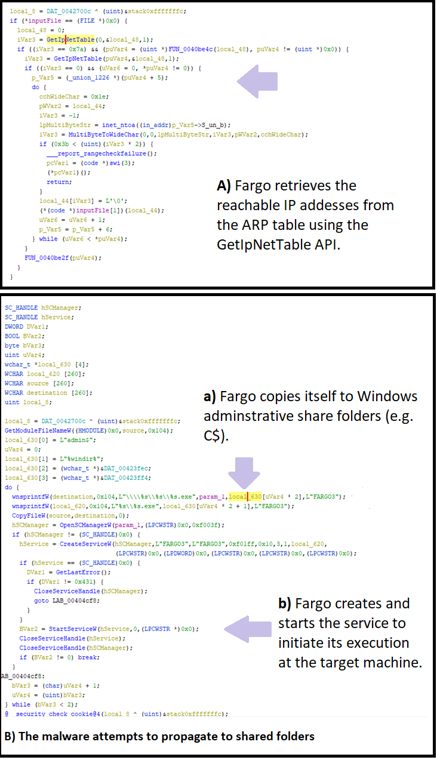
Fargo and Mallox also attempt to propagate to systems in the local subnet. Before the malware gathers the files for encryption, it enumerates the reachable IP addresses in the subnet (Refer to Figure 6A), using the GetIpNetTable API. The API retrieves the IPv4 addresses in the ARP table. Following this, the malware copies itself to the Windows administrative share (e.g. C$ ) folders as seen in Figure 6B. Further, it creates a service to initiate its execution. Figure 5 illustrates the operating system logs indicating the copy.
MITRE ATT&CK Techniques
Following are the different MITRE ATT&CK techniques observed for the Fargo ransomware during our analysis (Figure 7).
| Execution | Credential Access | Persistence | Privilege Escalation | Defense Evasion | Lateral Movement | Discovery | Impact |
|---|---|---|---|---|---|---|---|
| System Services (T1569) | Registry Run Keys/Start-up (T1547.001) | Access token manipulation (T1134) | Sandbox evasion (T1497) | Lateral Tool Transfer (T1570) | Query Registry (T1012) | Data Encrypted for Impact (T1486) | |
| Command and Scripting Interpreter (T1059) | Create or Modify System Processes (T1543) | Impair defences (T1562) | File and Directory Discovery (T1083) | Service Stop (T1489) | |||
| Native API (T1106) | Direct Volume Access (T1006) | System Information Discovery (T1082) | Inhibit System Recovery (T1490) | ||||
| Process Injection (T1055) | System Process Discovery (T1057) | ||||||
| System Time Discovery (T1124) |
Figure 7 MITRE ATT&CK techniques of Fargo ransomware
Execution.
- T1059: Command and Scripting Interpreter Windows Command Shell
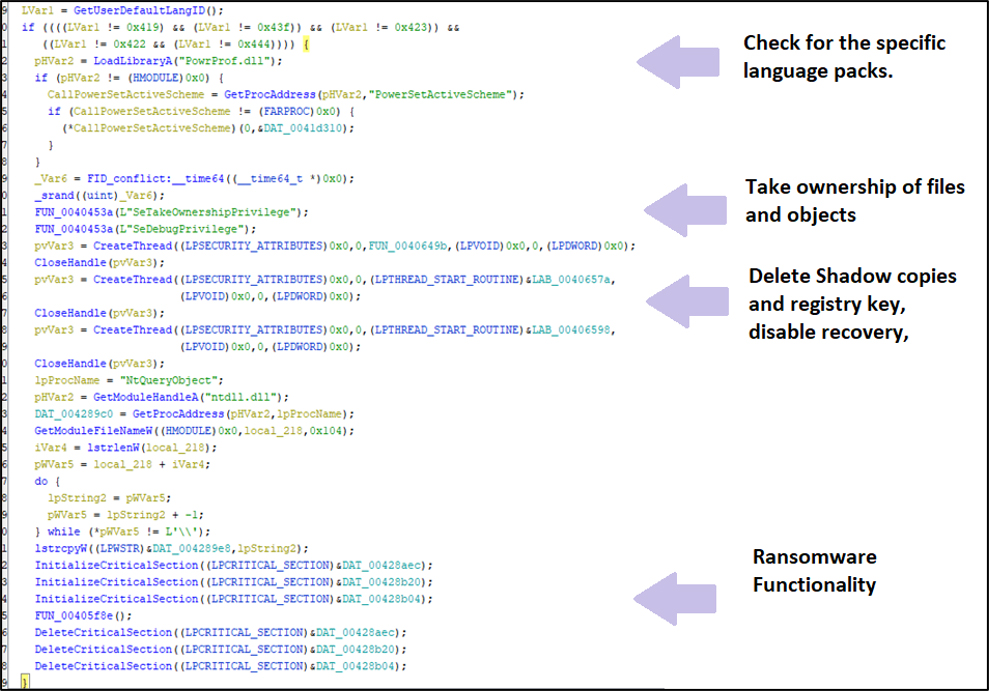
Fargo ransomware abuses the command and scripting interpreter or the command shell to execute malicious payloads and commands. For instance, "C:\Windows\System32\cmd.exe" /c bcdedit /set {current} bootstatuspolicy ignoreallfailures - T1106: Native API
Fargo ransomware invokes ShellExecute and ShellExecuteA to delete services and terminate processes. - T1055 Process Injection
The .NET downloader injects Fargo ransomware into AppLaunch.exe [1].
[1]. - T1569: System Services Execution
After copying itself to the network folders, Fargo ransomware creates a service to initiate the execution of the malware process.
Evasion.
- T1562: Impair Defenses
The infection chain of Fargo ransomware begins with a .NET executable downloaded at the target. This process generates the Kill AV Batch script and downloads the Fargo ransomware. The Kill AV Batch script (41bcad545aaf08d4617c7241fe36267c) payload disables or kills security software such as Microsoft defender, Active Health System Services, Sense Shield Service, SSMonitorService, Microsoft Office Software Protection Platform
Privilege Escalation.
- T1134: Access Token Manipulation
Fargo ransomware invokes SeTakeOwnershipPrivilege and SeDebugPrivilege to elevate privileges as observed in the reverse engineering of the ransomware code.
Persistence.
- T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
Fargo ransomware employs Registry Run Keys/Startup Folder to configure system settings to execute the program during system boot or logon. - T1543: Create or Modify System Processes
Fargo ransomware copies itself to the shared network folders and creates a service to initiate its execution
Discovery.
- T1012: Query Registry
Fargo reads Internet settings and machine GUID. - T1082: System Information Discovery
Fargo reads the computer name, invokes IsdebuggerPresent(). - T1124: System Time Discovery
Fargo invokes GetTickCount, GetSystemTimeAsFileTime, GetSystemTimePreciseAsFileTime - T1083: File and Directory Discovery
Fargo invokes GetWindowsDirectory, FindFirstFileEx, FindNextFile - T1057: System Process Discovery
Fargo invokes GetCurrentProcessId, getCurrentProcess, getCurrentThreadID, CreateToolhelp32Snapshot, Process32Next.
Lateral Movement.
- T1570: Lateral Tool Transfer
Fargo ransomware copies itself to the shared network folders and creates a service to initiate its execution
Impact.
- T1486: Data Encrypted for Impact
Fargo encrypts and renames files like ransomware. Further, it creates ransomware like instructions - T1489: Service Stop
Fargo disables multiple services including the MS-SQL server - T1490: Inhibit System Recovery
Fargo uses BCDEDIT.EXE to modify recovery options (C:\Windows\System32\cmd.exe /c bcdedit /set {current} recoveryenabled no)
Possibility of Recovery
As significant portions of files are left unencrypted in intermittent encryption, research shows that data could be recovered from the unencrypted portions of the file for select file formats  [10]. White-Phoenix is an open-source ransomware decryptor that supports recovery of files encrypted using the strategy of intermittent encryption. The tool is shown to decrypt files encrypted by malware such as BlackCat/ALPHV, Play, Qilin/Agenda and BianLian ransomware
[10]. White-Phoenix is an open-source ransomware decryptor that supports recovery of files encrypted using the strategy of intermittent encryption. The tool is shown to decrypt files encrypted by malware such as BlackCat/ALPHV, Play, Qilin/Agenda and BianLian ransomware  [10].
[10].
We observe that the encryption strategy adopted in Fargo is similar to the one of the modes followed in BlackCat  [7]. Unlike BlackCat, Fargo splits the entire file into equally sized blocks, whereas BlackCat encrypts a fixed size of bytes in the beginning of the file before splitting the rest of the file into blocks. With the encryption strategy being largely similar to BlackCat, the decryption of the files encrypted by Fargo seems possible with White-Phoenix. To assess if such recovery is feasible, we evaluate White-Phoenix with three different files which was encrypted by Fargo (i) a PDF document with 5 images, (ii) the same document in word (.docx) format) and (iii) a zip file.
[7]. Unlike BlackCat, Fargo splits the entire file into equally sized blocks, whereas BlackCat encrypts a fixed size of bytes in the beginning of the file before splitting the rest of the file into blocks. With the encryption strategy being largely similar to BlackCat, the decryption of the files encrypted by Fargo seems possible with White-Phoenix. To assess if such recovery is feasible, we evaluate White-Phoenix with three different files which was encrypted by Fargo (i) a PDF document with 5 images, (ii) the same document in word (.docx) format) and (iii) a zip file.
Table 2 summarizes the results of our experiment. With respect to the PDF file, we observe that two out of 5 images could be decrypted as seen in Figure 8. While one image could be completely recovered, the other was only partially recovered. On the other hand, White-Phoenix failed to decrypt the word document.
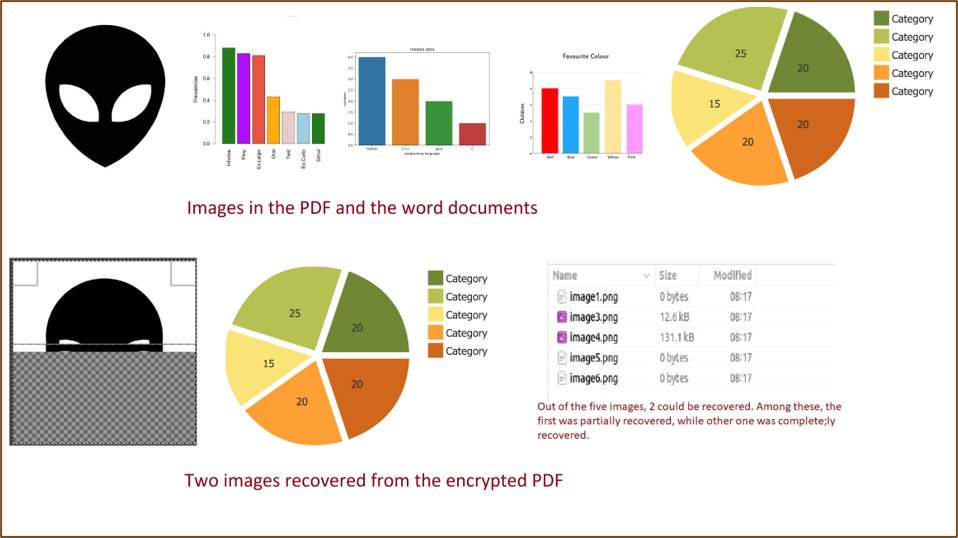
Further, the zip file (Test.zip of 57.9MB size) had a total of 751 files. Out of these, 724 files could be completely recovered from the Fargo encrypted Test.zip.FARGO3 file. These files were recovered from the unencrypted potions of Test.zip.FARGO3 file, and varied in size from 4KB to 3.2 MB. Recovery of files of 3.2 MB size is feasible because Fargo divides the file into 10 blocks, each of size ≈ 5.7 MB, and in each block only 15% of the bytes are encrypted. On the other hand, 20 files could not be recovered at all and these files ranged in sizes from 1.7 KB to 3.4 MB. Note that the recovery of files from Test.zip.FARGO3 also depends on the location of the compressed file inside the zip file. Finally, 7 files were partially recovered. The percentage of bytes recovered in summarized in the Table.
As observed, the recovery efficacy varied on the type of file and its contents. Images could be recovered from a pdf document, and not from the word document. For images and text-based files, partial recovery may be helpful in interpreting the data. It is to be noted that the experiment was conducted using the White-Phoenix code without any Fargo-specific configuration. The recovery could be enhanced by configuring White-Phoenix to the encryption algorithm adopted by Fargo. Nevertheless, partial recovery of files that are binary in nature such as virtual machine images may not be interpretable and usable.
| Sl.No | Original File | Size | Recoverable |
|---|---|---|---|
| 1 | Test.pdf (PDF file with 5 images) | 403 KB | Partially. Two images recovered |
| 2 | Test.docx (Word document with 5 images) | 517 KB | Not recoverable |
| 3 | Zip file (total 751 files) | 57.9 MB | 724 files recovered completely 20 files not recovered, ranging from file size 1.7K - 3.4M 7 files partially recovered |
| Partially recovered files | |||
| File 1 (binary) | 1.7 MB | Partially recovered 64KB (3.6%) | |
| File 2 (binary) | 1.3MB | Partially recovered 192K (14.4%) | |
| File 3 (binary) | 16MB | Partially recovered 128KB (0.78%) | |
| File 4 (text) | 3.4MB | Partially recovered 1.3MB (38%) | |
| File 5 (binary) | 651K | Partially recovered 576K (88%) | |
| File 6 (binary) | 1.3MB | Partially recovered 896K (67%) | |
| File 7 (binary) | 30MB | Partially recovered 3.5MB (11%) | |
Table 2. Summary of the files that could be recovered from the Fargo encrypted files.
Conclusion
Fargo ransomware seems to be quite active given the spate of attacks reported last year  [1]
[1]  [3]
[3]  [5]
[5]  [6]. It has been known by various names such as Mallox and TargetCompany based on the extension it gives to the files after encrypting. In this report, we delved into the strategies adopted by Fargo and its variants in terms of encryption, geo-location sensitivity and propagation. Fargo and its variants adopt the intermittent encryption strategy to accelerate encryption, to maximize impact and evade detection. However, such as strategy makes it feasible for recovery of the files encrypted by the malware using open-source tools. One such tool was explored in this report. Finally, the report presents the detailed MITRE ATT&CK analysis of the behaviour of Fargo ransomware.
[6]. It has been known by various names such as Mallox and TargetCompany based on the extension it gives to the files after encrypting. In this report, we delved into the strategies adopted by Fargo and its variants in terms of encryption, geo-location sensitivity and propagation. Fargo and its variants adopt the intermittent encryption strategy to accelerate encryption, to maximize impact and evade detection. However, such as strategy makes it feasible for recovery of the files encrypted by the malware using open-source tools. One such tool was explored in this report. Finally, the report presents the detailed MITRE ATT&CK analysis of the behaviour of Fargo ransomware.
References
- [1]ASEC, “FARGO Ransomware (Mallox) Targeting Vulnerable MS-SQL Servers,” ASEC,
 https://asec.ahnlab.com/en/39152/, 2022.
https://asec.ahnlab.com/en/39152/, 2022. - [2]Enlyft, “Companies using MySQL,”
 https://enlyft.com/tech/products/microsoft-sql-server.
https://enlyft.com/tech/products/microsoft-sql-server. - [3]TargetCompany, “Ransomware Spotlight: TargetCompany,”
 https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-targetcompany, 2023.
https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-targetcompany, 2023. - [4]“ID Ransomware,” [Online]. Available:
 https://id-ransomware.malwarehunterteam.com/.
https://id-ransomware.malwarehunterteam.com/. - [5]TargetCompany, “TargetCompany Ransomware,”
 https://id-ransomware.blogspot.com/2021/06/tohnichi-ransomware.html, 2021.
https://id-ransomware.blogspot.com/2021/06/tohnichi-ransomware.html, 2021. - [6]S. C. Lior Rochberger, “Threat Group Assessment: Mallox Ransomware,” Unit42,
 https://unit42.paloaltonetworks.com/mallox-ransomware/, 2023.
https://unit42.paloaltonetworks.com/mallox-ransomware/, 2023. - [7]A. Novick, “White Phoenix: Beating Intermittent Encryption,” CyberArk, no.
 https://www.cyberark.com/resources/threat-research-blog/white-phoenix-beating-intermittent-encryption, 2023.
https://www.cyberark.com/resources/threat-research-blog/white-phoenix-beating-intermittent-encryption, 2023. - [8]Labs, Sentinel, “Ransomware Developers Turn to Intermittent Encryption to Evade Detection,” no.
 https://www.sentinelone.com/labs/crimeware-trends-ransomware-developers-turn-to-intermittent-encryption-to-evade-detection/, 2022.
https://www.sentinelone.com/labs/crimeware-trends-ransomware-developers-turn-to-intermittent-encryption-to-evade-detection/, 2022. - [9]B. Krebs, “Try This One Weird Trick Russian Hackers Hate,” KrebsOnSecurity,
 https://krebsonsecurity.com/2021/05/try-this-one-weird-trick-russian-hackers-hate/, 2021.
https://krebsonsecurity.com/2021/05/try-this-one-weird-trick-russian-hackers-hate/, 2021. - [10]CyberArk, “White Phoenix,' an open-source ransomware decryptor,”
 https://github.com/cyberark/White-Phoenix.
https://github.com/cyberark/White-Phoenix. - [11]Microsoft, “Available languages for Windows,”
 https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/available-language-packs-for-windows?view=windows-11.
https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/available-language-packs-for-windows?view=windows-11.
Profile

Wataru Takahashi, CISSP Associate
Security Engineering Center, Cyber Security Intelligence Group
Wataru Takahashi is a member of Cyber Security Intelligence Group. He dedicates himself to collection, analysis, and provision for threat intelligence.
Profile
Dr.Manikantan Srinivasan, CISSP
NEC Open networks Solution and Services (NOSS) Delivery Unit, NEC Corporation India Pvt Ltd.
Dr Manikantan is involved in AI/ML aided 5G and beyond related research, O-RAN alliance architecture based secure 5G solution development, Telecom Security, 3GPP standardization initiatives and Cyber Threat Intelligence related research. He is a NEC Delegate to O-RAN WG11 - Security Working Group and contributes to O-RAN Security standardization. Dr. Manikantan has 24+ years of Industry experience in domain of Communication Networks, Mobile Cellular Networks and Security.
Dr. Manikantan has made several contributions to MITRE ATT&CK since 2021.

Profile
Dr. Sareena Karapoola
Digital Platform Delivery Unit (DPDU), NEC Corporation India Pvt Ltd.
Dr. Sareena is involved in malware analysis, detection engineering, and cyber threat intelligence-related research. Dr. Sareena earned her direct Ph.D. in Computer Science from the Indian Institute of Technology Madras in 2022 in cyber security. Her other research interests include novel AI-based detection and mitigation strategies, real-world testbeds, and labeled datasets for security research. Dr. Sareena has 10+ years of industry experience in embedded products and system software, including smart card readers and access control terminals.
