Global Site
Breadcrumb navigation
NEC’s Secure Development Initiatives
NEC Security BlogFeb 22, 2024
The topic of this blog is about NEC’s secure development initiatives.
NEC has been engaged in secure development for more than 20 years since the early 2000s.
The trigger for our full-fledged efforts was the increase in cyber-attacks targeting websites, such as SQL injections, and the growing concern that customers were suffering from data breaches and other problems. Around that point, we began company-wide efforts in secure development, such as conducting vulnerability assessments on systems before shipping and implementing countermeasures against any vulnerabilities detected.
To further enhance our organizational response, a specialized department called the Cyber Security Strategy Division (currently changed to the Cyber Security Strategy Department) was established in the 2010s and started full-fledged efforts in secure development.
This article introduces our process of improvement for such secure development initiatives and recent topics related to it.
Table of Contents
Revision of Security Baseline
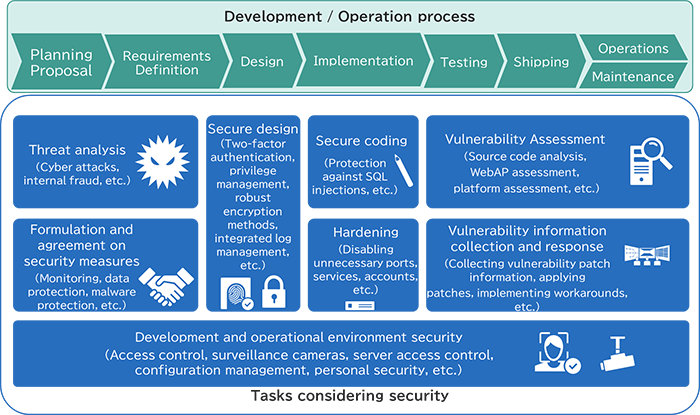
In our secure development initiatives, we utilize the checklist to verify the implementation of security measures in each phase, from the planning and design to the operation of products, systems, and services (hereinafter referred to as "products"). Initially, when we started our secure development efforts, this checklist focused only on the confidentiality of the information assets handled by the target products. By utilizing this checklist, we defined the security levels of confidentiality and it narrowed down the measures to be implemented.
However, this method posed a risk of vulnerable security measures in systems where continuous operation (= high availability) was required and only publicly available information was handled (= low confidentiality of information assets). Furthermore, in the latter half of the 2010s, the methods and targets of cyberattacks such as ransomware and denial-of-service became more diverse. As a result, there was a growing need to consider integrity and availability in addition to confidentiality.
Then, we reviewed the previous baseline, added definitions of integrity and availability besides confidentiality, and revised the checklist to respond to a wider variety of risks by extracting the necessary security measures from those three elements.
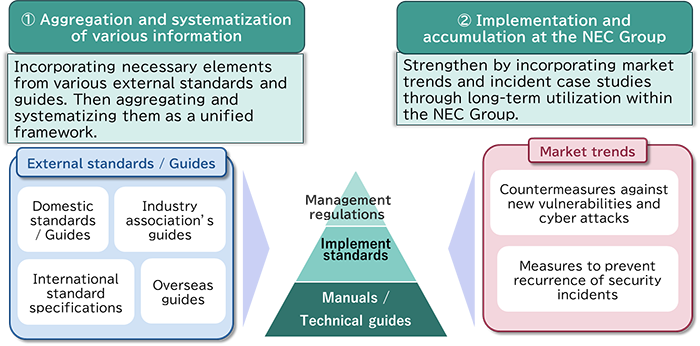
Reinforcement of Secure Development Systems and Processes
As part of our efforts to enhance secure development practices, we have formulated a set of guidelines called the Rules for Secure Development and Operations Management to reduce incidents caused by various system misconfigurations and failures. Also, we have established a framework to promote secure development and operations management and proceeded with company-wide deployment.
Considering the recent increase in cyberattacks that have become more sophisticated, the content of this regulation has been extensively revised and the name has also been changed to the Cybersecurity Management Rules.
In this revision, mainly we have changed two points. The first one is to increase the percentage for departments with the Cybersecurity Managers. Previously, in the business departments that provide products to customers, a person in charge of security was assigned to take responsibility for promoting secure development. We have now expanded the increased the number of the departments with Cybersecurity Managers and made it a general practice to have Cybersecurity Managers assigned to all the departments. As a result, we have been able to promote and be aware of secure development not only in the department that provides products but also others that interact with customers in various ways.
For second, we have revised the development process. Specifically, in the past, each person in charge of development has made judgements on which products should be subject to secure development. However, with this approach, there was a risk of subjective judgements and the products that should have been subject to secure development would be judged as out of the scope of the regulations. Therefore, under the new regulations, we have introduced a definition that all products provided to customers are subject to secure development. In the development of all products, the process has been changed to determine the security levels and narrow down the necessary security implementations.
Summary
In this article, we introduced some of the topics related to secure development that we have been working on in recent years. Currently, this initiative has been spreading to all group companies, and equivalent regulations, systems, and processes are being implemented within each company. By continuing these initiatives, we aim to standardize the security quality of the products of NEC Group at a high level.
Profile
Masashi Kobayashi, CISSP, RISS(Registered Information Security Specialist)
Security Engineering Center, Security Implementation Technology Architecture Group
After working as an infrastructure engineer and consulting on security, Masashi Kobayashi currently leads the promotion of secure development and operation at NEC Group, overseeing the creation of policies, structure, and processes. He also serves as a risk assessment and security training instructor. His qualifications include CISSP and RISS(Registered Information Security Specialist).
