Global Site
Breadcrumb navigation
Password Requirements Examined from Guidelines and Survey
NEC Security BlogSep 18, 2020
The theme of this blog is passwords. There are various discussions and guides on what kind of password requirements should be set for organizations and systems and what kind of password users should set. The goal of this blog is not to give readers an answer to password requirements but to give them a chance to think about passwords.
Based on the password policy guide provided by organizations such as NIST (National Institute of Standards and Technology) and CIS (Center for Internet Security), I have picked up the points of password requirements and sorted them out.
Also, by examining account creation and documents on thirty-one websites, I have found out what kind of password requirements are actually set in those websites.
- ※Please be noted this is just only a reference due to insufficient number of the samples.
Please read it while imagining your passwords of the websites or systems you usually use.
By the way, the discussion of password requirements is just only a small part of the topic of user authentication, how to verify a user’s identity. Therefore, as long as the authentication is enhanced, it does not have to be a password and there are other authentication methods such as biometrics and one-time-passwords.
The goal of this blog is to give readers a chance to think about passwords, but ultimately, it is ideal to have them think about authentication, not just passwords. I am aiming to encourage readers to use this password discussion as a chance to put their thought into how to enhance your authentication with passwords and other authentication methods.
Password Requirements by Major Authorities
Table-1: Password Requirements Excerpted from CISPPG, NIST63B, and NISC Handbook
| CIS Password Policy Guide | NIST SP800-63 | NISC Handbook | |
|---|---|---|---|
| Minimum Length |
|
|
|
| Maximum Length | Unlimited | At least 64 characters (For user-created passwords) <Recommended> | Not defined |
| Available Character Type |
|
|
Total 88 types which are composed of uppercase/lowercase letters of alphabet, numbers, and 26 types of symbols |
| Required Character Type |
|
|
|
| Expiration |
|
|
|
| Other Requirements |
|
|
Password reuse, similar passwords, and passwords which can be inferred from personal information are not allowed |
Each of these guides may have a different intended reader. CISPPG is widely familiar regardless of whatever it is system developer or user. NIST63B describes the technical requirements for systems for federal agencies. However, as NIST SP800 is the de facto standard in the field of security, NIST63B is also for people involved in cybersecurity. NISC Handbook is for general users. Therefore, these comparisons may not make sense, so please simply take them as one way to think about passwords.
Minimum Password Length
As shown in table-1, 8 characters is the most common case of the minimum password length, and it seems to be in line with the general perception. However, please consider that both CIS and NIST have certain condition, such as “with/without Multi-Factor Authentication (MFA)” in CIS and “user-created password” in NIST.
As for my thoughts on the minimum length, although there is no clear reason why a typical password is minimum 8 characters, 8 characters has been the norm for a long time and there is a portability problem where 8 characters is the maximum length in legacy system. But meanwhile, it is also necessary to maintain the minimum strength of password, so as a compromise, 8 characters may be the minimum number. Also, I would say this can be supported by the fact that NISC Handbook which is for general users does not mention the minimum number of 8 characters, while CISPPG and NIST63B whose intended reader include developers and engineers set 8 characters as minimum.
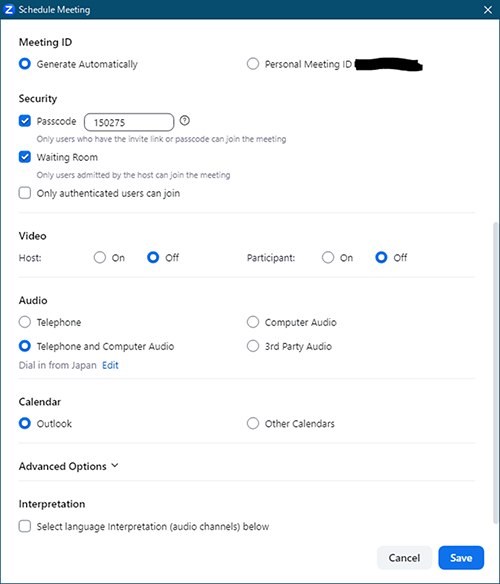
The term “for auto-generated passwords” in NIST63B refers to that the user uses a password generated by the system. It does not mean the password generated with password generator by the user. Zoom is a good example. As shown in Figure-1, when meeting schedule is set in Zoom, 6 characters passcode is automatically generated. This is exactly what the term “for auto-generated passwords” in NIST63B represents.
Maximum Password Length
For the maximum password length, CISPPG specifies “unlimited” and NIST63B does “at least 64 characters.” Since NISC Handbook is for general users, it is no wonder that it does not have a description. Basically, both CISPPG and NIST63B seem to have no limit on the maximum number.
Character Composition of Passwords
CISPPG and NIST63B represent both the characters which are available for passwords and the types of characters which should be included in passwords. NISC Handbook is for general users, so it represents only the types of characters which should be included in passwords.
- ※This is just an aside, but NIST63B also recommended Unicode characters and there were also real implementation
 [4].
[4].
Regarding password changes, they all have the same idea that immediate change is required when anything occurs such as password leakage.
For other requirements, I think the content of each guide is slightly different, but it seems common for all to avoid the passwords that are easy to guess.
Survey on Password Requirements
As mentioned above, a survey was conducted to find out what password requirements are actually set in thirty-one websites. There are three items to survey, the minimum length, the maximum length, and character composition. What investigated in the survey were the password requirements on the account creation screen of the website and the password policy published by the organization. The result is shown in Table-2.
- ※Please note that I only checked whether the password requirement is mentioned in the account creation screen, and did not create any accounts. Password policies should be determined by each organization and the content of this blog is not a condemnation of the organization’s password policy.
Table-2: Results of Survey on Password Requirements
| Website | Minimum Length | Maximum Length | Character Composition |
|---|---|---|---|
| A | 4 | 16 | Alphabets, numbers, and symbols |
| B | 6 | Unspecified | Unspecified |
| C | 6 | Unspecified | Alphabets and numbers |
| D | 6 | Unspecified | Alphabets, numbers, and symbols |
| E | 6 | 32 | Unspecified |
| F | 6 | 10 | Alphabets and numbers |
| G | 6 | Unspecified | Unspecified |
| H | 6 | Unspecified | Unspecified |
| I | 6 | 12 | Alphabets and numbers |
| J | 6 | 14 | Alphabets and numbers |
| K | 6 | 16 | Alphabets, numbers, and symbols |
| L | 6 | 11 | Alphabets and numbers |
| M | 6 | 20 | Alphabets, numbers, and symbols |
| N | 8 | Unspecified | Alphabets, numbers, and symbols |
| O | 8 | Unspecified | Uppercase/lowercase letters of alphabets and numbers |
| P | 8 | 60 | Uppercase/lowercase letters of alphabets, numbers, and symbols |
| Q | 8 | Unspecified | Uppercase/lowercase letters of alphabets and numbers |
| R | 8 | 20 | Alphabets and numbers |
| S | 8 | 20 | Other |
| T | 8 | 40 | Alphabets and numbers |
| U | 8 | 31 | Uppercase/lowercase letters of alphabets and numbers |
| V | 8 | 16 | Uppercase/lowercase letters of alphabets, numbers, and symbols |
| W | 8 | Unspecified | Uppercase/lowercase letters of alphabets and numbers |
| X | 8 | Unspecified | Unspecified |
| Y | 8 | Unspecified | Unspecified |
| Z | 12 | 60 | Uppercase/lowercase letters of alphabets, numbers, and symbols |
| AA | 15 | Unspecified | Other |
| AB | 10 | 20 | Uppercase/lowercase letters of alphabets, numbers, and symbols |
| AC | 10 | 18 | Other |
| AD | 12 | 16 | Uppercase/lowercase letters of alphabets, numbers, and symbols |
| AE | 12 | Unspecified | Other |
Minimum Length
Figure-2 shows the number of survey results of thirty-one websites by minimum password length.
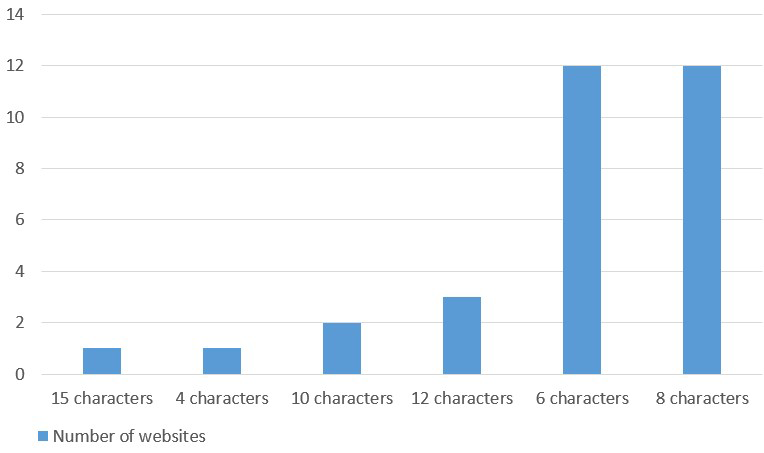
There are six patterns of the minimum password length which are 4, 6, 8, 10, 12, and 15 characters. Most of them are 6 and 8 characters and there seems to be few variations in this survey.
Regarding 8 characters, it is also in line with general perception and NIST63B requirements.
Regarding 6 characters, though NIST63B also describes minimum of 6 characters under the condition of “auto-generated password,” it did not apply in this case because it was different from NIST63B’s requirements. Possibly other guides set 6 characters as the minimum length, but it is not clear why they set it to 6 characters. Personally, I did not think 6 characters is common as the minimum length of passwords, but it may actually be common. However, 4 and 6 characters would be relatively vulnerable since they do not meet any requirements in the guides above.
Regarding 10 characters, it is in line with the requirements of NISC Handbook. There were two websites that set 10 characters and one of them conformed to NISC Handbook including the characters composition as well. Regarding 12 and 15 characters, they are stronger than the password requirements of NISC Handbook, even considering the character composition.
Now, consider not only the minimum length, but also the character composition. Table-3 shows how many websites conform to each guide if the password is created with only the minimum length and the required character composition for each website.
Table-3: Compliance with Each Guide Considering the Minimum Length and Character Composition of Thirty-one Websites
| CISPPG Compliant (Password Only) | CISPPG Compliant (with MFA) | NIST63B Compliant | NISC Handbook Compliant | Not Compliant with Any | |
|---|---|---|---|---|---|
| Number of Websites | 1 | 18 | 18 | 4 | 13 |
For CISPPG (with MFA) and NIST63B, 60% of all websites were appliable because the requirement for compliance is only a minimum length of 8 characters and MFA is not considered as it is not included in this survey. For CISPPG (password only) and NISC Handbook, only about 10% or less were compliant. Approximately 40% do not conform to the minimum level of any guide, which can be said to be vulnerable.
- ※In this blog, in examining the guide compliance and strength of passwords, CISPPG's character composition requirements (password only) "requires at least one non-alphabetic character" assumes the use of numbers.
Maximum Length
Figure-3 shows the number of survey results by maximum password length.
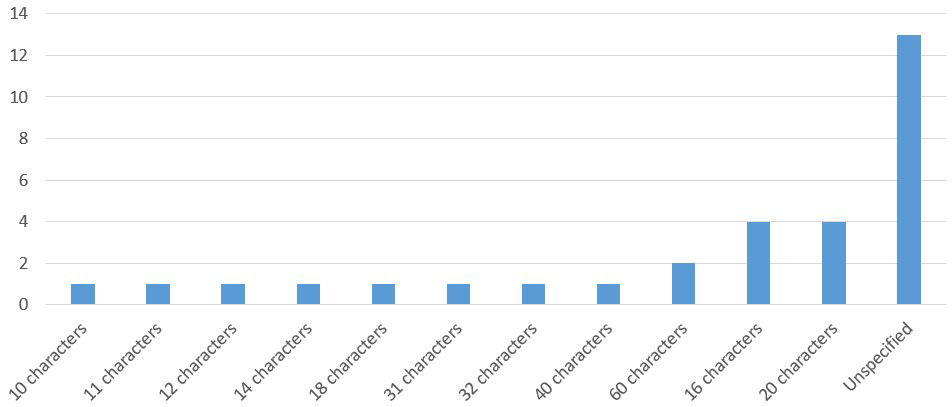
There is a variation in maximum length of passwords. Since it depends on the system specifications, it is difficult to consider the reason.
If there is no indication, it can be recognized as no limit, but in reality, there may be a systemic upper limit. Therefore, it cannot be considered as “no limit” unless there is a clear indication of “unlimited,” in which case it is listed as “unspecified.”
None of them meets the NIST63B requirement of “at least 64 characters” among those that the password length is specified.
In the same way as the minimum number of characters, Table-4 shows how many websites conform to each guide if the password is created with only the maximum length and the required character composition for each website.
Table-4: Compliance with Each Guide Considering the Maximum Length and Character Composition of Thirty-one Websites
| CISPPG Compliant (Password Only) | CISPPG Compliant (with MFA) | NIST63B Compliant | NISC Handbook Compliant | Not Compliant with Any | |
|---|---|---|---|---|---|
| Number of Websites | 28 | 31 | 31 | 29 | 0 |
Basically, most websites were compliant with each guide, but there were three websites which do not conform to CISPPG (password only) and two websites which do not conform to NISC Handbook.
Regarding NISC Handbook, all websites can conform if the character composition includes not only the required one but also uppercase and lowercase letters of alphabet, numbers, and symbols. However, there are still two websites which do not conform to CISPPG (password only) even if the character composition is increased. Thus, it is necessary to enable multi-factor authentication to conform to CISPPG with these websites.
Character Composition
Figure-4 shows the number of websites by the character composition of passwords.
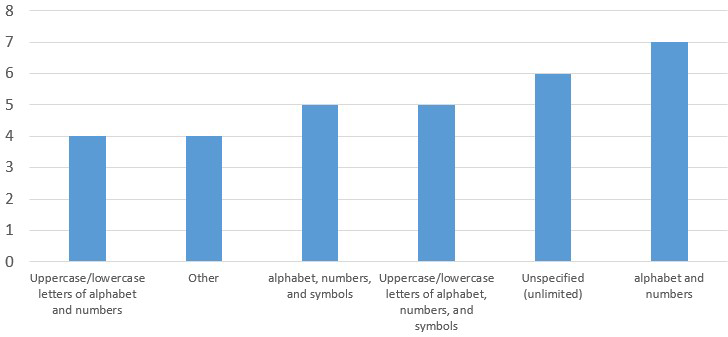
There were six patterns of character composition requirements which are “alphabets and numbers,” “unspecified (unlimited),” “uppercase/lowercase letters of alphabet, numbers, and symbols,” “alphabets, numbers, and symbols,” “other,” and “uppercase/lowercase letters of alphabet and numbers” in descending order. There seemed to be few variations.
“Other” is a choice format that the user chooses character types to use from several types, for example, “use three types from the four types of uppercase letters of alphabet, lowercase letters of alphabet, numbers, and symbols.” How many types to choose from and how many types to choose depends on the website.
Regarding “unspecified (unlimited),” “unspecified (unlimited)” is added because it was confirmed that some websites can accept account creation with numeric-only password without any errors.
Summary
What are your thoughts after reading this blog? Examining the actual survey results, my impression is that there is no uniformity in the requirements except for the minimum length. This may indicate that there is no correct answer to password requirements. After all, each organization and user should decide their own password policy by themselves.
For example, if an organization follows NIST63B whose requirements are relatively lax, they should not enforce the rules of the maximum length and character composition on users.
However, if an information leakage occurs due to a user’s weak password setting, the organization is also considered responsible  [5]
[5]  [6]. Therefore, it makes sense that a lot of organization try to make conditions for password registration. NIST63B specifies measures to prevent weak password settings such as password blacklisting.
[6]. Therefore, it makes sense that a lot of organization try to make conditions for password registration. NIST63B specifies measures to prevent weak password settings such as password blacklisting.
Having said that, it is not simple to take measures against password reuse. Even if a reused password is leaked from other organization, it is hard to notice it and deal with the problem. On the other hand, it has been pointed out that if the password requirements are too strict, users will only use similar passwords, so it is difficult to balance with the password requirements.
For those reasons, organizations set password requirements by balancing the costs and risks of continuity of their activity and sometimes consider using multi-factor authentication in addition to passwords.
From the user’s point of view, it is tempting to set a simple password for convenience, but considering the risk of password leakage, they should not set a simple password easily. However, complicated passwords are difficult to remember, and just like setting password requirements for an organization, setting a password requires a balance between cost and risk.
- ※Discussion of password management and how to create passwords are not considered at this time.
It is a good idea for users to start by following the relatively easy NISC Handbook. However, it is not necessary to stick to its condition of minimum 10 characters and character composition of “uppercase/lowercase letters of alphabet, numbers, and symbols.” If the strength of the password is equivalent, longer passwords with only alphabets and numbers can be also available option. Important thing is to set a workable password.
Following is what I would do if I were from the standpoint of each organization and user.
If I were in the position of an organization, it would change the action depending on the situation.
If the information (assets) that could be compromised through unauthorized logins is important and there is sufficient cost, I would comply to NIST63B password requirements and implement multi-factor authentication as well. As already mentioned, authentication is the essence, and it does not have to be a password if authentication is strong enough. Therefore, deploying multi-factor authentication together will enhance an authentication and reduce risks.
If the cost is not enough, the deployment of multi-factor authentication should be excluded from the options. And minimum length and character composition will be set to match CISPPG and the maximum length will be set to 64 characters according to the NIST63B. The reason for this is that it will be less convenient for users, but not enough to stop creating an account, and as the survey results show, few organizations set “at least 14 characters,” so it is unlikely that the password will be duplicated with other organizations.
In addition, if the information (assets) that could be compromised through unauthorized logins is not so important, password requirements would be complied with NIST63B, with user convenience rather than password strength.
Next, what if I were a user?
I would like to create passwords as I like since I understand the appropriate strength and other necessary factors. In that sense, I hope the maximum length of an ideal password is at least about 30 characters, and there are no character composition requirements. Also, it is better not to change the password regularly, which is troublesome.
Therefore, it would be ideal if the organization was in line with NIST63B.
Like in this way, I would like readers to be inspired to think about passwords.
I hope this blog will be useful to you and contribute to a safe and secure society.
References
- [1]
- [2]
- [3]
- [4]
- [5]
- [6]
Profile

Shun Miyazaki, CISSP Associate
Security Engineering Center, Security Implementation Technology Team
Shun Miyazaki works for promoting and streamlining secure development within the company.
He was awarded Grand Prix in the Hardening II SecurEach and Most Valuable Vendor in the Hardening II SU, competing in the ability to protect EC sites from cyber attacks and safeguard the business.